Crypto ransomware is the worst threat at present. There are a lot of variants in crypto ransomware. Only some make it into the limelight, while others fade away. In this article, you will get to know about Crypto Ransomware and how one can code it easily in order to encrypt certain directories and important files.
The reason for a possible increase in the use of crypto ransomware could be because coding it is quite easy compared to other malware. The malware just needs to browse through user directories to find relevant files that are likely to be personal and encrypt them. The malware author need not write complex code, such as writing hooks to steal data. Most crypto ransomwares don't care about hiding in the system, so most do not have rootkit components either. They only need to execute on the system once to encrypt all files. Some crypto ransomwares also check to see whether the system is already infected by other crypto ransomware.
There is a huge list of crypto ransomware. Here are a few of them:
- Locky
- Cerber
- CryptoLocker
- Petya
This article is an excerpt taken from the book, 'Preventing Ransomware' written by Abhijit Mohanta, Mounir Hahad, and Kumaraguru Velmurugan.
How does crypto ransomware work?
Crypto ransomware technically does the following things:
- Finds files on the local system. On a Windows machine, it can use the FindFirstFile(), FindNextFile() APIs to enumerate files directories.
- A lot of ransomware also search for files present on shared drives
- It next checks for the file extension that it needs to encrypt. Most have a hardcoded list of file extensions that the ransomware should encrypt. Even if it encrypts executables, it should not encrypt any of the system executables.
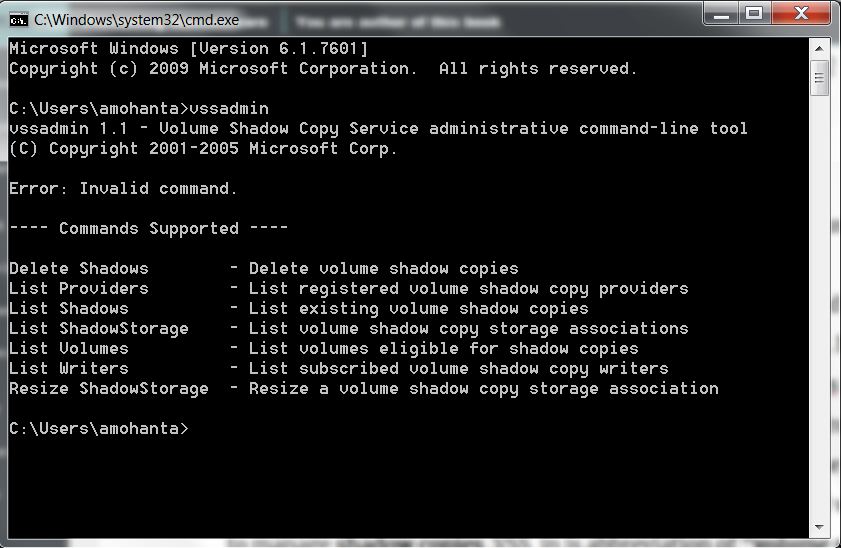
- It makes sure that you should not be able to restore the files from backup by deleting the backup. Sometimes, this is done by using the vssadmin tool. A lot of crypto ransomwares use the vssadmin command, provided by Windows to delete shadow copies. Shadow copies are backups of files and volumes. The vssadmin (vss administration) tool is used to manage shadow copies. VSS in is the abbreviation of volume shadow copy also termed as Volume Snapshot Service. The following is a screenshot of the vssadmin tool:
- After encrypting the files ransomware leaves a note for the victim. It is often termed a ransom note and is a message from the ransomware to the victim. It usually informs the victim that the files on his system have been encrypted and to decrypt them, he needs to pay a ransom. The ransom note instructs the victim on how to pay the ransom.
- The ransomware uses a few cryptographic techniques to encrypt files, communicate with the C&C server, and so on. We will explain this in an example in the next section. But before that, it's important to take a look at the basics of cryptography.
Overview of cryptography
A lot of cryptographic algorithms are used by malware today. Cryptography is a huge subject in itself and this section just gives a brief overview of cryptography. Malware can use cryptography for the following purposes:
- To obfuscate its own code so that antivirus or security researchers cannot identify the actual code easily.
- To communicate with its own C&C server, sometimes to send hidden commands across the network and sometimes to infiltrate and steal data
- To encrypt the files on the victim machine
A cryptographic system can have the following components:
- Plaintext
- Encryption key
- Ciphertext, which is the encrypted text
- Encryption algorithm, also called cipher
- Decryption algorithm
There are two types of cryptographic algorithms based on the kind of key used:
- Symmetric
- Asymmetric
Unlock access to the largest independent learning library in Tech for FREE!
Get unlimited access to 7500+ expert-authored eBooks and video courses covering every tech area you can think of.
Renews at £16.99/month. Cancel anytime
A few assumptions before explaining the algorithm: the sender is the person who sends the data after encrypting it and the receiver is the person who decrypts the data with a key.
Symmetric key
In symmetric key encryption, the same key is used by both sender and receiver, which is also called the secret key. The sender uses the key to encrypt the data while the receiver uses the same key to decrypt.
The following algorithms use a symmetric key:
- RC4
- AES
- DES
- 3DES
- BlowFish
Asymmetric key
A symmetric key is simpler to implement but it faces the problem of exchanging the keys in a secure manner. A public or asymmetric key has overcome the problem of key exchange by using a pair of keys: public and private. A public key can be distributed in an unsecured manner, while the private key is always kept with the owner secretly. Any one of the keys can be used to encrypt and the other can be used to decrypt:

Here, the most popular algorithms are:
- RSA
- Diffie Hellman
- ECC
- DSA
Secure protocols such as SSH have been implemented using public keys.
How does ransomware use cryptography?
Crypto ransomware started with simple symmetric key cryptography. But soon, researchers could decode these keys easily. So, they started using an asymmetric key. Ransomware of the current generation has started using both symmetric and asymmetric keys in a smart manner.
CryptoLocker is known to use both a symmetric key and an asymmetric key. Here is the encryption process used by CryptoLocker:
- When CryptoLocker infects a machine, it connects to its C&C and requests a public key.
- An RSA public and secret key pair is generated for that particular victim machine.
- The public key is sent to the victim machine but the secret key or private key is retained with the C&C server.
- The ransomware on the victim machine generates an AES symmetric key, which is used to encrypt files.
- After encrypting a file with AES key, CryptoLocker encrypts the AES key with the RSA public key obtained from C&C server.
- The encrypted AES key along with the encrypted file contents are written back to the original file in a specific format. So, in order to get the contents back, we need to decrypt the encrypted AES key, which can only be done using the private key present in the C&C server. This makes decryption close to impossible.
Analyzing crypto ransomware
The malware tools and concepts remain the same here too. Here are few observations while analyzing, specific to crypto ransomwares, that are different compared to other malware. Usually, crypto ransomware, if executed, does a large number of file modifications. You can see the changes in the filemon or procmon tools from Sysinternals
File extensions are changed in a lot of cases. In this case, it is changed to .scl. The extension will vary with different crypto ransomware.
A lot of the time, a file with a ransom note is present on the system. The following image shows a file with a ransom note:
Ransom notes are different for different kinds of ransomware. Ransom notes can be in HTML, PDF, or text files. The ransom note's file usually has decrypt instructions in the filename.
Prevention and removal techniques for crypto ransomware
In this case, prevention is better than cure. It's hard to decrypt the encrypted files in most cases. Security vendors came up with decryption tool to decrypt the ransomware encrypted files. There was a large increase in the number of ransomware and an increase in complexity of the encryption algorithms used by them. Hence, the decryption tools created by the ransomware vendors failed to cope sometimes.
http://www.thewindowsclub.com/list-ransomware-decryptor-tools gives you a list of tools meant to decrypt ransomware encrypted files. These tools may not work in all cases of ransomware encryption.
If you've enjoyed reading this post, do check out 'Preventing Ransomware' to have an end-to-end knowledge of the trending malware in the tech industry at present.
Top 5 cloud security threats to look out for in 2018
How cybersecurity can help us secure cyberspace
Cryptojacking is a growing cybersecurity threat, report warns
 United States
United States
 United Kingdom
United Kingdom
 India
India
 Germany
Germany
 France
France
 Canada
Canada
 Russia
Russia
 Spain
Spain
 Brazil
Brazil
 Australia
Australia
 Argentina
Argentina
 Austria
Austria
 Belgium
Belgium
 Bulgaria
Bulgaria
 Chile
Chile
 Colombia
Colombia
 Cyprus
Cyprus
 Czechia
Czechia
 Denmark
Denmark
 Ecuador
Ecuador
 Egypt
Egypt
 Estonia
Estonia
 Finland
Finland
 Greece
Greece
 Hungary
Hungary
 Indonesia
Indonesia
 Ireland
Ireland
 Italy
Italy
 Japan
Japan
 Latvia
Latvia
 Lithuania
Lithuania
 Luxembourg
Luxembourg
 Malaysia
Malaysia
 Malta
Malta
 Mexico
Mexico
 Netherlands
Netherlands
 New Zealand
New Zealand
 Norway
Norway
 Philippines
Philippines
 Poland
Poland
 Portugal
Portugal
 Romania
Romania
 Singapore
Singapore
 Slovakia
Slovakia
 Slovenia
Slovenia
 South Africa
South Africa
 South Korea
South Korea
 Sweden
Sweden
 Switzerland
Switzerland
 Taiwan
Taiwan
 Thailand
Thailand
 Turkey
Turkey
 Ukraine
Ukraine



 Here, the most popular algorithms are:
Here, the most popular algorithms are:










