Signing in with a Google account
Have you ever found an interesting web service but closed the browser page as soon as you realized you’d need to go through the entire registration process to use it? On the other hand, if the service offers single-click sign-up options, such as using your Google or Facebook account, you’re more likely to continue using it, right?
Signing in and signing up are among the first actions your app users will take, so it’s important to make this process as easy as possible by offering social identity authentication options.
In this recipe, we’ll implement Google-based authentication. We’ll add an endpoint to ASP.NET Core Identity that will start a Google authentication flow and create a new user if they haven’t registered before. Additionally, we’ll develop the client-side UI for user authentication in our .NET MAUI app.
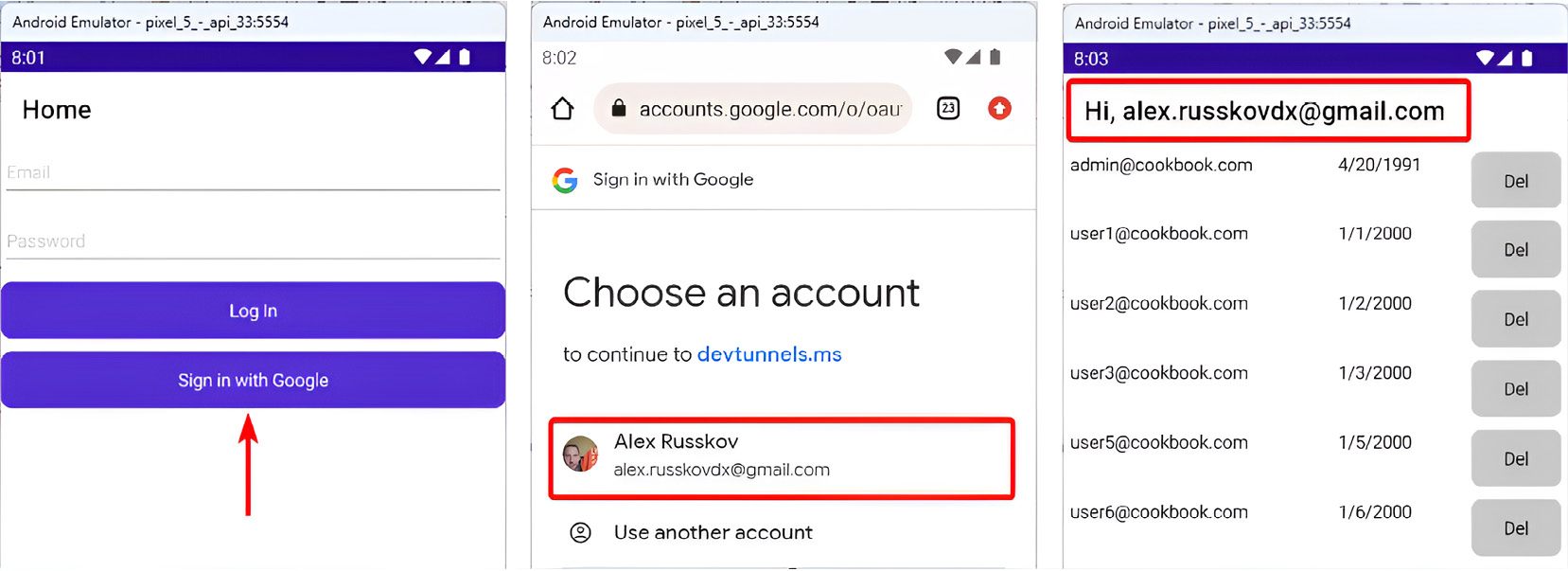
Figure 5.17 – Google sign-in





















































