In a RedTeam activity, we may often find more networks which are further accessible from one of the internal systems. In our case, this was the 172.19.4.0/24 network. Multi-level pivoting occurs when we achieve further access into a different subnet. Let's look at an example of this:
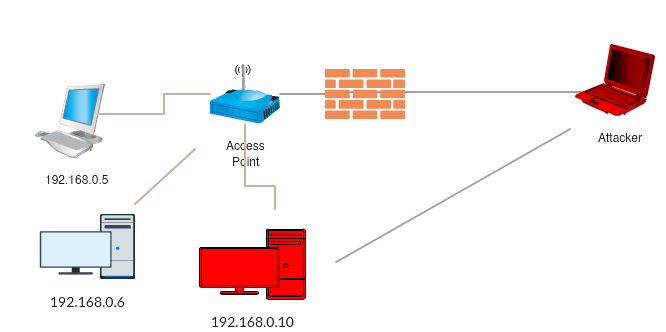
In the preceding diagram, the attacker exploits the network and sets up a pivot on 192.168.0.10 to gain further visibility into the internal network. Upon doing more recon, the attacker comes across a system that has two NICs:

Once the attacker gains access to 192.168.0.11, they can then add a pivot again which will allow them access to 172.4.19.0 subnet. This is known as multi-level pivoting. The following diagram explains this:

As explained previously, we found a system in the 172.4.19.0 system which has another IP assigned to it. We exploited that system and added a...












































































