Application- and protocol-aware technologies
Some applications will benefit from dedicated security appliances/services operating on sole behalf of those applications. Imagine you wanted to protect your web application server from typical exploits, including cross-site scripting (XSS), cross-site request forgery (XSRF), and Structured Query Language (SQL) injection. In that case, you would not want to filter all traffic for these exploits using the network firewall; it would have a huge workload and would slow down traffic for the entire network. Application-aware security appliances process traffic only being forwarded to that service.
The types of security applications that inspect and apply rulesets to application layer traffic are said to be using DPI.
It is important to plan for the placement of these devices to ensure traffic can be inspected before entering or leaving the network and to also minimize latency or delay where inspection and filtering are not required.
In the following section, we will take a look at some examples of application- and protocol-aware security solutions.
DLP
We must ensure the enterprise does not breach legal or regulatory compliance by exfiltration of sensitive data, either knowingly or unknowingly. It is important that intellectual property and customer data are protected, even when compliance is not a factor. Physical restrictions and/or enforceable policy may be used to block data exfiltration to a removable storage medium. DLP can also be implemented on the edge of the network, or as part of a cloud solution. Microsoft is one of many providers offering DLP as part of the Cloud Access Security Broker (CASB) security suite. In the following screenshot, we are selecting built-in rules to block the exfiltration of financial data:

Figure 1.14 – Microsoft 365 DLP rule
There are many built-in templates for regulated industries.
WAF
A WAF is defined as a security solution on the web application level. It allows for HyperText Transfer Protocol/HTTP Secure (HTTP/HTTPS) traffic to be inspected for anomalies without slowing down the rest of the network traffic. A WAF can be implemented as an appliance, plugin, or filter that applies a set of rules to an HTTP connection.
A WAF helps prevent attacks, such as the following:
- SQL injection attacks
- XSS attacks
- Malicious file execution
- CSRF attacks
- Information leakage
- Broken authentication
- Insecure communications
A WAF can also provide URL encryption and site usage enforcement, as illustrated in the following diagram:
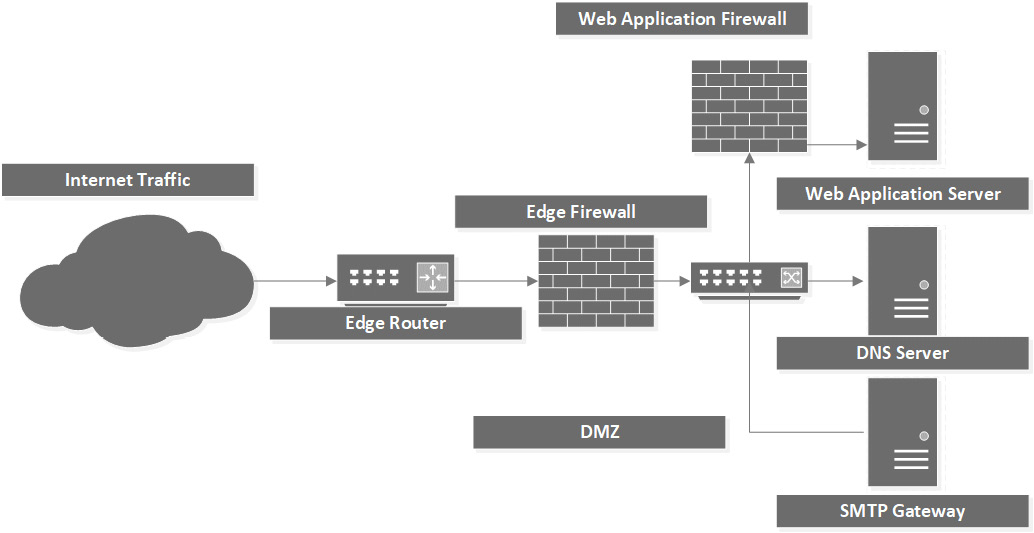
Figure 1.15 – WAF
Advantages
A WAF has the following advantages:
- Allows for the creation of custom rules
- Monitors and blocks malicious traffic
- Can prevent live attacks
- Protects vulnerable web applications
Disadvantages
A WAF has the following disadvantages:
- May slow web traffic
- Could block legitimate traffic
- Requires frequent tuning
Database activity monitoring
Database activity monitoring (DAM) tools monitor, capture, and record database activity in near real time and can generate alerts when rules are violated.
DAM can be accomplished by doing the following:
- Network sniffing
- Reading of database logs
- Memory analysis
DAM tools can correlate data and provide the administrator with the tools to detect anomalous database activity and capture a log of events, should this be required for forensics.
As a database is often a critical line-of-business (LOB) solution, often hosting enterprise resource planning (ERP), customer relationship management (CRM), sales order processing, and so on, investing in this additional technology will be worth the cost.
Spam filter
A spam filter typically scans incoming emails to protect your employees from email-borne threats. It can also scan emails leaving the organization (although this is more likely taken care of by a DLP solution). It can be deployed on the demilitarized zone (DMZ) network, filtering incoming SMTP traffic, and will typically perform additional tasks such as querying Spamhaus Block List (SBL) providers, such as Spamhaus, to drop connections from verified blocked domain names or IP addresses.
Many organizations will deploy this service in a cloud deployment, especially if the ISP hosts the email servers.
The following section covers some of the additional considerations to allow for secure remote working and administration.

































































