Cloud native security patterns
Now that we have a broad understanding of the native security tools available to us in the cloud, we can dive into some examples of how to design and build common deployments. It is important to realize that each use case will not leverage all security tools and will not exactly match other security patterns. We aim to demonstrate a palette of different approaches to varying problems and give the reader the ability to select and combine different solutions.
As our first example, let's consider a three-tier web application:
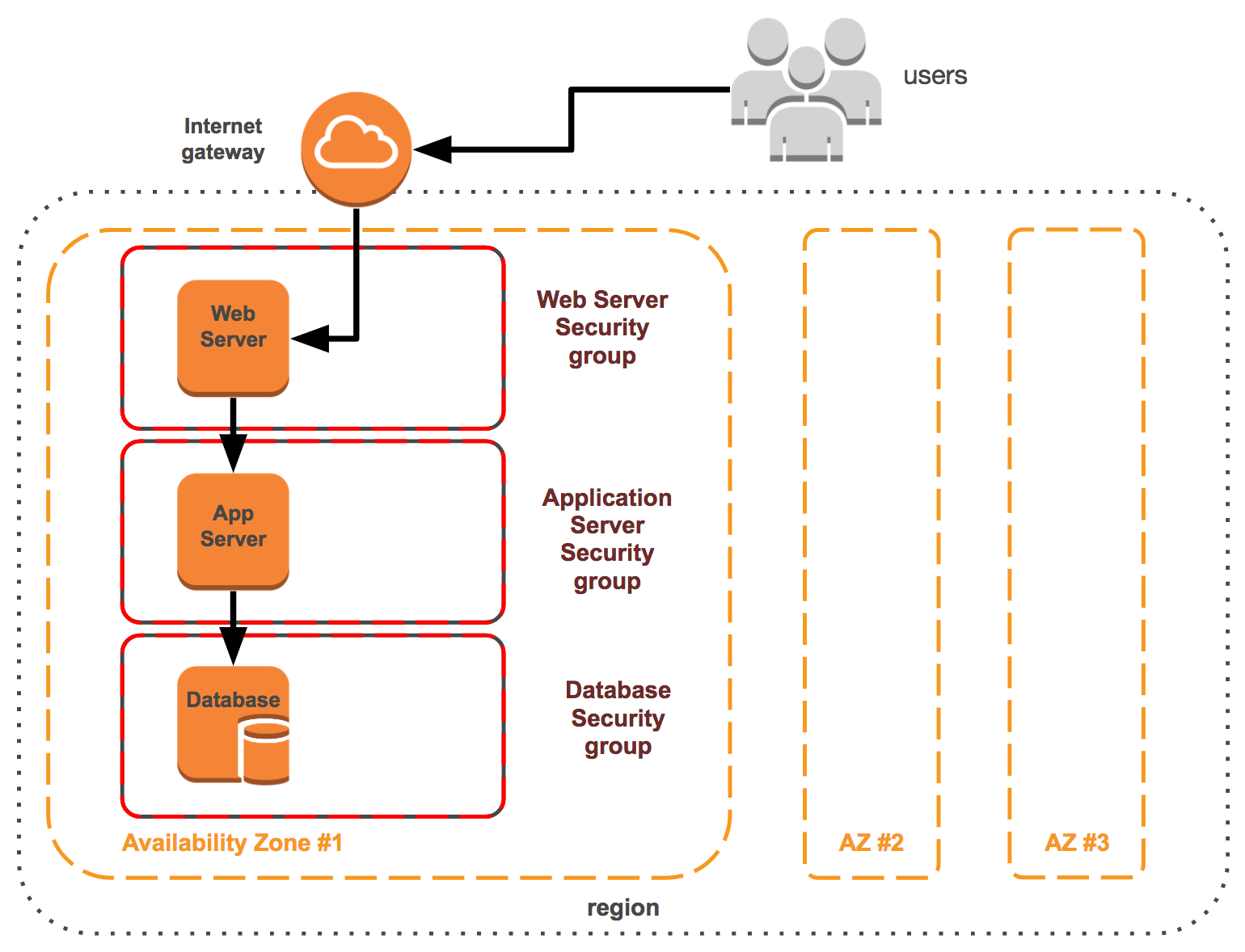
Figure 6.3
Security groups should be used to separate tiers within a stack, as shown in the previous diagram of a three-tier web application. Each tier has its own security group, which has unique rules that expose minimal attack vectors.
For our first security pattern example, let's use a basic three-tier web application. The 3 tiers comprising this pattern are the web, application, and database. A user routing from the internet will not directly...



























































