User authentication
Now that you know everything about users and the information that is stored about them, let's look at how to authenticate them with Moodle. So far, we have only dealt with manual accounts, which are activated by default after the installation of Moodle.
Moodle supports a significant number of authentication types. Furthermore, Moodle supports multi-authentication, that is, concurrent authentication from different authentication sources. For example, your organization might use an LDAP server containing user information for all your full-time students and staff, but it wishes to manage part-time users manually.
Remember the basic authentication workflow we looked at in Chapter 3, Courses, Users, and Roles. Now, we can have a look at a more complete picture, as shown in the following diagram:
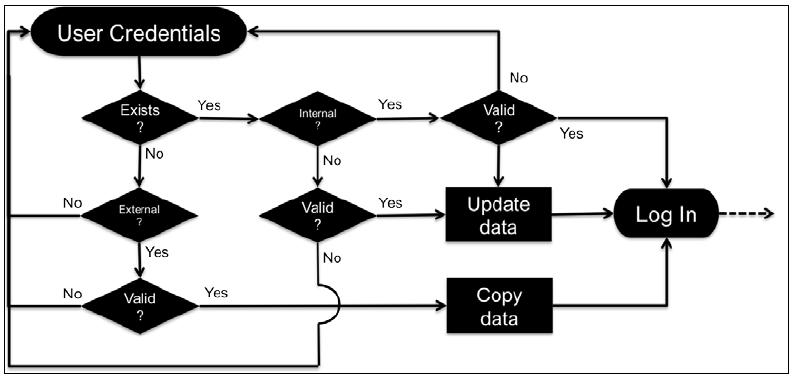
Let's start at the top where the user enters their user credentials, that is, username and password. Bear in mind that this could take place automatically, for example, in a single sign...
























































