A primer on cybersecurity domains and the NIST CSF
There are many, many ways to think about cybersecurity domains and this could very well be a book in itself. The purpose of this section is to provide an overview of common cybersecurity domains and what they entail.
For the sake of simplicity and aligning it with a common industry standard, this section is aligned with the NIST CSF.
The NIST CSF divides the cybersecurity domain into five main categories, namely, Identify, Protect, Detect, Respond, and Recover:
- Identify: There is an old saying in the cybersecurity world – You cannot protect what you do not know exists. The Identify category of the CSF emphasizes developing the organization’s understanding to manage cybersecurity risk to systems, assets (including people), data, and the capabilities to do so.
This activity is important for prioritizing the organization’s efforts and resources in consistency with its overall risk management strategy and business goals. This function stresses the importance of understanding the business context, the resources that support critical functions, and the related cybersecurity risks. The activities in Identify include the following:
- Identification of physical, software, and people assets to establish the basis of an asset management program
- Identification of established cybersecurity policies to define the governance program, as well as identifying legal and regulatory requirements regarding the cybersecurity capabilities of the organization
- Identification of the organization’s business environment and critical systems, including the role of critical vendors in the supply chain
- Identification of asset vulnerabilities, threats to internal and external organizational resources, and risk response activities to assess risk
- Implementation of a risk management strategy, including identifying risk appetite and tolerance
- Identification of vendor risk management strategy, including priorities, constraints, risk tolerances, and assumptions used to support risk decisions associated with managing supply chain risks
- Protect: Once the assets and critical processes have been identified, the appropriate safeguards (controls) must be developed and implemented to ensure the delivery of critical infrastructure services. This function is dedicated to identifying controls that outline appropriate safeguards to ensure the delivery of critical infrastructure services and supports the ability to limit or contain the impact of a potential cybersecurity event. The activities in Protect can be seen here:
- Perform security awareness training for all staff and additional role-based and privileged user training.
- Implement protections for identity management and access control within the organization, including physical and remote access. In the case of an external data center or using cloud services, implement robust controls such as complex passwords, the use of VPNs, and multi-factor authentication.
- Establish data security protection consistent with the organization’s risk strategy and criticality of assets to protect the confidentiality, integrity, and availability of information.
- Implement processes and procedures to maintain and manage the protection of information systems and assets.
- Protect organizational resources through maintenance, including remote maintenance activities.
- Manage technology to ensure the security and resilience of systems, consistent with organizational policies, procedures, and agreements.
- Detect: Proactively detecting and deterring potential cybersecurity incidents is critical to a robust information security program. This function defines the appropriate activities to proactively identify the occurrence of a cybersecurity event and involve the relevant teams as soon as the threat vectors are identified. The activities in Detect can be seen in the following list:
- Detect anomalies across all system events and act on them before they cause substantial harm to the assets
- Implement tools for continuous monitoring and detection (also known as the Security Operations Centre) to monitor critical events, tune the systems to reduce false positives, and gauge the effectiveness of protective measures, including network and physical activities
- Respond: Once an event has indeed materialized and caused the incident, the organization should be prepared to contain and respond using manual as well as automated processes. This function aims to develop such systems, train the staff on incident response, and ensure that incidents can be resolved within the agreed timeframe and with minimum disruption to the system. The activities in Respond include the following:
- Manage communications with internal and external stakeholders during and after an event
- Analyze the incident to ensure effective response and supporting recovery activities including forensic analysis and determining the impact of incidents
- Ensure incident response planning processes are agreed upon with relevant staff, executed at the time of the incident, and lessons learned are improved to prevent the incident in the future
- Perform mitigation activities to prevent the expansion of an event and to resolve the incident
- Implement improvements by incorporating lessons learned from such responses and ensure the staff is trained on the new practices
- Recover: This function identifies appropriate activities to renew and maintain plans for resilience and to restore any capabilities or services that were impaired due to a cybersecurity incident. The activities in Recover can be seen here:
- Ensure that the organization has a recovery plan process in place that is tested within an acceptable time frame and that procedures to restore systems and/or assets affected by cybersecurity incidents are in place
- Implement the lessons learned while responding to incidents and review those with relevant stakeholders
- Internal and external communications are coordinated during and following the recovery from a cybersecurity incident, and new areas of risk are continuously added and acted upon
The following figure summarizes the NIST CSF functions:
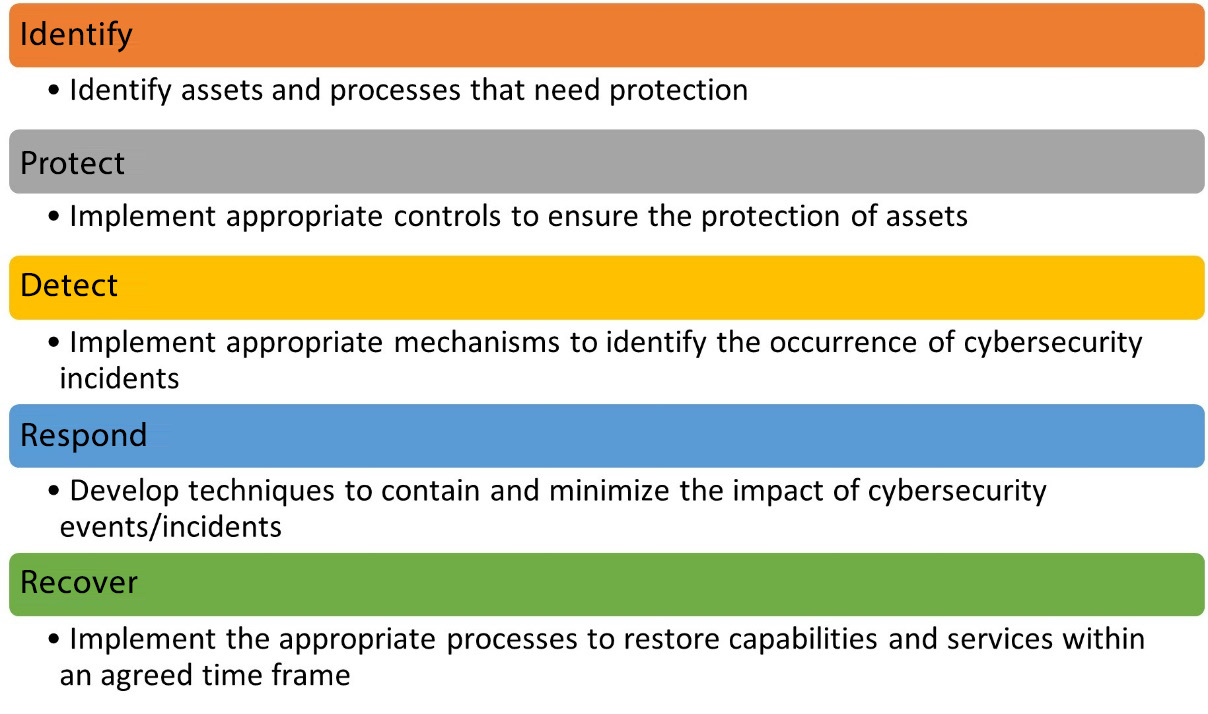
Figure 1.3 – Simplified NIST CSF functions
Each of these domains is further segregated into multiple subdomains that are outside the scope of this book. I highly encourage you to familiarize yourself with the NIST CSF subdomains and their relationship with COBIT.
Important note
COBIT has custom frameworks for several specific use cases, including a framework for implementing the NIST CSF. A set of such publications can be found on the ISACA website at https://www.isaca.org/resources/cobit.
























































