Implementing Conditional Access policies
There must be a balance of protecting an organization’s resources while ensuring every user, wherever they are, is empowered to be productive whenever.
To further strengthen our Azure AD identities, we can use insights from identity-driven signal data to make informed access control decisions and then use those decisions to enforce access policies.
MFA works alongside Conditional Access to provide further granular control of access.
Conditional Access is based on an IF/THEN approach. This approach means that IF signal information collected from the sign-in process matches certain criteria, THEN decisions are made based on the information as to whether access will be allowed or blocked.
Conditional Access will also determine whether the user will be required to perform additional authentication methods or take other actions, such as resetting their password. This is represented in the following diagram:
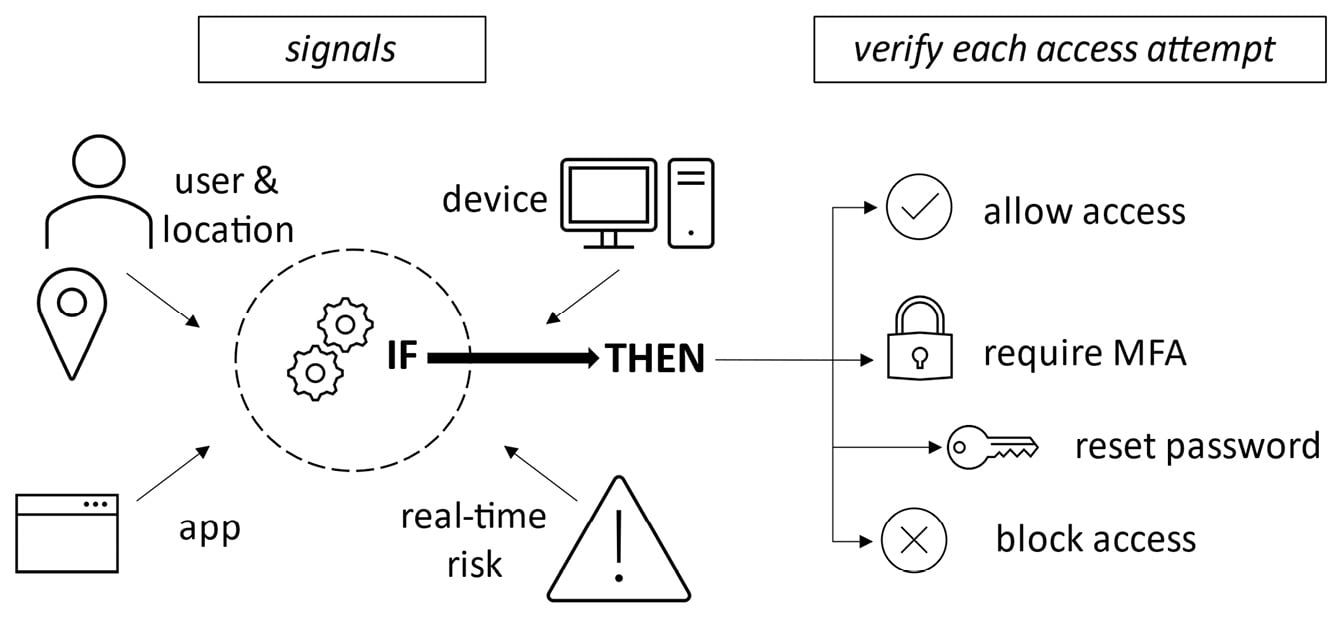
Figure 1.29 – Conditional Access concept
The following are some common Conditional Access policies:
- Require MFA for all users
- Require MFA for Microsoft portals/services access
- Require password reset for risky users
- Block the use of legacy authentication protocols
- Require hybrid-joined or compliant devices
- Allow or deny from specific locations
This recipe will teach you how to implement Conditional Access policies in your environment’s AD tenancy. We will take you through enabling conditional access policies and configuring them to restrict user access to apps based on if a set of conditions have been met.
Getting ready
This recipe requires the following:
- A device with a browser, such as Edge or Chrome, to access the Azure portal: https://portal.azure.com.
- You should sign into the Azure portal with an account with the Global Administrator role.
- You will require Azure AD Premium licenses or trial licenses.
- If you have Security Defaults enabled, you will automatically have MFA enabled for all users and administrators using the free benefits of Azure AD. Using one of the paid Azure AD Premium licenses provides additional capabilities such as the additional authentication methods of verification codes, text messages, or phone calls, as well as the following:
- Azure AD Premium P1: This license includes Azure Conditional Access for MFA
- Azure AD Premium P2: This license adds risk-based Conditional access to MFA
How to do it…
This recipe consists of the following task:
- Configuring Conditional Access
Task – configuring Conditional Access
Perform the following steps:
- From the Azure portal, go to Azure Active Directory, click Security in the Manage section from the side menu, and then click Conditional Access in the Protect section.
- Click + New Policy from the top toolbar in the Conditional Access Policies blade:
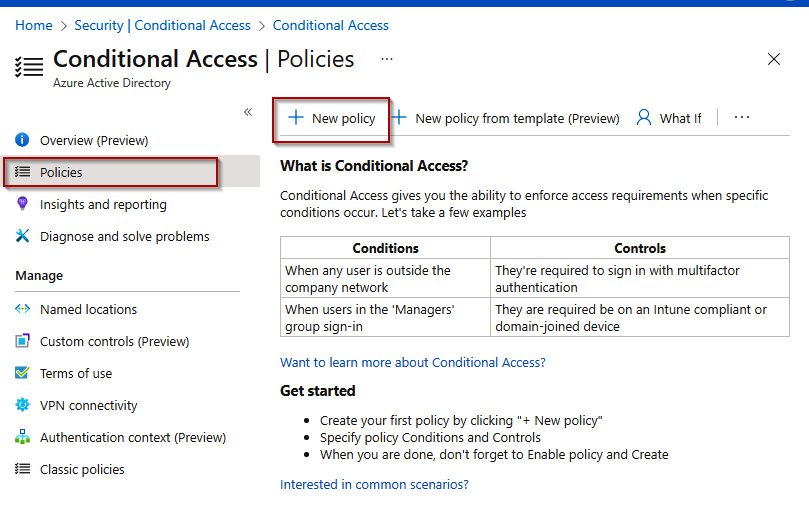
Figure 1.30 – Conditional Access | Policies
- Select a Name for your policy from the New conditional access policy blade.
- From the Assignments section, select which users and groups this policy will apply to:
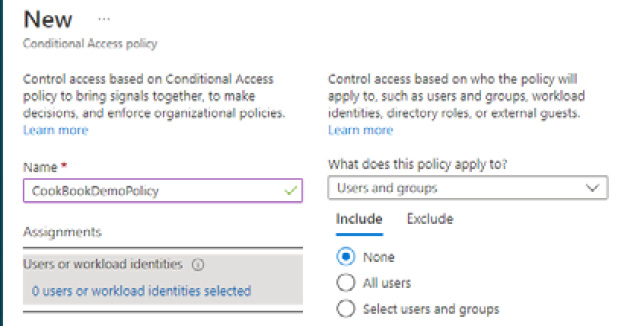
Figure 1.31 – User settings
- From the Cloud apps or actions section, select whether this policy will apply to Cloud apps or Actions; we will select Cloud apps:
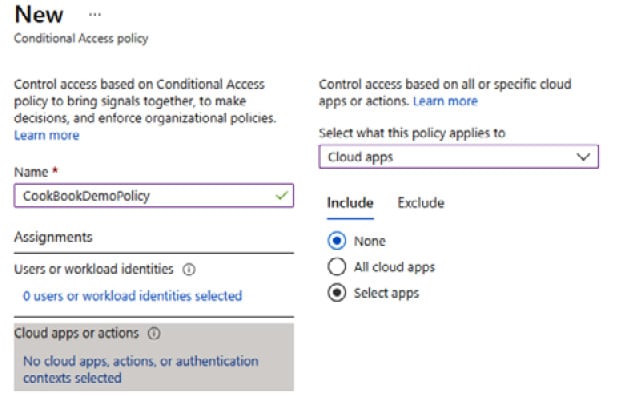
Figure 1.32 – Apps setting
- From the Include tab, we will click Select apps, search for Azure Management, tick the check box next to Microsoft Azure Management app in the list, and click Select. Note the warning dialog box about not locking yourself out:
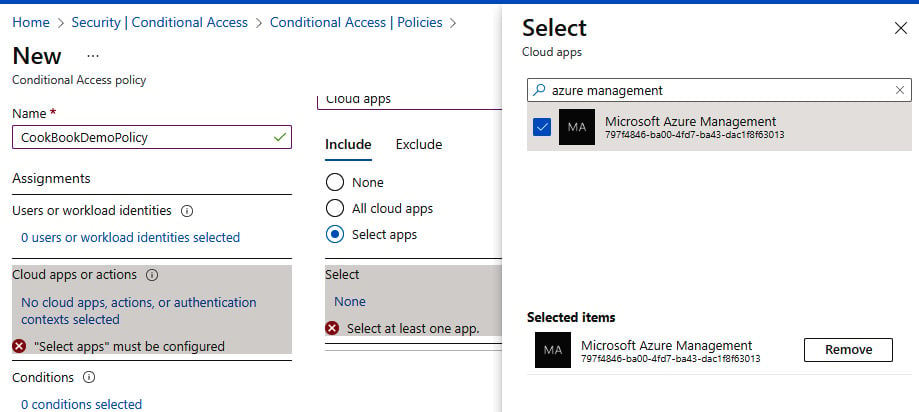
Figure 1.33 – App selection
- Click the Conditions settings, set any required conditions, or leave it unconfigured:
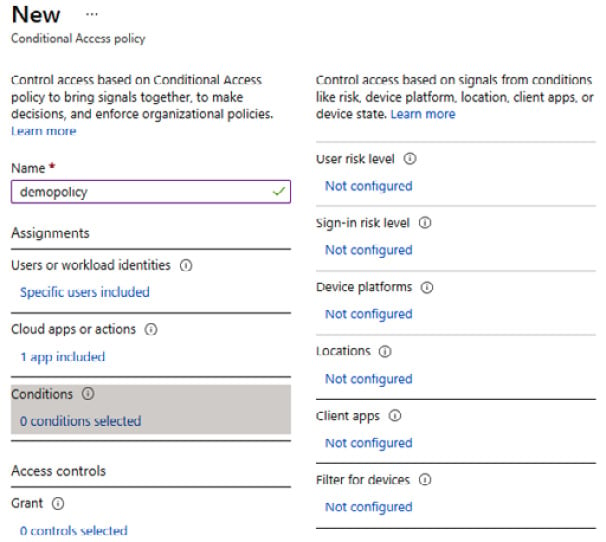
Figure 1.34 – Conditions settings
- From Grant, under the Access controls section, click on 0 controls selected, set it to Grant access, tick Require multifactor authentication, and then click Select:
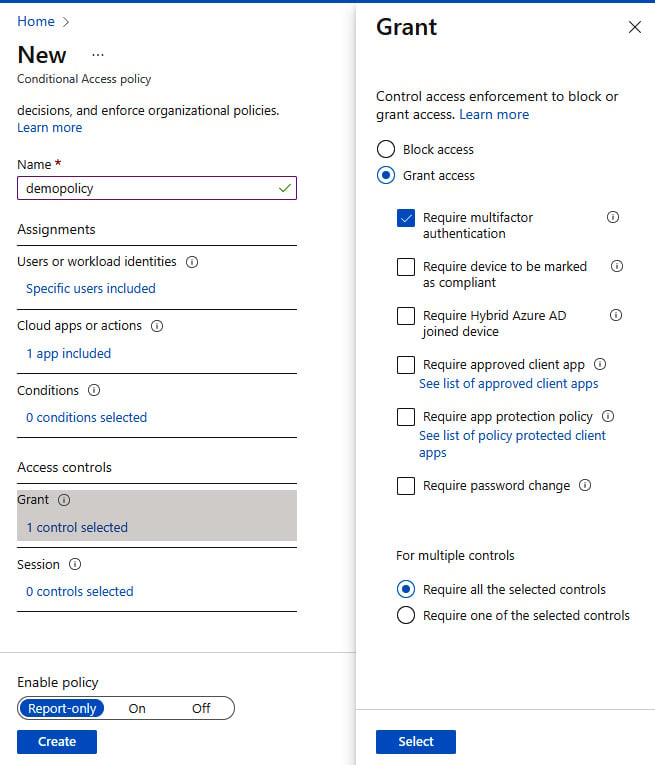
Figure 1.35 – Access settings
- In the Enable policy section, leave it set to Report-only, then click Create.
- Your policy will now appear in the policies list:
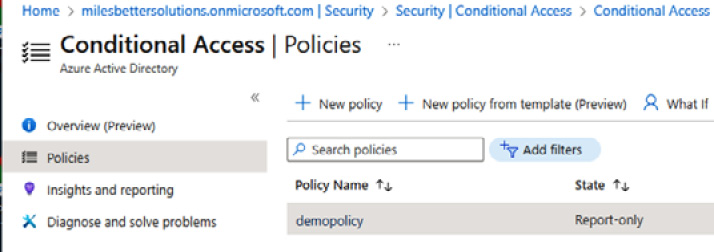
Figure 1.36 – Access policies list
With that, you have configured Conditional Access. This concludes the hands-on tasks for this recipe.
How it works…
In this recipe, we looked at how we can implement Conditional Access policies in addition to MFA to layer on an additional layer of defense while maintaining the users’ productivity needs.
We configured a Conditional Access policy to a set of selected users (or groups) that required MFA when they accessed the Azure portal; this was enabled by selecting the Microsoft Azure Management app.
See also
Should you require further information, you can refer to the following Microsoft Learn articles:
- What is Conditional Access?: https://learn.microsoft.com/en-us/azure/active-directory/conditional-access/overview
- Azure AD Conditional Access documentation: https://learn.microsoft.com/en-us/azure/active-directory/conditional-access
- Conditional Access: Cloud apps, actions, and authentication context: https://learn.microsoft.com/en-us/azure/active-directory/conditional-access/concept-conditional-access-cloud-apps
- Azure Active Directory fundamentals documentation: https://learn.microsoft.com/en-us/azure/active-directory/fundamentals

























































