Living in today's digital world
Today, we are more reliant on technology than ever and live in a world where businesses cannot survive without it. As our younger generations grow up, there is greater demand for the use of advanced technology. One scary thought is how fast the world has grown within the previous 100 years compared to the overall history of mankind. Technology continues to push the boundaries of innovation, and a significant portion of that change must include the securing of this technology. Especially since the world has become a more connected place with the advancement of the internet.
To give you a rough idea of technology usage today, let's take a look at the current desktop usage throughout the world. For these statistics, we will reference an online service, called Statcounter GlobalStats: https://gs.statcounter.com/. This dataset is not all-inclusive, but there is a very large sampling of data used to give us a good idea of worldwide usage. Statcounter GlobalStats collects its data through web analytics via tracking code on over 2 million websites globally. The aggregation of this data equates to more than 10 billion page views per month. The following screenshot shows the OS market share that is in use worldwide. More information from Statcounter can be viewed at https://gs.statcounter.com/os-market-share/desktop/worldwide:

Figure 1.1 – Statcounter Desktop Operating System Market Share Worldwide
As you can see, the Windows desktop market is more widely adopted than any other OS available today. Seemingly, Windows has always had negative connotations because of its ongoing vulnerabilities in comparison to other OSes. Part of this is due to how widely used Windows actually is. A hacker isn't going to waste their time on an OS that isn't widely adopted. We can assume there would be a direct correlation between OS adoption rates and available security vulnerabilities. Additionally, the Windows OS is supported across many types of hardware, which opens up opportunities for exploits to be developed. One reason as to why we see significantly fewer macOS vulnerabilities is due to the hardware control with which Apple allows its software to run. As the platform has grown, though, we have seen an increase of vulnerabilities within its OS too. The point we're making is that we tend to focus our efforts on areas where it makes sense, and Windows has continued to be a leader in the desktop space, making it a very attractive source to be attacked. This, in turn, has created an ecosystem of vendors and products over the years, all aimed at helping to protect and secure Windows' systems.
Let's take a look at the current adoption of the different Windows OSes in use. The following screenshot from Statcounter shows the current Windows desktop version usage around the world today. To view these statistics, visit https://gs.statcounter.com/os-version-market-share/windows/desktop/worldwide:

Figure 1.2 – Desktop Windows Version Market Share Worldwide
As you can see, Windows 10 has become the most adopted OS. Microsoft continues to push more users and organizations to Windows 10, and this is where they spend the majority of their development resources. There are also major changes to Windows 10 compared to older versions, which is why it is critical to migrate from older versions, especially for security-specific reasons. Microsoft ended its support (including security updates) for Windows XP in April 2014 and Windows 7 in January 2020.
NetMarketShare is another analytical site similar to Statcounter GlobalStats with its own set of statistics for reference: https://netmarketshare.com/.
A recent buzz term you have most likely heard in recent years is that of digital transformation. This refers to the shift from a legacy on-premises infrastructure to a modernized cloud-first strategy to support the evolving need of big data, machine learning, Artificial Intelligence (AI), and more. A significant part of this shift also falls within Windows systems and management. In Chapter 3, Server Infrastructure Management, we will look at the differences between a data center and a cloud model, including where the responsibilities fall for maintaining and securing underlying systems. Prior to digital transformation, we relied heavily on the four walls of the corporation and its network to protect a data center and its systems. This included a requirement for client devices to be physically on the corporate network in order to access data and services. With this model, our devices were a little easier to manage and lock down, as they never left the corporate office. Today, the dynamics have changed, and, referencing back to Statcounter in the following screenshot, you can see a significant shift from traditional desktop usage to a more mobile experience and requirement. To view the source of this diagram, visit https://gs.statcounter.com/platform-market-share/desktop-mobile-tablet/worldwide/#monthly-200901-202003:
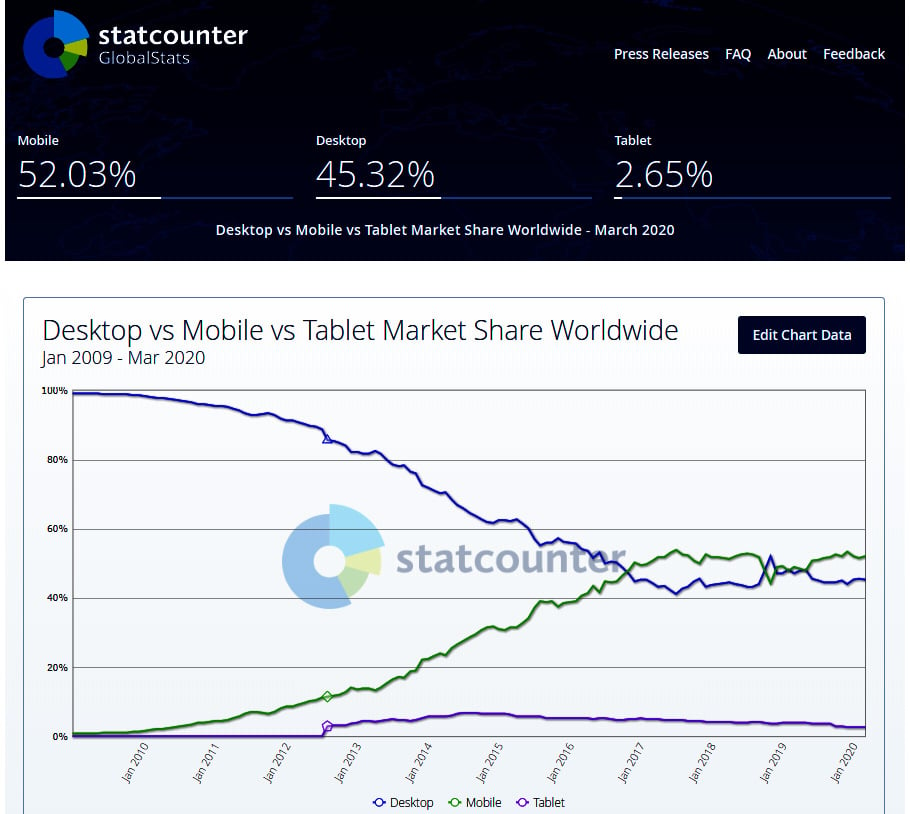
Figure 1.3 – Statcounter platform comparison Jan 2009 – Mar 2020
Focusing on Windows security, the traditional model of an organization would have typically included the following security tools as part of its baseline:
- AV (antivirus software)
- Windows Firewall
- Internet proxy service
- Windows updates
Depending on your organization or industry, there may have been additional tools. However, for the most part, I'd imagine the preceding list was the extent of most organizations' security tools on Windows client devices. The same would have most likely applied to the Windows servers in the traditional model. As this digital transformation has brought change, the traditional method of Windows management has become a legacy. There is an expectation that we can work and access data from anywhere at any time. We live in an internet-connected world, and, when we plug our device in, we expect to access our data with ease. With this shift, there is a major change in the security of the systems we manage and, specifically, the Windows server and client. As we shift our infrastructure to the cloud and enable our users to become less restricted, the focus of security revolves not only around the device itself but that of the user's identity and, more importantly, the data. Today, the items that we listed earlier will not suffice. The following tools are those that would be needed to better protect your Windows devices:
- Advanced Threat Protection (ATP): AV and threat protection, advanced analytics and behavioral monitoring, network protection, exploit protection, and more
- Advanced data loss prevention
- Information protection
- Identity protection: biometric technology, multi-factor authentication, and more
- Application control
- Machine learning and advanced AI security services




























































