1. Lab Environment Overview
When performing dynamic analysis, you will be executing the malware specimen, so you need to have a safe and secure lab environment to prevent your production system from being infected. To demonstrate the concepts, I will be using the isolated lab environment that was configured in Chapter 1, Introduction to Malware Analysis. The following diagram shows the lab environment that will be used to perform dynamic analysis and the same lab architecture is used throughout the book:
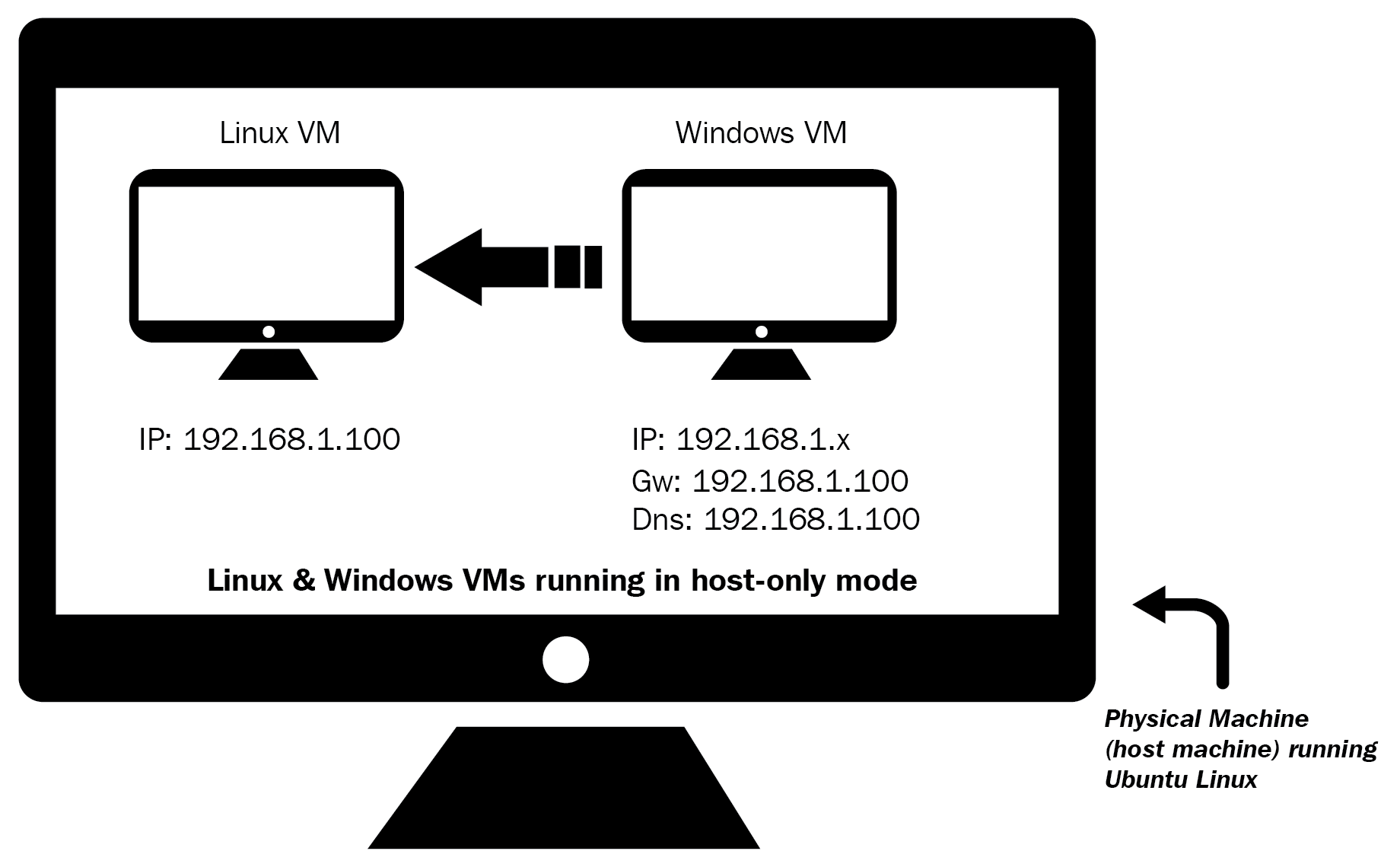
In this setup, both the Linux and Windows VM were configured to use the host-only network configuration mode. The Linux VM was preconfigured to an IP address of 192.168.1.100, and the IP address of the Windows VM was set to 192.168.1.50. The default gateway and the DNS of the Windows VM were set to the IP address of the Linux VM (192.168.1.100), so all the Windows network traffic is routed through the Linux VM.
The Windows VM will be used to execute the malware sample during analysis, and...

































































