To further increase the availability of the attack surface on the Windows operating system, it is important to add vulnerable software and enable or disable certain integrated components.
Increasing the Windows attack surface
Getting ready
Prior to modifying the configurations in Windows to increase the attack surface, you will need to have the operating system installed on one of your virtual machines. If this has not been done already, refer to the previous recipe.
How to do it...
Now, follow these steps to make Windows XP more vulnerable:
- Enabling remote services, especially unpatched remote services, is usually an effective way of introducing some vulnerabilities into a system. First, you'll want to enable Simple Network Management Protocol (SNMP) on your Windows system. To do this, open the Start menu in the bottom-left corner and then click on Control Panel. Double-click on the Add or Remove Programs icon, and then click on the Add/Remove Windows Components link on the left-hand side of the screen to get the following screen:
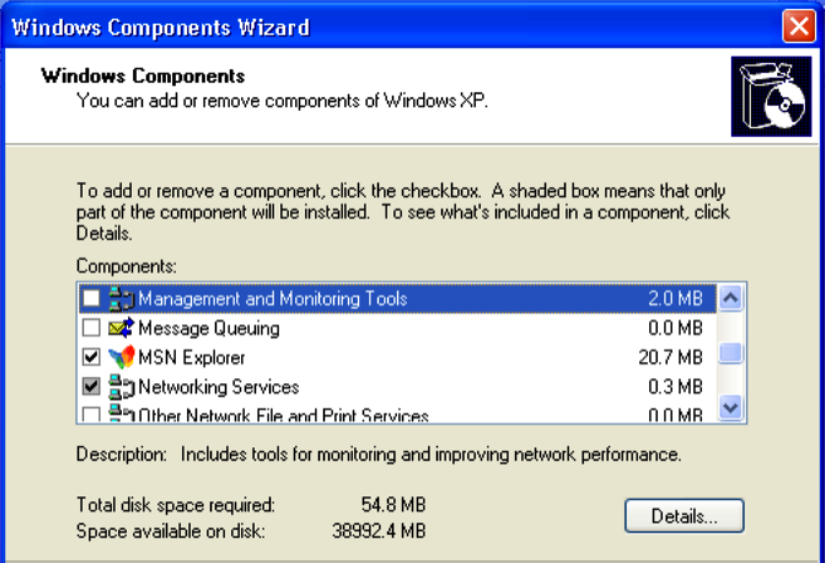
- From here, you will see a list of components that can be enabled or disabled on the operating system. Scroll down to Management and Monitoring Tools and double-click on it to open the options contained within, as shown in the following screenshot:
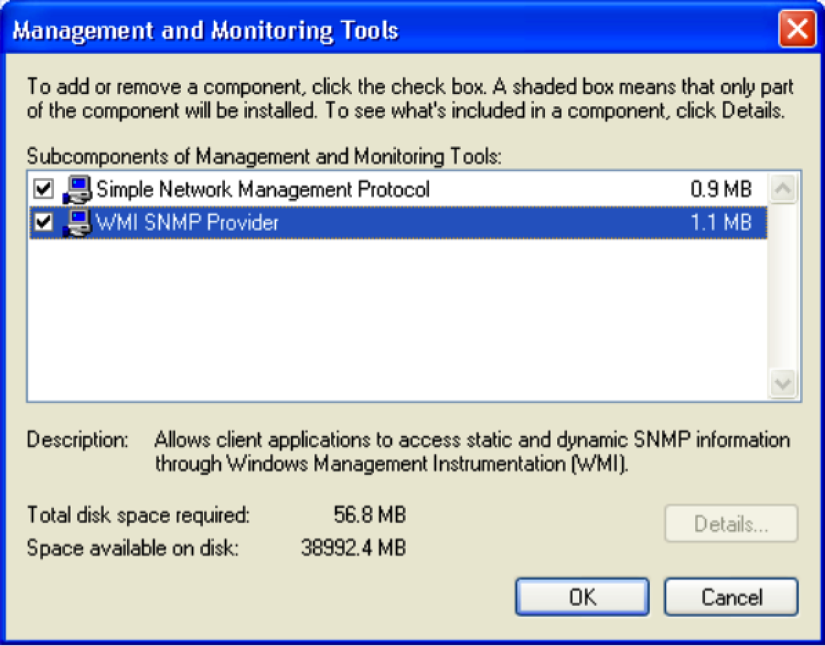
- Once opened, ensure that both checkboxes, Simple Network Management Protocol and WMI SNMP Provider, are checked. This will allow remote SNMP queries to be performed on the system. After clicking on OK, the installation of these services will begin. This installation will require the Windows XP image disc, which VMware likely removed after the virtual machine was imaged. If this is the case, you will receive a popup requesting you to insert the disc, as shown in the following screenshot:
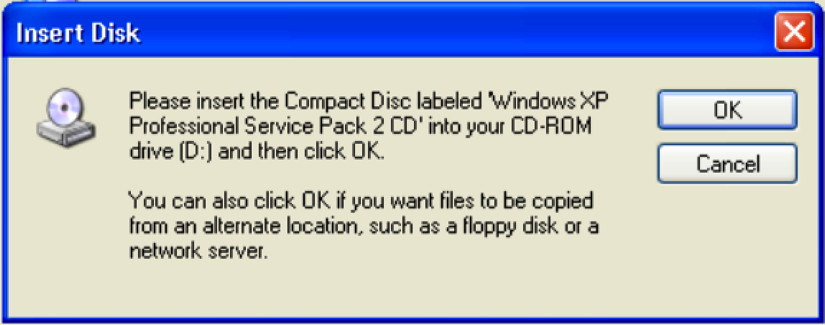
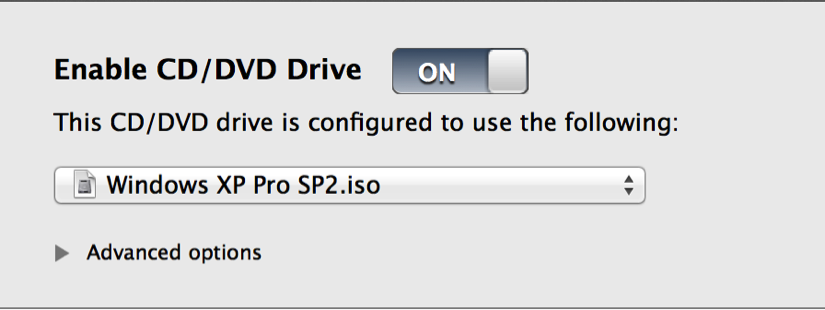
- To use the disc image, access the virtual machine settings. Ensure that the virtual optical media drive is enabled, then browse to the ISO file in your host filesystem to add the disc:
- Once the disc is detected, the installation of SNMP services will be completed automatically. The Windows Components Wizard window should notify you when the installation is complete. In addition to adding services, you should also remove some default services included in the operating system. To do this, open Control Panel again and double-click on the Security Center icon. Scroll to the bottom of the page, click on the link for Windows Firewall, and ensure that this feature is turned off, as shown in the following screenshot:
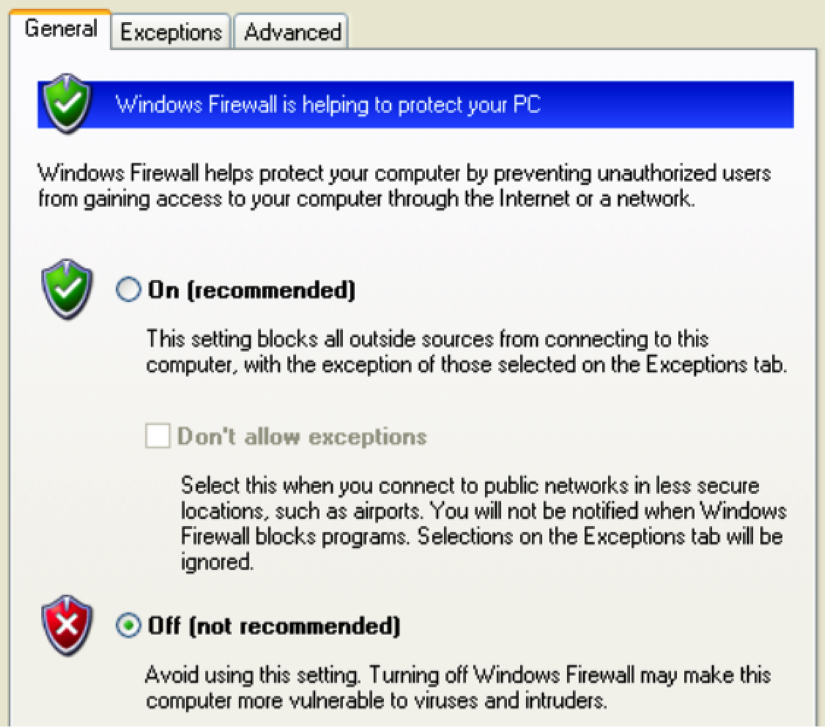
- After you have turned off the Windows Firewall feature, click on OK to return to the previous menu. Scroll to the bottom once again, click on the Automatic Updates link, and ensure that it is also turned off.
How it works...
The enabling of functional services and disabling of security services on an operating system drastically increases the risk of compromise. By increasing the number of vulnerabilities present on the operating system, we also increase the number of opportunities available to learn attack patterns and exploitation. This particular recipe only addressed the manipulation of integrated components in Windows to increase the attack surface. However, it can also be useful to install various third-party software packages that have known vulnerabilities.
http://www.exploit-db.com/
http://www.oldversion.com/














































































