Gearing up Wireshark
To ease the analysis of malicious traffic, Wireshark requires certain tweaks. In short, we need to create a new profile in Wireshark to inspect malware traffic.
Updated columns
We added the following columns in Wireshark:

The columns can be added/modified by going to menu bar and navigating to Edit | Preferences | Select Columns (under User Interface).
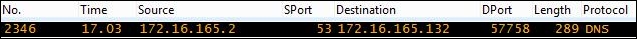
SPort—source port (unresolved)
DPort—destination port (unresolved)
HTTP host—display filter:
http.hostURI—display filter:
http.request.uri
Updated coloring rules
For any packet containing an unusual number of DNS answers, we colored it with a background color—black and foreground color—orange, as can be seen in the following image.
The coloring rule implied for any packet can be seen under the Frame header in the Packet Details pane.

Coloring rule implied for the above packet
Important display filters
Some of the common display filters in use can be saved as well, as shown in the following filter toolbar:

Simply put the filter...































































