One of the biggest cyber attacks of the century happened on Yahoo!, where it is believed that attackers were able to breach its systems in 2014 and make away with the account details of over 500 million users. The FBI has confirmed that social engineering was used in the attack to get the attackers past the scrutiny of the layers upon layers of security tools and systems used to protect such data. This attack on Yahoo!, a giant tech company, therefore confirms that social engineering is more dangerous than it's given credit for. No one is secure if one of the oldest email service providers that invests heavily in cyber security tools can be compromised so easily using this technique.
Social engineers have also been able to make away with huge sums of money using simple social engineering attacks. In 2015, a company called Ubiquiti Networks, which makes networking equipment, was hit by a social engineering technique. The attackers were able to collect information about the CEO and effectively assume his personality. They used this impersonation to direct the finance department to channel huge amounts of money to some overseas company that had informed him of a change in their payment preferences. Without question, a finance department member of staff transferred the money only to discover later on that the orders did not come from the real CEO and that the attackers had already made away with millions of the organization's hard-earned money. Further investigations revealed that the security systems were still in place and not compromised and the theft was only done through a social engineering con.
Both these incident emphasize the fact that human weakness cannot be discounted in the cyber security chain. It is fast becoming the widely used method for attacking organizations:

Today's cybercriminals are fortunate since users are exposing themselves to social engineering attacks. The rise of the use of social media platforms has been a key contributing factor to the increased number of social engineering attacks. This is because today's users are living their lives on social media and giving details about their daily lives, family, workplace, personal preferences, and so on that can all be used for a social engineering attack. An attacker needs only to go through a user's social media accounts to get enough information to stage a successful social engineering attack. There is more than enough information on Facebook, Twitter, Instagram, and Snapchat to enable a social engineer to assume the personality of most users. It is also surprisingly easy to create a fake social media account of a senior executive. This account commands instant respect and compliance with any orders issued to a target and can thus be used to rake money from junior employees at an organization.
Another method used on social media has been the creation of honeypot accounts of non-existent people that are used to attack real people. In July 2017, a senior IT operations employee at a Middle Eastern Telecommunications Company (METCO) escaped by a whisker shortly after approving a friend request from a honeypot account. The attack seems to have been highly targeted at, a male amateur photographer. This is because the attackers had created an attractive profile of a young girl called Mia that said she was an upcoming photographer in London and she shared very many hobbies with the target. The target was obviously quick to accept the friend request believing that they had a strong connection. After a few weeks of chats, Mia sent the man a photography survey. Unknown to the IT staffer, the survey was a file that contained a malware called Pupy RAT, which is used to steal login credentials when it is opened. Luckily, the company's computer was secured with effective end-host antivirus programs that quickly detected and disinfected the malware before any damage was done. Further investigations were able to reveal the hacking group behind the attempted social engineering attack. It was confirmed that the group had previously tried to attack the company using phishing emails but none were successful. The employees had been educated about fake emails and clicking on suspicious links or opening email attachments. It seems that the hacking group was able to come up with the social engineering attack and target one employee through Facebook.
This incident confirms that users, irrespective of the departments that they work in, are prone to social engineering attacks. The target here was IT-knowledgeable and yet the guise of a young, attractive lady who shared his interests was able to get his guard down. He opened a file inside the organization's network that could have stolen login credentials or even spread through the network and infected other computers. If a stronger malware had been used, the attack would probably have gone through. Users are all faced with the same weaknesses when it comes to social engineering. All it takes is for the attacker to find the weak spots in one personality. This could be blind obedience to any authority, loneliness, financial needs, or investment needs among others.
Okenyi and Thomas conducted a study on the anatomy of human hacking, which can be translated to social engineering.
They said that humans are always open to being manipulated by social engineers; all it takes are the right knobs to be turned. They found out that humans were obedient to authority above them and were thus ready to execute commands passed down from their superiors. This is a weakness that social engineers use frequently to try and pass down malicious commands using fake profiles of senior management staff at an organization. The two authors also came to the realization that humans are sympathetic to and trustful of strangers. Humans are caring and are willing to help strangers and this puts them in the unfortunate spot of being able to be manipulated by common crooks. Courtesy, trust, and sympathy have been used to get people to give out details to hackers on their personal devices containing very sensitive data. These hackers are able then to install malware or copy the sensitive data before the target is aware of this. Women, especially pregnant or disabled women, have been used to get targets to give out their device's details only for malware to be planted or data to be copied or wiped off. The authors discovered that humans are always interested in certain rewards and are willing to take actions that will supposedly earn them rewards.
A commonly used phishing tactic is to tell users that they stand the chance of winning hefty prizes if they click on certain links. Many people want the prizes and will, therefore, click on links supposedly leading them to giveaway pages only to find that the links lead to malicious websites. Humans also have a sense of guilt, a desire to please, and feelings of moral duty. These are among the psychological issues that will be discussed in the forthcoming chapters.
It is good to understand that social engineering is not generally a bad practice; it has both good and malicious applications. It is effective both ways because the targets share the same characteristics previously detailed and thus are always open to attack. Social engineering plays a key role in society; it enables people to get favors. Regardless of whether they are good or bad, it gets people to make decisions favorable to the person requesting them. It is only that social engineering is now being used by the bad guys to commit huge crimes. The framework of the tactics used for manipulating people during criminal acts is the same as that used for positive outcomes. The weaknesses being exploited are relatively the same and all humans share them.
One of the oldest social engineering scams is the Nigerian scam. It might have been the first widely successful social engineering attack mediated by email technology. Since it came up in the early days of emails, many people fell for it. Attackers pretended to be a well-off Nigerian prince that had a lucrative deal that only needed a target to offer some help and get a big cut. The con was executed when the targets were being asked to resolve certain problems by paying some cash in order to have a large payout released to them. The problems kept on coming until a target would eventually realize that there was no money to be released. A few human characteristics were being exploited in this attack which are discussed as follows:
- The first one is greed where targets were made to believe that they would indeed get a big cut from a huge fortune. Everyone wants money and, if it comes so easily, then many people will be willing to do what is being asked. It is not a strange characteristic that was only present in the victim; it is a characteristic present in everyone.
- Another characteristic exploited was commitment. Humans naturally want to see things to the end. This is the reason why the attackers discovered that they could fleece people of money by assuring them that the sooner they make the payment, the sooner the payout would be released. Again, it is a characteristic present in everyone.
- The last characteristic is trust and it was the core part of the attack. Strangers were being manipulated to trust another stranger on another continent and believe that all they were told was true. Trust is powerful and the strangers were quick to give the supposed Nigerian prince the benefit of the doubt when an error occurred in the processing of the payout. Exploiting three human weaknesses at once, the attack was very powerful and some people ended up losing as much as $50,000.
The following is an example of spam email:
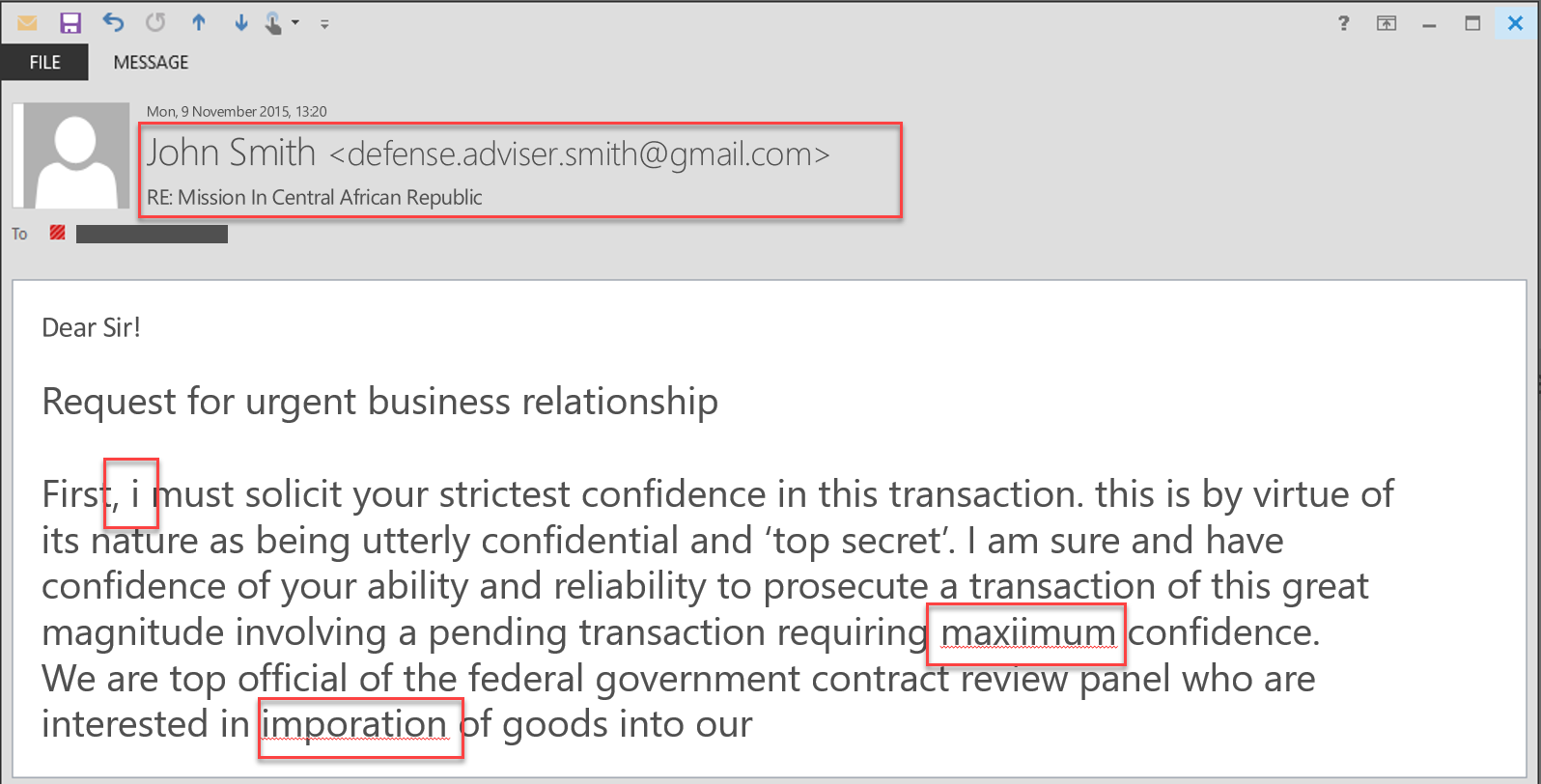
The preceding instance describes a well-structured social engineering attack that exploits human characteristics for malicious purposes. It is important to note that the same characteristics are used for positive outcomes. Trust is used every day in agreements or when making transactions and it is only in unfortunate scenarios that it is used maliciously. Commitment is used in almost all undertakings to ensure that they are successfully completed. Humans get a certain internal reward for completing tasks and are therefore committed to seeing through everything they start.
Greed is not necessarily a bad characteristic either. It is only human to be subtly greedy. Money is sought after and it is subtle greed that allows people to seek for it in all possible ways. It is therefore, only during unfortunate scenarios that these characteristics are exploited for malicious purposes.
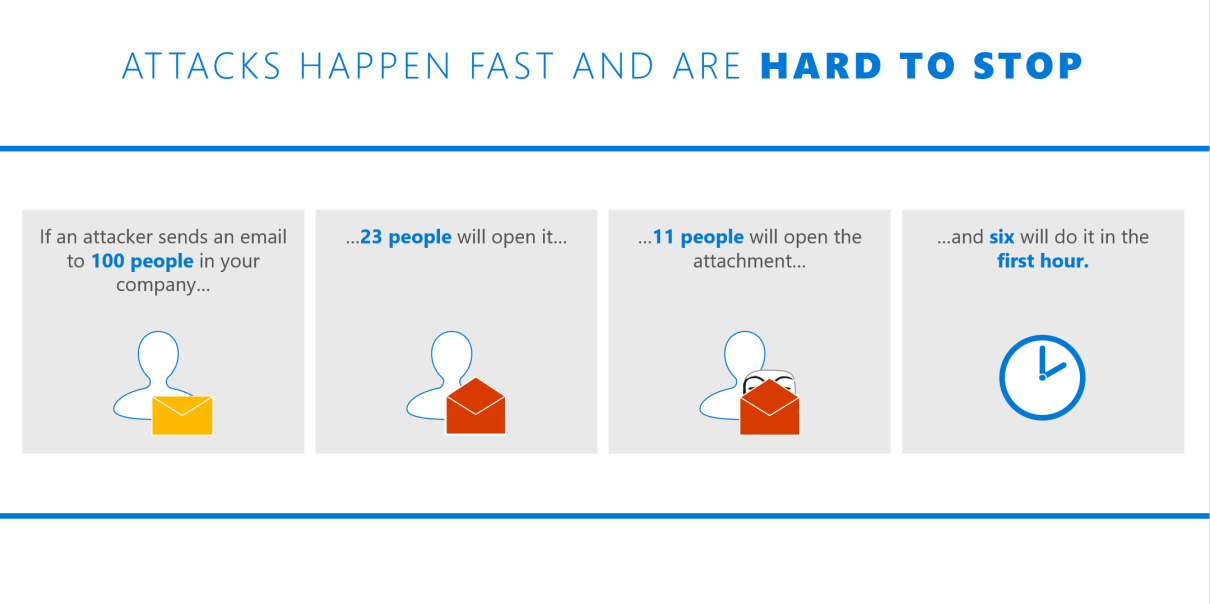
Consider the following figure based on Verizon's Data Breach report, 2015: