Identifying vulnerabilities
Now that we know more about the kinds of threats you may face, it’s even more important for you to know where to access information about these vulnerabilities. You also need to be aware of any resources that are available so that you can educate yourself on what’s required to remediate any vulnerabilities. As you are already aware, Windows is renowned for its ongoing vulnerabilities, and patching/updating these systems has morphed into a full-time and very specialized role over the years. The following website is the authoritative source regarding Microsoft security updates: https://msrc.microsoft.com/update-guide/en-us.
Useful Information
Here is a link to the Microsoft Security Response Center (MSRC): https://www.microsoft.com/en-us/msrc?rtc=1.
As shown in the following screenshot, you will be provided with a list of all identified vulnerabilities from Microsoft within a selected time range, with additional filtering options. To give you an idea of the risk profile for Windows, the following filter is scoped to Windows 11 for x64-based systems over November 2021, which returned 47 uniquely addressed vulnerabilities:
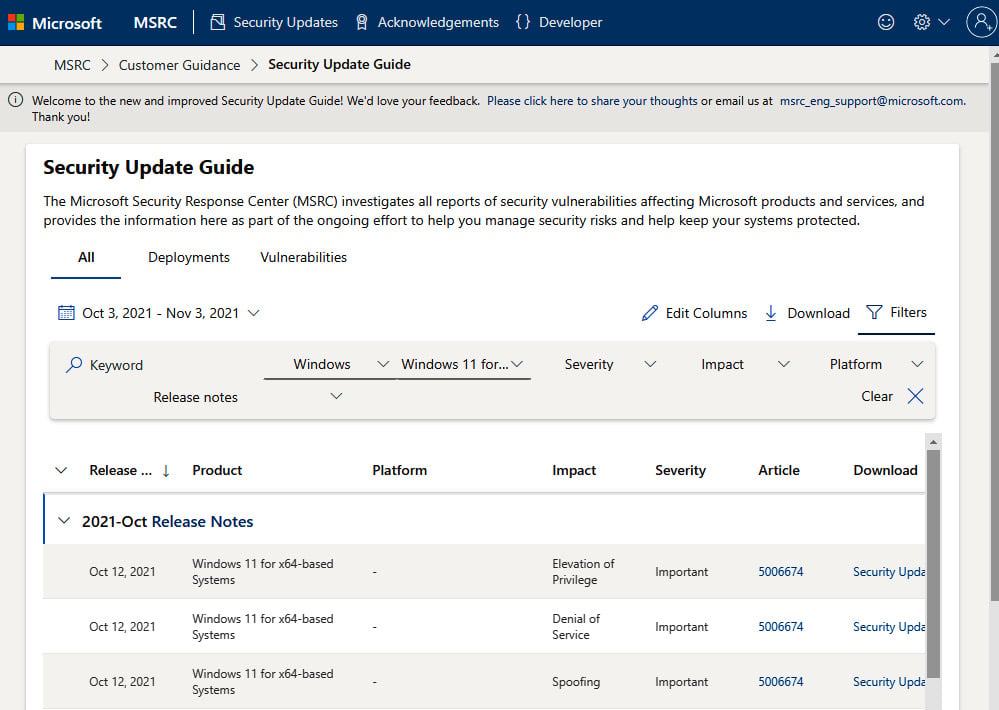
Figure 1.5 – Microsoft Security Update Guide
One term you may have heard as part of vulnerability management with Microsoft is the famous Patch Tuesday (also referred to as Update Tuesday). Patch Tuesday occurs on the second Tuesday of every month and is the day that Microsoft will release its monthly patches for Windows and other Microsoft products. There are many references on the internet for Patch Tuesday, in addition to the MSRC. One example of a common resource used to track Patch Tuesday releases is the Patch Tuesday dashboard: https://patchtuesdaydashboard.com/.
As you review the updates needed for your Windows systems, you will notice that each of them has a unique identifier (UID) to reference the update, beginning with CVE. CVE stands for Common Vulnerabilities and Exposures and is the standard for vulnerability management, allowing one source to catalog and uniquely identify vulnerabilities. CVE is not a database of vulnerabilities but a dictionary providing definitions for vulnerabilities and exposures that have been publicly disclosed. The US DHS and CISA sponsor the CVE.
Tip
Visit this website to learn more about CVE: https://www.cve.org/About/Overview.
The following screenshot shows an overview of what the CVE provides and can be found at https://cve.mitre.org/cgi-bin/cvekey.cgi?keyword=Windows:

Figure 1.6 – CVE Windows search results
In addition to the CVE is the NVD. NVD is the National Vulnerability Database, which is an additional resource for vulnerability management provided by NIST. The NVD is synced with the CVE to ensure the latest updates appear within its repository. NVD provides additional analysis of the vulnerabilities listed in the CVE dictionary by using the following:
- Common Vulnerability Scoring System (CVSS) for impact analysis
- Common Weakness Enumeration (CWE) for vulnerability types
- Common Platform Enumeration (CPE) for structured naming standards
The following screenshot shows an overview of what the NVD provides and can be found via https://nvd.nist.gov/vuln/search/results?form_type=Basic&results_type=overview&query=Windows&search_type=all&isCpeNameSearch=false:
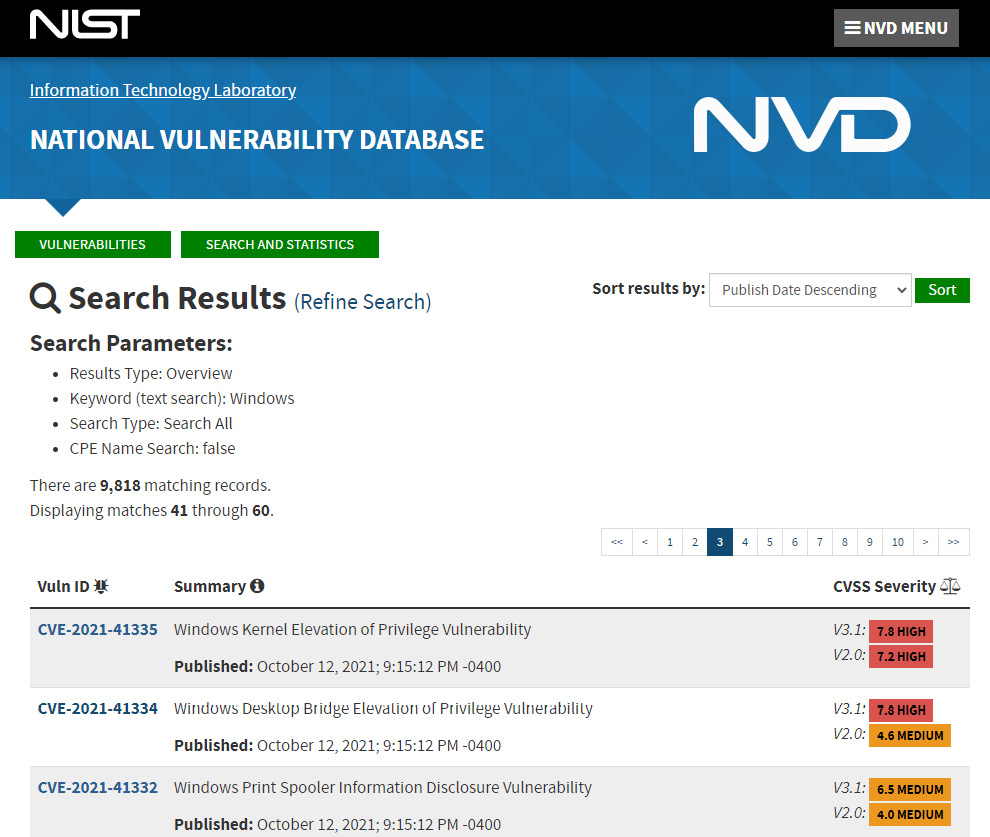
Figure 1.7 – NVD Windows search results
Information
CISA has released a known exploited vulnerabilities catalog that will be continuously maintained. This should be incorporated into your VMP for review. You can find the catalog here: https://www.cisa.gov/known-exploited-vulnerabilities-catalog.
One additional resource that we should mention is the Open Web Application Security Project (OWASP). OWASP is a nonprofit organization that helps improve the security of software for individuals and enterprises. It provides a tremendous amount of resources such as tools, documentation, and a community of professionals, all looking to continually enhance software security. Although OWASP is focused on application and web application security, there is a high possibility that an application or a web application will be running on your Windows servers and Windows clients. Because of this, it is critical, as a security professional, for you to be able to intelligently discuss these concerns and challenges with the business, developer(s), and application/web application owners.
Tip
You can find more information about OWASP at https://owasp.org/.
One of the more common projects that OWASP provides is the OWASP Top 10, which provides the most critical web application security risks. The latest version available was recently published in 2021 and is presented here:
- Broken Access Control
- Cryptographic Failures
- Injection
- Insecure Design
- Security Misconfiguration
- Vulnerable and Outdated Components
- Identification and Authentication Failures
- Software and Data Integrity Failures
- Security Logging and Monitoring Failures
- Server-Side Request Forgery (SSRF)
Tip
View OWASP Top Ten Web Application Security Risks for 2021 here: https://owasp.org/www-project-top-ten/.

























































