Android application fundamentals
Native Android applications are written mainly in Java or Kotlin. The Android SDK tools compile the code along with any data and resource files into an APK or an Android App Bundle. The compiled application is in a specific format, specified by the extension .apk. That is, an Android package is an archive file containing multiple application files and metadata.
Fun Fact
Rename the file extension of an APK to .zip and use unzip to open. You will be able to see its contents.
The following are the major components of an APK:
AndroidManifest.xml: The application manifest file containing app details such as the name, version, referenced libraries, and component details in XML format. The Android operating system relies on the presence of this file to identify relevant information about the application and related files.- Dalvik executable files (
classes.dexfiles). META-INF:MANIFEST.MF(manifest file)CERT.RSA(certificate of the application)CERT.SF(list of resources with SHA-1 digest of the corresponding lines in theMANIFEST.MFfile)
lib: This contains the compiled code that is specific to a selection of processors, as follows:armeabi: Compiled code for all ARM-based processorsarmeabi-v7a: Compiled code for all processors based on ARMv7 and abovex86: Compiled code for x86 processorsmips: Compiled code for MIPS processors
res: Resources that are not compiled intoresources.arsc.assets: Contains application assets.resources.arsc: Pre-compiled resources.Important Note
Java code in Android devices does not run in the Java Virtual Machine (JVM). Rather, it is compiled in the Dalvik Executable (DEX) bytecode format. A DEX file contains code that is ultimately executed by Android Runtime.
Let's see how to create a simple hello world application for Android and then unzip it to look at its components:
- Android apps are developed using Android Studio. Download and install the latest version of Android Studio from https://developer.android.com/studio:
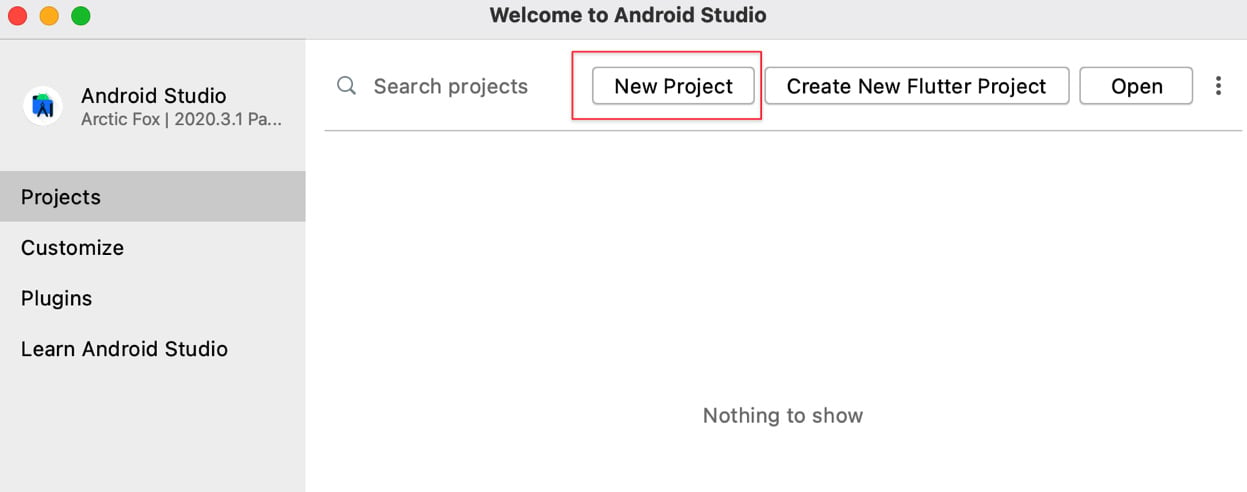
Figure 1.5 – Creating a new project in Android Studio
- Let's choose the New Project option and select the Empty Activity option:
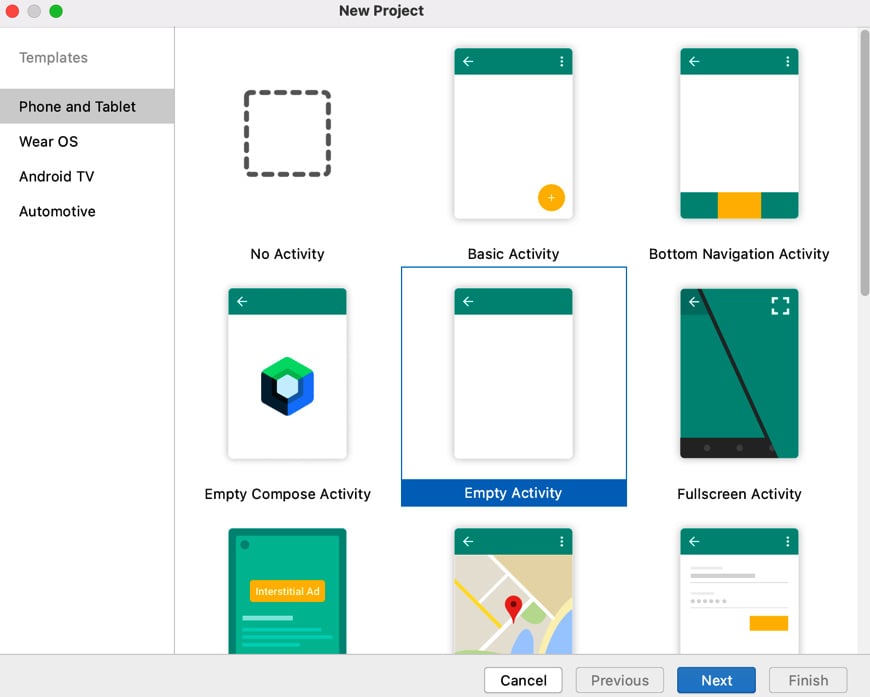
Figure 1.6 – Selecting project type
- On the next screen, fill in all the details as shown in the following screenshot. You can choose the name as you please:
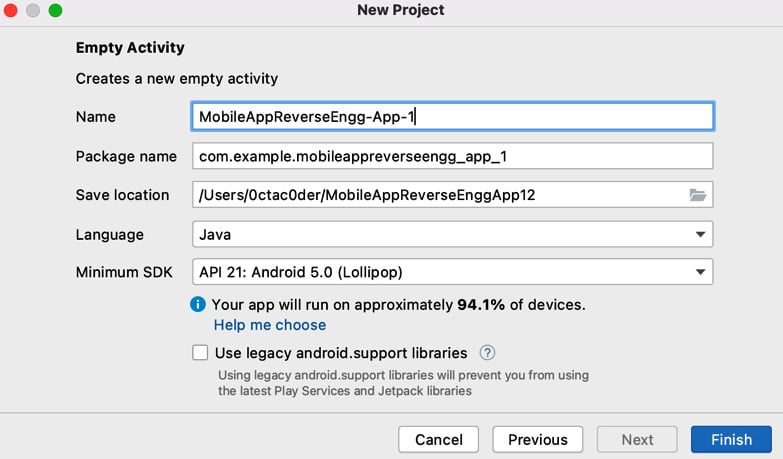
Figure 1.7 – Project details
- Once you click Finish, a new project will be created for a default activity/screen app.
- You can now try to run the app on any attached Android device, or the virtual Android emulator. For the latter, create a virtual Android device from the AVD menu.
- Once the app runs successfully, we will try to extract the application package for this app from Android Studio:

Figure 1.8 – Running the app on the emulator
- To get the APK from Android Studio, go to the Build | Build Bundle(s)/APK(s) | Build APK(s) menu option. Once generated, navigate to the folder mentioned in the Locate option and copy the APK.
- Once the APK is copied, change the extension of the file to
.zip:
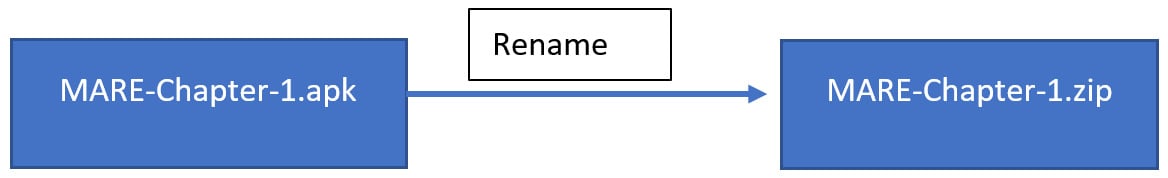
Figure 1.9 – Diagram of rename process
- Use any archive tool to unzip the file and extract its contents:
# unzip MARE-Chapter-1.zip
For reference, the result is as follows:
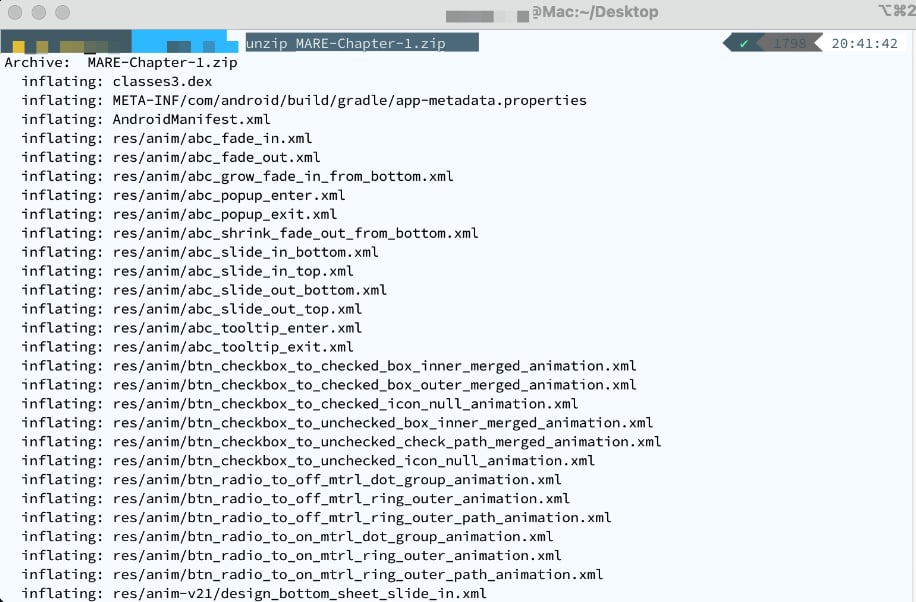
Figure 1.10 – Extracting the content of the APK, after renaming it to .zip
- Let's analyze the components inside the APK and compare it with the list here (Android application fundamentals):
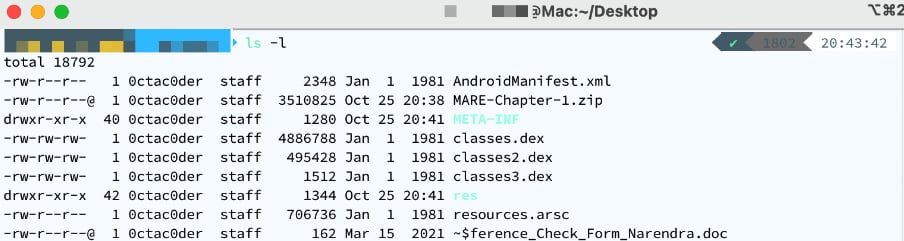
Figure 1.11 – Extracted content of the APK
The following diagram shows the processes of forward and reverse engineering an Android application:
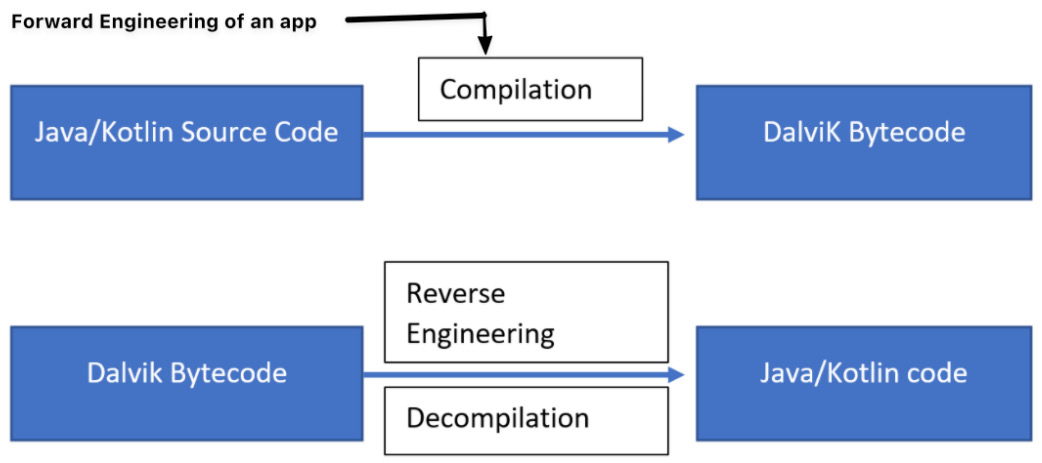
Figure 1.12 – The forward and reverse engineering processes with an Android application
Android applications are mainly developed using Java and Kotlin. The internals of an Android package are the same whether it is based on Java or Kotlin. Therefore, the approach to reverse engineer the application is also the same.
We've now learned about the fundamentals of Android applications. iOS apps are also packaged into a specific format and have a specific structure. Let's look into the iOS application fundamentals now.
































































