Hacking phases and methodology
With the required knowledge obtained, the process of hacking begins. Like any other well-organized task, hacking has its own sequence of steps that need to be followed to carry out a successful attack. Real-life hacking is a painstaking process and requires a lot of work. From gathering information to attacking to covering your tracks, each step needs to be executed perfectly. One lapse could potentially expose your identity and compromise the whole process. Figure 1.7 shows the different phases of hacking that will be discussed in detail:
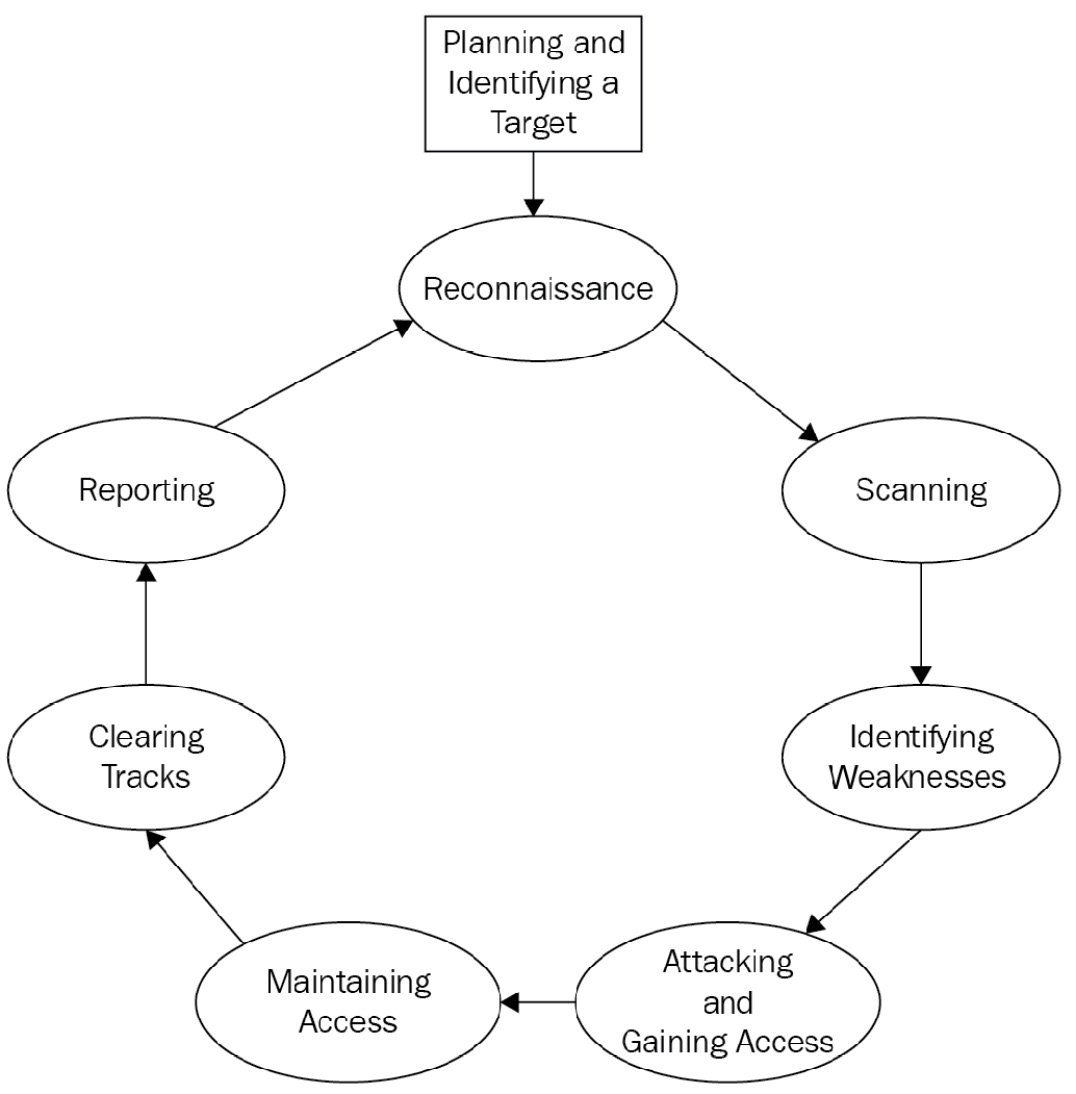
Figure 1.7 – Hacking steps
In the following sections, we are going to take a look at each step, in detail.
Planning
The first step of anything is proper planning. Time spent on proper planning could potentially save a lot of time wasted due to improper planning. The importance of planning cannot be stressed enough. In the following chapter, we will focus on penetration testing methodology, that is, testing how easy it is to penetrate a system or a network. We will perform an attack on a fiction organization called Famous Organization Limited and inside the organization, we will focus on a fictional person, let's call him Mr. Target. In a professional penetration testing scheme, you will need to create a proper workflow in the planning process and maintain all the relevant information obtained during the process in an orderly manner to be used for reporting purposes.
The next step is to identify the target person or system to be attacked. From a penetration testing point of view, here we will define the scope of the test, what it encompasses, its limitations, and the like. Before penetration testing is performed, we should make sure that the system under test is ready for testing. This includes ensuring that testing would not cause a breakdown of the critical infrastructure of an organization.
Before starting the penetration testing program, it should also be clearly mentioned who will be performing the attack and what kind of oversight will be present. The boundaries of what the penetration test includes and what is not included should be clearly defined. Test objectives and timelines should be properly mentioned beforehand. Penetration testing should be aligned with the company's objectives. In some cases, simulated scenarios are also tested where we want to see how an attack would impact the company's day-to-day operations. The planning stage should also determine what kind of penetration test is required.
Reconnaissance
Once the target has been identified and the planning stage is completed, we move forward to starting the penetration testing process. In the simplest terms, reconnaissance means gathering information about the target individual as well as the organization. Before any penetration attack is carried out, our goal would be to gain as much information about the target as we can. The more information we have about the target, the more opportunities we have to carry out a successful attack. There are two methods of information gathering, listed as follows:
- Passive information gathering
- Active information gathering
Let's study them in the following sub-sections.
Passive reconnaissance
Passive reconnaissance, as the name indicates, is a method of gathering information about the target individual and company by means of passive sources, without directly interacting with the intended target. This is the safest form of information gathering because there is no interaction with the target so it cannot be traced back to you. Passive reconnaissance includes gathering information from public sources. This could include gathering information available on the internet. Passive information itself is usually harmless, but combined with attack vectors, it can be exploited. For example, let's say that you visit the social media profile of the target and find out that the person is very interested in dogs. This information itself is not very useful. But if you send them an email containing a phishing link (phishing will be explained in a moment) containing some information about dogs, it is more likely that the target will click on this link and eventually compromise the system. Passive reconnaissance is usually done through search engines and public databases. Passive reconnaissance is much slower and usually gives limited technical data about the target. Although it is slower, the risk of getting caught in passive reconnaissance is very low.
Active reconnaissance
In active reconnaissance, you engage with the target directly, either personally or through the computer. Active reconnaissance is much faster and gives a lot of information about the target, albeit at the cost of higher risk. Active reconnaissance includes finding information about the system used by the target as well as other technical specifications associated with the target's system. The following is a list of the most used information sought in active reconnaissance; however, this is not a comprehensive list:
- IP address: The internet protocol address of the target, both private and public.
- MAC address: Field identifying the hardware interface used by the target to connect to the network.
- Ports: Port scanning is one of the most frequently used tools in active reconnaisance. Open ports in the system can be used for initiating a connection with the target without their knowledge.
- Services/software running on the target machine: Having knowledge of the different services running on a target could be a good starting point for initiating attacks. If a service running on the target has a known vulnerability, it could be easily exploited.
- Operating system fingerprinting: Determining the operating system used by the target.
These are the most common pieces of information sought in active reconnaissance. You should be very careful with active reconnaissance. Make sure that your identity is completely hidden while performing active reconnaissance. Most modern systems have intrusion detection systems (IDSes). They often keep a log of every attempt made to scan the system. If you are not anonymous, your identity can be easily revealed. Firewalls and IDSes often block unwanted port scans.
Scanning
As mentioned, scanning includes getting technical information about network topology and the target. Understanding the network topology helps you to pivot once you have gained access to the system. Creating a list of active hosts along with the target machine is an important aspect of the scanning process. Detecting firewalls and routers in the network can also be helpful. One of the main goals of scanning is to identify vulnerabilities, either by finding open ports or detecting vulnerable services running on the system. A lot of commercial tools are available for scanning purposes. One of the most famous tools for network reconnaissance is NMAP. NMAP has a Python API that could be used to create automated scanning testing. We will discuss some examples of using the NMAP API in Python in later sections.
Network and port scanning are very noisy processes in terms of generating a lot of network requests. Modern IDSes are very quick to detect them. This means that the slower the scanning process is, the more chance there is of it being successful. Sweeping the network to detect live hosts is one example of this. Application services and version detection are also considered an important aspect of network scanning, though it is a more complicated task.
A packet sniffer is another tool that helps you to monitor network traffic. If you are connected to the same network as the target, it can provide insights into the network traffic, which could help to identify potential opportunities for attack. One of the most famous and free network sniffing tools is Wireshark. It helps you to monitor and see network traffic in detail.
Identifying weaknesses
Network scanning and reconnaissance would give you a lot of information. It is necessary that you keep track of all the information obtained in a structured manner, which would help you to identify relevant information. In practical cases, hackers work on information gathering for an extended period lasting from a few months to even years. Once you are confident that you have sufficient information, you can proceed forward to the next step, which is identifying weaknesses. This step includes examining all the information obtained in the previous step and determining which information could be useful for carrying out an attack.
Attacking and gaining access
Once you have identified the weaknesses, the next step is to start thinking about an attack strategy. There is no hard definition of what an attack strategy would look like. If you want to gain control of the remote system via the command line, you can use either a forward shell or a reverse shell. Most operating systems in use today provide a command-line interface to their functionalities. In Windows, you can access it through the Cmd.exe or powershell.exe programs. In the case of Linux, you can use Bash. You can execute nearly any task on the operating system with the command-line interface and therefore having a command line or command-line interface to the target is extremely dangerous. If you have a command-line process running on the target machine that you can control on your own system, you can essentially do anything with the victim/target machine.
Forward shell
In the forward shell, the attacker tries to initiate a connection to the target machine. In modern systems, this type of strategy is quite hard as IDSes and firewalls of the target system usually block all unwanted incoming connections unless otherwise specified in the firewall rules. This makes this strategy quite difficult to execute.
Reverse shell
In a reverse shell, the attacker plants the malware program into the system in some manner and then once the program is executed on the victim's machine, it initiates a connection back to the hacker, thus giving them full control. These attacks are quite successful since it is very hard for an IDS to differentiate between a legitimate process and a malicious process.
Attacks can also be carried out by exploiting some vulnerability in software running on the target machine. There are a lot of online resources that explain how you can create a payload (a piece of code that performs a malicious operation) and execute it on the target machine. One of the most widely used tools in this domain is Metasploit. It contains tons of preloaded exploits; once you have detected that a vulnerable service is running on the target PC, you can use Metasploit to create payloads that can be delivered to the target machine to gain access to these systems.
Maintaining access
Once you have entered the target machine, the goal should be to maintain persistent access to these systems. Hackers try to maintain access to the system for as long as possible without being detected. There are a lot of reasons why hackers would compromise a system. Sometimes they just gain access to a system to use it as a launchpad to attack other system infrastructure; in this case, they are usually not very concerned about being detected while carrying out something such as a Distributed Denial of Service (DDoS) attack from compromised machines. In other cases, they would stay on the compromised system in stealth mode, watching every activity and sometimes stealing data. Using sniffers, attackers could easily monitor network traffic, which can be very dangerous for the victims.
Once the attacker gets into a system with very primitive access, their immediate goal is to increase their access deep into the network or a system. This would ensure that the attacker has long-term access to the victim/target machine, and they can control it whenever they want. Another important aspect of maintaining long-term access is pivoting, in which you attack other machines present in the same local area network. This helps the attacker to maintain a strong foothold in the network and makes it difficult for the IDS to clean the tracks of the attacker.
Post exploitation
Once you have gained basic system access, it is always a good idea to enhance your access levels. For example, you can get basic user-level access to the system by exploiting a system vulnerability; however, most of the time, this kind of access will be very limited in nature and would not help you to penetrate further into the system. For example, in Windows, you cannot disable an antivirus or IDS using user-level privileges; you need to be an administrator in order to do this. In later sections, we will learn how to increase your access level from a normal user to a system admin, which would virtually give you complete control over the system.
Covering tracks
Covering tracks is an essential aspect of a successful penetration testing attack. In cybersecurity, the incident response team are the individuals whose goal is to limit the extent of the attack and provide restoration operations to the services. Once the hacker achieves their objectives, they should cover their tracks completely; otherwise, they can be easily detected by forensics. Common methods of covering tracks include removing logs and temporary files created during the attack phase and cleaning registry entries, caches, and in some cases browser history. A penetration tester should also be aware of logging mechanisms related to different operating systems. For example, the Windows operating system maintains the record of recently accessed and modified files using jump lists. Digital forensic experts use these technologies to determine the attacker and the extent of the attack on the system.
A lot of open source tools are available on the internet for covering tracks that perform a very good job at hiding your identity. For example, in Metasploit, you can use scripts such as clearv to clear up all event logs on Windows machines.
Another method to cover tracks is by using reverse HTTP shells. A shell is a code that executes user commands on a system. We will talk more about this in later chapters. In most computers, port 80 is used for HTTP packets; therefore, port 80 is open a lot of time in computers. It is very hard for firewalls to distinguish between legitimate and malicious packets over port 80. Using HTTP-based reverse shells, forensic analysts have a very hard time distinguishing hackers.
Once the hacker has gained access to the system, they will run various commands over the command-line interface. Once the objective is achieved, the hacker usually deletes the command history in order to avoid detection. This is done using the export HISTSIZE=0 command in Linux-based systems.
Reporting
The last phase of penetration testing or ethical hacking is to compile a report about all the weaknesses of the system as well as the achieved objectives of the penetration test. The pen-test report should list out all the necessary details regarding the attack. A penetration test report usually contains the following items.
Summary
The summary should summarize the pen-test briefly. It should explain the main reason for the pen-test. The following points should be considered while writing a summary report for a pen-test:
- The purpose and objectives of the pen-test
- The scope of the pen-test
- A brief list of the tests performed
- The findings of the pen-test
- The conclusion of the pen-test
These tasks are explained as follows.
Introduction
In the introduction section, all the relevant information about the test environment should be explained. It should mention the timeline of the pen-test from the start to the end. How long did the pen-test take? It should mention the methodology and approach used to perform the pen-test. Which systems were targeted during the pen-test and finally, what kind of tests were performed?
Methodology
In this section, we should list all the procedures and methods used to attack the target. For example, how did we get information about the target and what information did we get? How was this information used in carrying out the attack? Which methods of delivering the payload were used? For example, did the attacker send a malicious PDF file to the target? It should also mention the difficulty level for the attacks, that is, which aspects were easy to attack and which sections were hard.
Findings
The findings section should mention the vulnerabilities and threats detected in the pen-test. It is a good idea to divide the number of vulnerabilities found into different levels based on their severity level. An example of this test would be to perform a vulnerability scan on the devices and detect whether any vulnerable service is running on the system. Finally, the findings should also mention the positives of the system as well, for example, strong firewall configuration and strong passwords. For serious vulnerabilities and threats, in-depth details should be mentioned. It is a good idea to attach necessary screenshots and findings to the document.

























































