Basic InfoSec terminology
Before we get into some heavier topics, first, we need to establish a common set of terms and ensure we're speaking the same language in order to simplify the ideas in this book. Otherwise, this book could become too complex, or even nearly impossible to decode as a result. My intention for this book is to reduce ambiguity and ensure you're right here with me.
For example, on the first page, I said that this book is going to help you with "making a difference in your day-to-day work at your organization." In that sentence, we can see a common InfoSec term: organization. Whether your information security knowledge is being utilized by a corporation, government, small business, firm, non-profit, extracurricular group, or some other structure, they all fit under the umbrella term of "organization," and that's the one we're going to use in this book.
Let's look at a few other basic terms. How about information? Information includes data but can also include common knowledge or intellectual property. For example, the new company slogan that is written down on a whiteboard after a brainstorming session is now "information," which should be protected, even if it isn't "data" in terms of it sitting on a hard drive in ones and zeros.
That logically brings me to security, or the state of protection. Information has the ability to be secured in various ways, most commonly noted as a triangle or "triad" of concepts called the CIA Triad. You'll remember this from other InfoSec books and training you have done, but CIA stands for confidentiality, integrity, and availability. They're extremely important in navigating the day-to-day of information security, and that's why they're being brought up again:
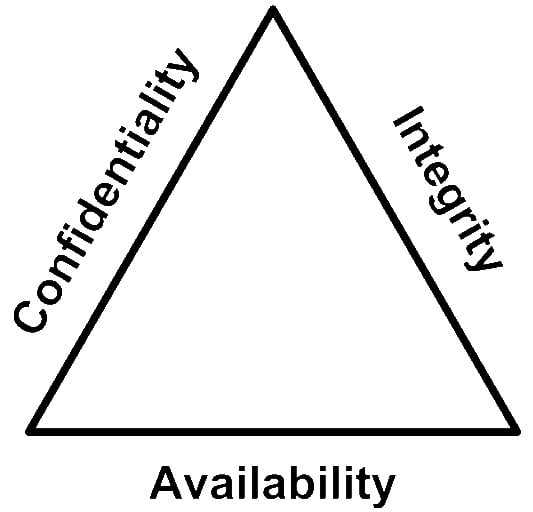
Figure 1.1 – The CIA Triad
Confidentiality is the concept of keeping information secret and ensuring only those that have been authorized to can see it. Integrity is the concept of being sure the information hasn't been changed without permission. Availability means that those with permission to access the information can access it in a timely fashion. The reason the CIA Triad is often represented as a triangle (as in the preceding diagram) is because the three principles work together as an interconnected system that represents the security of an asset, or group of assets.
The often-forgotten "N" in the CIA Triad is non-repudiation, which is a way of saying that if an entity has authored (or changed) some information, it is authoritatively indisputable. It is the ability to prove the origin of said data.
Now that we've covered some of the basics, I'd like to discuss why risk management is important to you and your organization.


























































