Configuring a firewall for an Azure Data Lake account using the Azure portal
Data Lake account access can be restricted to an IP or a range of IPs by whitelisting the allowed IPs in the storage account firewall. In this recipe, we'll learn to restrict access to a Data Lake account using a firewall.
Getting ready
Before you start, perform the following steps:
- Open a web browser and go to the Azure portal at https://portal.azure.com.
- Make sure you have an existing storage account. If not, create one using the Provisioning an Azure storage account using the Azure portal recipe in Chapter 1, Creating and Managing Data in Azure Data Lake.
How to do it…
To provide access to an IP or range of IPs, follow these steps:
- In the Azure portal, locate and open the Azure storage account. In our case, the storage account is packtadestoragev2, created in the Provisioning an Azure storage account using the Azure portal recipe of Chapter 1, Creating and Managing Data in Azure Data Lake.
- On the storage account page, in the Security + Networking section, locate and select Firewalls and virtual networks.
As the packtadestoragev2 account was created with public access, it can be accessed from all networks.
- To allow access from an IP or an IP range, click on the Selected networks option on the storage account on the Firewalls and virtual networks page:
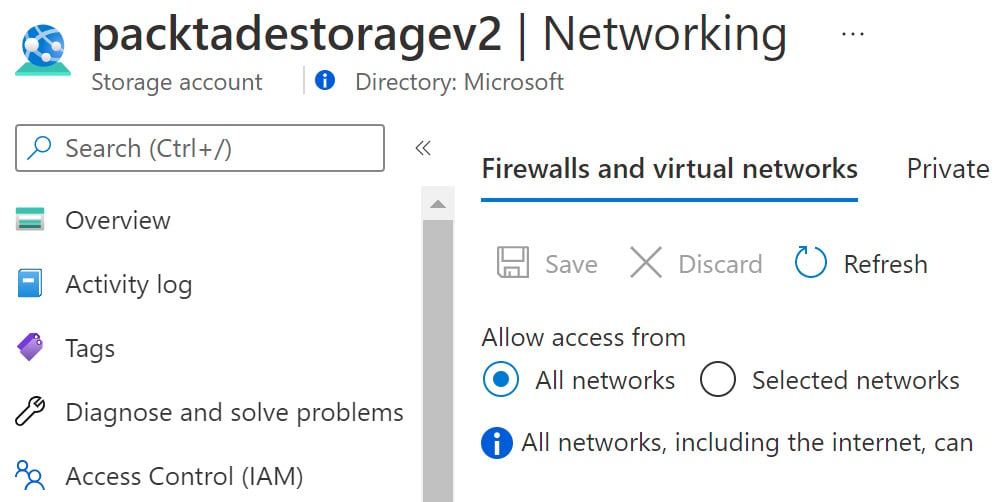
Figure 2.1 – Azure Storage – Firewalls and virtual networks
- In the Selected networks option, scroll down to the Firewall section. To give access to your machine only, select the Add your client IP address option. To give access to a different IP or range of IPs, type in the IPs in the Address range section:
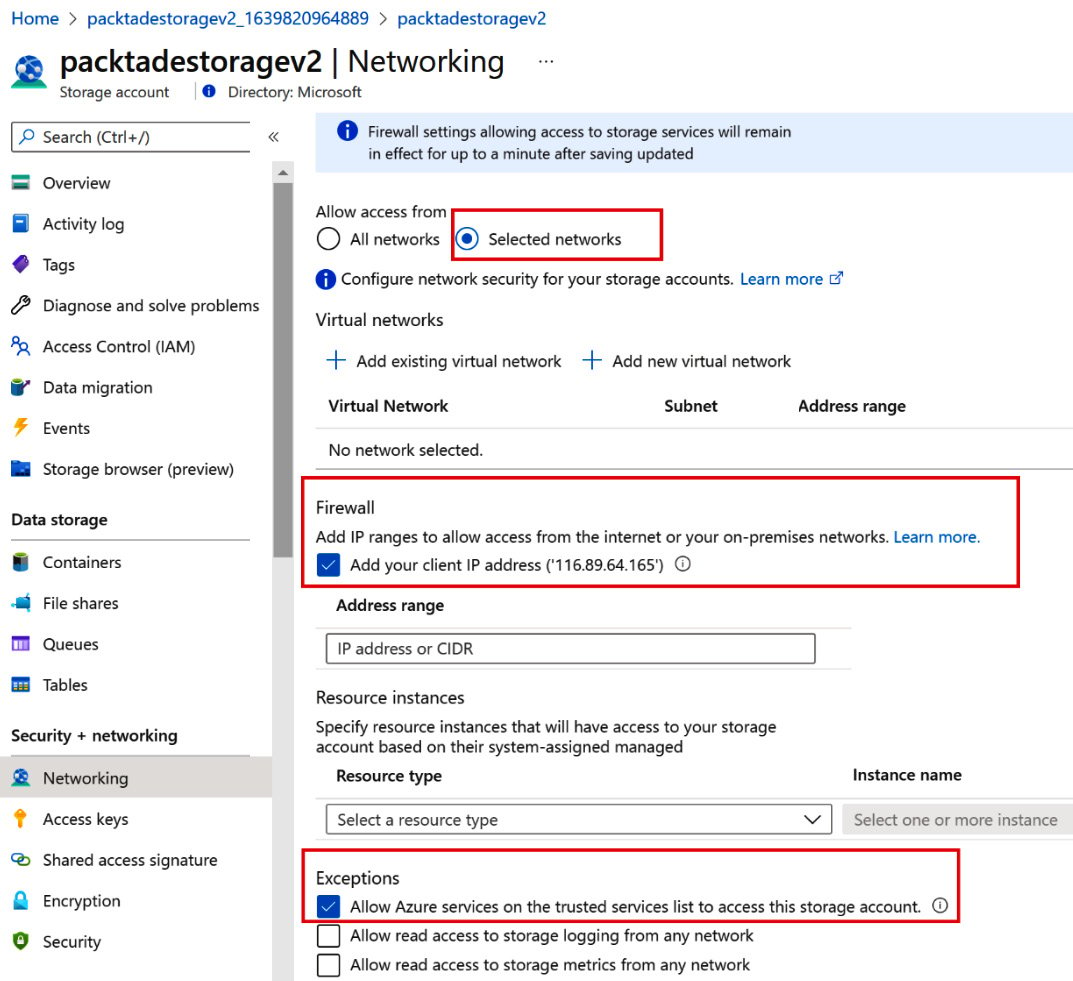
Figure 2.2 – The whitelist IPs in the Azure Storage Firewall section
- To access storage accounts from Azure services such as Azure Data Factory and Azure Functions, check Allow Azure services on the trusted services list to access this storage account under the Exceptions heading.
- Click Save to save the configuration changes.
How it works…
Firewall settings are used to restrict access to an Azure storage account to an IP or range of IPs. Even if a storage account is public, it will only be accessible to the whitelisted IPs defined in the firewall configuration.























































