Isolating your environment
With our tooling installed, we no longer require internet access for most malware analysis. Analysis with a VM connected to the internet can pose several risks and should be avoided unless absolutely necessary. Risks associated with exposing your VM to the internet include the following:
- Allowing attackers to directly interact with the target machine via command and control
- Assisting in the wider propagation of worming malware to your network or others
- Accidentally participating in illegal activities such as DDoS as a zombie, being utilized as a proxy for further hacking of targets, and more
For these reasons, it's important that we set our VM to be isolated by default and only expose it to the internet if absolutely necessary in order to further understand our malware. And even in instances such as these, take proper precautions.
Isolating your VM is a simple process, and only requires a few clicks. As before, we'll highlight our VM in VirtualBox, and then click the Settings icon as shown in the following screenshot:
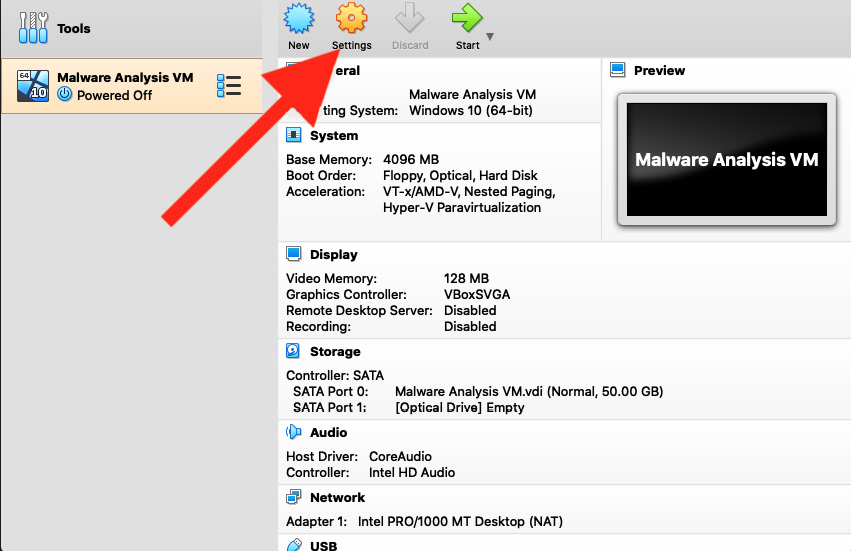
Figure 1.19 – VirtualBox's Settings button will take you to the Settings pane
With the Settings pane open, navigate to the Network pane. Here, we can select Host-only Adapter. This will limit the VM's network communication to just the host and prevent the spread of malware via the network to more sensitive endpoints.
Thankfully, other host isolation features such as Shared Folders and Shared Clipboard access are off by default in VirtualBox and do not require further configuration for VM isolation:
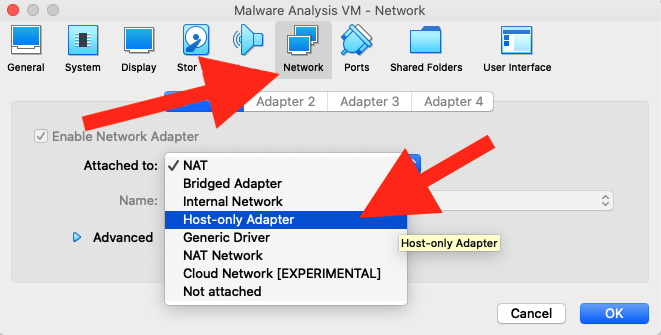
Figure 1.20 – Setting up Host-only Adapter
A word on executing with network activity
Occasionally, when examining malware samples, it is impossible to proceed without having an internet-connected VM. Droppers responsible for writing malware to disk often reach out to staging servers on the internet to download secondary stages, as opposed to writing them directly to disk from memory.
This can pose a challenge to an isolated VM and prevent an analyst from fully studying the execution of malware within an environment. Fortunately, it's possible to determine whether this access is required with a number of tools prior to enabling network access for your VM. These tools will be covered further in Chapter 3, Dynamic Analysis – Techniques and Tooling.
While VirtualBox does not necessarily have built-in mechanisms for safely executing in this manner, it's highly recommended that a separate network be set up, either physically or via a VLAN, for any dynamic malware analysis that requires network connectivity in order to function properly.

































































