Kerberos authentication with Protocol Transition
In order for end-to-end Kerberos to work, the client needs to be able to reach the KDC. This will not be possible in most environments, either because there are external users or partners in the mix, or simply because security policies require not exposing the KDC directly to all users. This is where Protocol Transition comes into the picture. Let's now turn our attention to the flow for this scenario. For the purpose of this section, I have set up LDAP in the frontend, with Kerberos in the backend.
Here, NetScaler authenticates the users with whatever authentication policy is bound to the AAA vServer but then uses Kerberos in the backend to obtain service tickets for those authenticated users. The following image demonstrates the flow:
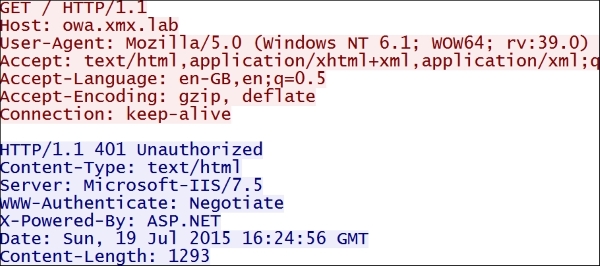
The flow goes like this:
The User requests the page
With LDAP authentication being configured on the frontend, LDAP exchange takes place and the User is authenticated
The User tries to request the page again, providing...























































