Understanding possible controls for compliance
This recipe identifies controls that may be used to fulfill compliance requirements. In addition, it maps those controls to technologies and tools such as System Center.
Getting ready
Understand your business and the scope for the compliance program based on the Planning the scope of a compliance program recipe.
How to do it...
Controls have two aspects to consider. On one hand, controls will provide you with a handle to fulfill compliance requirements. On the other hand, controls help you define processes and how tasks are done within the company. The most important thing to remember is keeping it simple. Most authority documents demand evidence of compliance but allow you to decide on the actual implementation and use of technology. Wherever possible, use automated controls based on the company's existing technologies.
The type of control implemented as part of the compliance process depends on the acceptance of your auditor, scope, the criticality of the requirement, or (simply) the budget and resources available.
The following illustration provides an overview of the type of controls:
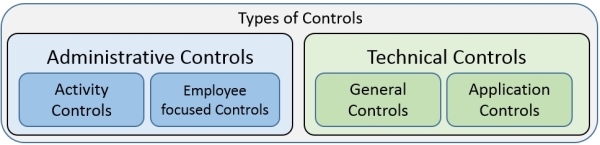
The controls are explained as follows:
- Administrative controls: They are most often process-related controls. For example, they influence or shape the activity of a process. Another example is that they reduce inefficiency and/or inconsistency.
- Employee-focused controls: They could include training, such as security awareness. The goal is to ensure that the employee knows what he or she is supposed to do and how.
- Technical controls: They focus on controls related to technical systems.
- General controls: They focus on the overall IT environment. The goal is to ensure that all IT operations are running in a secure and failure-free manner.
- Application controls: They are, as the name indicates, focused on the application level. The goal is to ensure that the processing, saving, exporting, and so on of data are correct. For example, technical controls exist to ensure the principles of orderly bookkeeping.
Regardless of compliance requirements, the implementation of administrative and technical controls is essential to ensure the survival of your company. Without any controls, the orderly conduct of business is not possible. In almost any company, some controls exist; however, they might not be obvious, as they are already integrated into the technologies used, or they may exist and not be documented.
There are also different characteristics to controls. Those include the following:
- Manual controls: They are always performed by a person.
- Automated controls: They are performed by an IT system.
- Preventive controls: They try to guard against a risk or an undesired situation from occurring.
- Detective controls: They collect data and try to discover inconsistency or whether a risk has occurred based on the collected data. Therefore, the undesired event has taken place, but it will be reported in some way to act upon.
With regard to the fulfillment of compliance requirements, the characteristic of a control must be weighted differently. For example, the most desirable control is an automated, preventive one followed by an automated detective one. Automated controls are viewed as more consistent and are not subject to personal interpretation. Therefore, an auditor will always favor those over manual ones. Keep this in mind when deciding on controls.
How it works...
The kind of control to use always depends on the situation of the company and the risk the control is supposed to address. Several factors influencing the decision of controls are listed here:
- The size of your company
- The legal structure of the company
- Services or products offered
- Employee qualifications
First, let's focus on an administrative control. One requirement might be to ensure the prevention of process inconsistency. The risk might be process inefficiency or an undesired activity by an employee. One example is having the right to enter supplier or customer data including financial data and the right for payment up to a certain limit. In this case, the employee could alter the bank details and then issue a payment; alternatively, the employee could split a payment into two if the bill is higher than his or her allowed payment limit.
The most desired control would be an automated preventive one. In this example, a role-based access control would prevent the first example, as most modern purchase order systems allow the creation of roles and tying those to certain rights or areas. The preventive measure here provides segregation of duty by splitting the process between two employees, preventing risk.
An automated detective control could be to check whether bank information for a certain supplier or customer has been changed right before a payment. To mitigate the second example, check if several payments have been made within a short timeframe with the same reference number.
When focusing on small companies, segregation of duties might not be possible, or the application might not offer role-based access controls. In this case, a manual preventive control could be used. One example is the four-eye principle. In this case, another employee has to approve payment as well.
The least desirable control would be manual detective. The amount of data or the number of transactions due to automated IT systems has been growing so much that inconsistency will most likely not be visible. Nonetheless, a manual detective control could be to pick several payments and check them for orderly processing.
Administrative controls have a protective function, as they try to prevent undesired events from happening. They do not exist to monitor every movement of an employee. Instead, they try to mitigate the risk that an employee might face a situation where, under pressure, an undesirable event could occur.
The next example focuses on technical controls. Again, we will use the purchase order system as an example. As mentioned before, data protection laws require protection of sensitive data. As an example, the German BDSG mentioned in the first recipe requires access control to prevent unauthorized usage. Please refer to Appendix, Useful Websites and Community Resources, for further information on BDSG.
The standard PCI DSS is fairly general, it demands access control in the form of authentication or logon without mentioning any system. As part of an authentication procedure, most companies will use a username and password combination. The kind of authentication procedure might depend on the product or service offered.
For highly sensitive products such as the ones in the military, research, or the medical industry, a more sophisticated implementation might be desirable. This will shape the kind of control required. We will focus on the most common authentication with a username and password. In order to ensure a meaningful password, many companies have an administrative control in place requiring adherence to a password policy.
An automated preventive control is the introduction of Microsoft Active Directory and the creation of a Group Policy Objects (GPO) that demands a certain password complexity. Therefore, a user will be prevented from using shorter, non-compliant passwords. The same thing might be possible within applications.
An automated detective control could be a tool that scans for undesired passwords. In this case, employees could use a non-compliant password, but the administrator would receive a report showing these. The administrator is now in a situation to remediate instances of non-compliance or recommend further action in the case of repeated occurrence.
A manual preventive control could be the usage of password letters. In this case, an employee would create passwords.
A manual detective control isn't feasible to ensure complexity of passwords. However, an example can be ensuring that only relevant people have access to an application. In this case, HR would provide a list of employees who have left the company or changed positions. The compliance team with the IT team would check whether those employees are no longer active in critical applications.
To understand the kind of controls available, you can try using a brainstorm technique. This could include the following:
- Talking to application owners to identify existing application controls, for example, roles in an application for an access management control
- Researching industry best practices for the objective you have; for example, access (and identity) management offers many papers from Microsoft on how to achieve this using Microsoft Active Directory Domain Service (AD DS)
- Researching frameworks that offer a list of controls
































































