Identifying where to use packet analysis
To conduct an effective packet analysis, the first step is to get a good capture. There are many places in which to conduct packet analysis, including on a LAN, on a host, or in the real world. Let's start with using packet analysis on a LAN.
Analyzing traffic on a LAN
Today's networks are complex. An enterprise network provides connectivity, data applications, and services to the clients on the network, as shown in the following diagram:
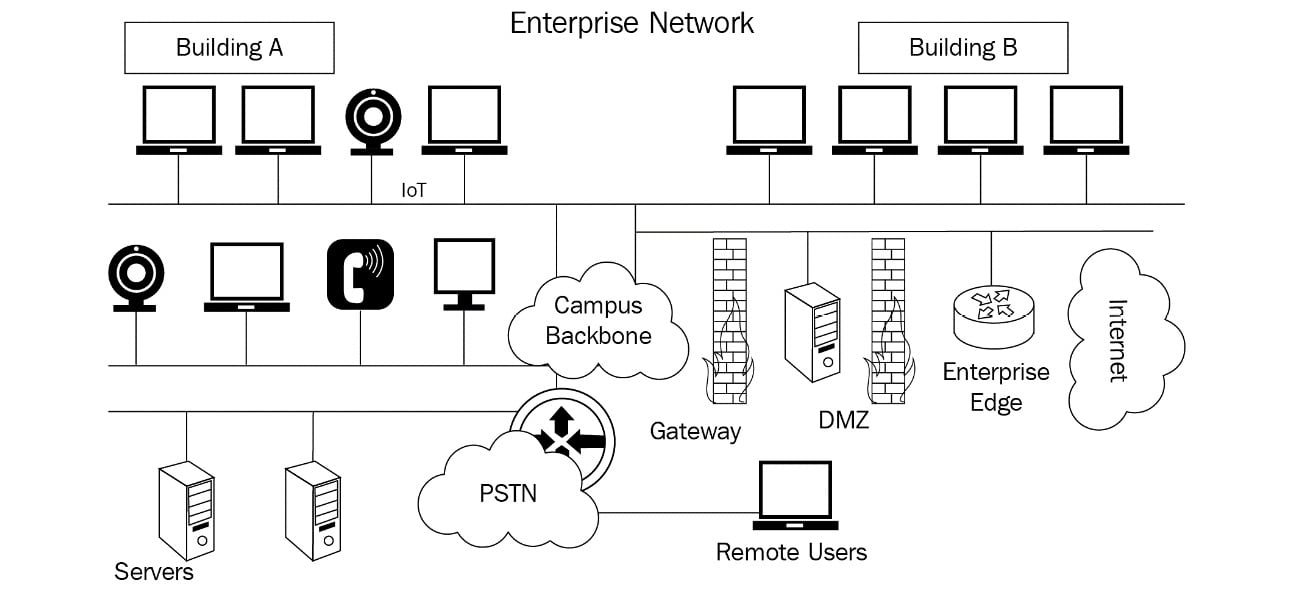
Figure 1.7 – A LAN
Most LANs are heterogeneous, with various operating systems such as Windows, Linux, and macOS, along with a mixture of devices such as softphones, tablets, laptops, and mobile devices. Depending on the business requirements, the network might include wide area network connectivity along with telephony.
To effectively use packet analysis, placement is the key. Not all traffic is created equally. Depending on placement, you might only capture a portion of the total network traffic. If the packet sniffer is on a host or end device, then it will be able to see the traffic on the segment's collision domain. If the sniffer is mirroring all traffic on a backbone, then it will be able to see all the traffic.
In certain instances, you might need to perform packet analysis on an individual host, such as a PC, to only monitor traffic destined to that host. In other cases, you might need to gather traffic on a switch to see the traffic as it passes through the switch ports.
Sniffing network traffic
Packet analysis can be done on an individual host, within a switch, or in line with the traffic. The difference is as follows:
- If the protocol analyzer is installed on a client device attached to a switch, then the view of network traffic is limited. While sniffing traffic on a single switch port, you will only see broadcasts, multicasts, and your own unicast traffic.
- To see all the traffic on a switch, the network administrator can use port monitoring or Switched Port Analyzer (SPAN). In some cases, you may be able to monitor within the switch, as Wireshark is built into the Cisco Nexus 7000 series and many other devices.
- Another option is to use a full-duplex tap in line with traffic. The tap makes a copy or mirror of the traffic, which is pulled into the device for analysis. If this option is used, then you might require a special adapter.
In addition to using packet analysis on a LAN or a host, packet analysis can be used in the real world to monitor traffic for threats.
Using packet analysis in the real world
Packet analysis is used in the real world in many forms. One example is the Department of Homeland Security (DHS) EINSTEIN system, which has an active role in federal government cybersecurity. The United States government is constantly at risk of many types of attacks, including DoS attacks, malware, unauthorized access, and active scanning and probing.
The EINSTEIN system actively monitors the traffic for threats. Its two main functions are as follows:
- To observe and report possible cyber threats
- To detect and block attacks from compromising federal agencies
The EINSTEIN system provides the situational awareness that is necessary to take a proactive approach against an active attack. The intelligence gathered helps agencies to defend against ongoing threats.
As illustrated, packet analysis is effective in many locations. The following section provides guidance on what circumstances packet analysis will reap the most benefits under.
































































