Combining Kali Linux and Raspberry Pi
The Kali Linux Raspberry Pi image is optimized for the Raspberry Pi. When you boot up your Raspberry Pi with your Kali Linux image, you will need to use root as the username and toor as the password to log in. We recommend you immediately issue the passwd command once you log in to change the default password. Most attackers know the Kali Linux default login, so it is wise to protect your Raspberry Pi from unwanted outside access.
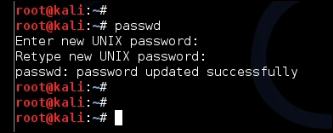
The following screenshot shows the launch of the passwd command to reset the default password:
When you issue the startx command, your screen might go blank for a few minutes. This is normal. When your X Windows (GUI) desktop loads, it will ask you whether you would like to use the default workspace or a blank one. Select the default workspace. After you make your selection, the desktop might attempt to reload or redraw. It may be a few minutes before it is fully loaded.
The following screenshot shows the launch of the startx command:

The first thing that you need to do is upgrade the OS and packages. The upgrade process can take some time and will show its status during the process. Next, you need to make sure you upgrade the system within the X Windows (GUI) environment. Many users have reported that components are not fully upgraded unless they are in the X Windows environment. Access the X Windows environment using the startx command prior to launching the apt-get upgrade command.
The following screenshot shows the launch of the apt-get update command:

The following screenshot shows the launch of the apt-get upgrade command:

Here are the steps you need to follow to open the Kali Linux GUI:
- Ensure you are in the X Windows desktop (using
startx). - Open a terminal command.
- Enter the
apt-get updatecommand. - Enter the
apt-get upgradecommand. - Enter the
synccommand. - Enter the
synccommand. - Enter the
rebootcommand.
After you have upgraded your system, issue the sync command (as a personal preference, we issue this command twice). Reboot the system by issuing the reboot command. In a few minutes, your system should reboot and allow you to log back into the system. Issue the startx command to open the Kali Linux GUI.
The following screenshot shows the launch of the sync and reboot commands:

You will need to upgrade your systems using the apt-get update and apt-get upgrade commands within the X Windows (GUI) environment. Failure to do so may cause your X Windows environment to become unstable.
At this point, you are ready to start your penetration exercise with your Raspberry Pi running Kali Linux.
Pros and cons of the Raspberry Pi
As stated in various parts of this book, the Raspberry Pi is designed to be an inexpensive computing option designed for various purposes. Inexpensive systems offer limited computing power, so one major drawback when using a Raspberry Pi for any type of penetration testing is its lack of power to run resource-intensive tasks. For this reason, it's highly recommended that use a Raspberry Pi for specific tasks rather than a go-to attack arsenal, as a full-blown Kali Linux installation offers many more tools over the limited Kali Linux ARM architecture.
The following two screenshots show the difference between the options available for one toolset category in the Kali Linux ARM architecture and a full-blown Kali Linux installation. We also found that some of the tools in the Kali Linux ARM do not function properly when they are run from the GUI, or they just failed in general. You will find more reliable tools in a full-blown installation of Kali Linux on a more powerful system than a Raspberry Pi. Here is the Kali Linux ARM screenshot showing Live Host Identification tools, which are ncat and nmap:

Here are the tool options for the same Live Host Identification category found in a full-blown installation of Kali Linux. As you can see in the following screenshot, a lot more options are offered:

Raspberry Pi penetration testing use cases
There are use cases for leveraging a Raspberry Pi outside of its "cool" factor. The first use case is delivering low-cost, remote penetration testing nodes to hard-to-reach locations. An example of this is when you offer penetration testing services to branch offices in China, UK, and Australia with limited bandwidth across sites. Rather than flying to each location, you can charge your customer the cost to build a Raspberry Pi and ship out each box to a location. You can have a local person plug in the Raspberry Pi as a network tap and perform the penetration test remotely, thereby dramatically saving in travel and hardware costs. In most cases, you can probably let the customer remove and keep the Raspberry Pi after the penetration test due to its low cost. You would have saved a customer thousands of dollars using this method as an alterative to enterprise cloud scanning tools that on a average have a much higher cost associated per location.
Another use case is abusing the average user's trust by physically accessing a target's location by claiming to be an IT or phone support representative doing maintenance. The Raspberry Pi chipboard can be hidden in any official looking hardware such as gutting a Cisco switch, hub, and so on, and placing the Raspberry Pi in one port. The average user wouldn't question a network box that looks like it belongs there.
In both these use cases, the major selling point is the Raspberry Pi's low cost, which means that losing a system won't break the bank. Also, both the use cases showcase the Raspberry Pi's value of being very mobile due to its small form. So, the Raspberry Pi makes a great alternative to more expensive remote penetration toolsets such as the ones offered by PWNIE Express (we are not saying that the PWNIE Express tools are not cool or desirable, but they will cost you a lot more than the Raspberry Pi approach). Speaking of which, you can run a light version of the PWNIE Express software on a Raspberry Pi as well, which is touched upon at the end of this book.
A common reason to consider a Raspberry Pi is its flexibility of design, its software, and its online community. There are thousands of websites dedicated to using the Raspberry Pi for various types of use cases. So, if you run into a snag, you are most likely to find a solution on Google. There are many options for operating systems and pretty much everything seems to be open source. This makes requirements for many design requests possible, such as the need to develop a large amount of affordable systems for mobile classrooms.
With a Raspberry Pi, the possibilities are endless. Regarding penetration testing, Kali Linux offers pretty much everything you would need for a basic exercise. The Kali Linux ARM is limited; however, you can always use apt-get to download any missing tools to meet your requirements for a penetration testing exercise as long as the tool doesn't require massive computing power. We will be covering how to download missing tools later in the book. So, go shell out $50 – $100 on a Raspberry Pi and check out the online communities for more information on how you can take your Raspberry Pi to the next level.
























































