Understanding iOS security
Apple devices are widely known for their ability to secure user data. With every release of a new iOS device or update to the iOS operating system, Apple works hard to improve security by introducing new features and by patching known vulnerabilities. In the following sections, we'll go over the key elements of Apple's security model.
User authentication
To secure physical access to the device, some form of user authentication is required. iOS devices implement authentication through two mechanisms:
- Passcode authentication
- Biometric authentication
By default, Apple devices suggest a six-digit numeric passcode, although the user can choose a four-digit passcode too or a custom alphanumeric code. Once a passcode has been set, the user will have to enter it every time the device is turned on and when it wakes up.
To improve the user experience while maintaining high-security standards, with the iPhone 5s, Apple introduced biometric authentication through Touch ID, which uses fingerprints as a passcode. With the release of the iPhone X, Apple introduced Face ID, which employs face recognition to unlock the device.
Unlocking passcode-protected iOS devices is one of the main challenges in mobile forensics.
Because there are a relatively small number of numeric passcodes, brute-force guessing attacks could theoretically be used to exploit authentication. However, this is extremely risky as iOS is designed to rate-limit passcode entry attempts, and data can be permanently deleted from the device if too many failed attempts occur.
This passcode is not just used to unlock the device itself – it's one of the key features of the iOS data protection model: the passcode, combined with the hardware encryption key, is used to generate a unique and extremely strong encryption key that is used by an algorithm to encrypt user data.
Encryption and Data Protection
While user authentication provides a degree of security in preventing unauthorized access to the physical device, these mechanisms could still be bypassed by exploiting vulnerabilities in software or hardware. A compromised device could potentially allow unauthorized access to the device's filesystem. For this reason, starting with the iPhone 4, the entire filesystem is encrypted using strong cryptography algorithms. However, with the release of the iPhone 5s, Apple set a new precedent in mobile security by introducing a technology called Data Protection, which relies on multiple dedicated components to support encryption and biometrics.
Secure Enclave
At the heart of iOS's security is Secure Enclave, a dedicated system on a chip (SoC) isolated from the main processor and operating system that provides cryptographic operations for data protection and key management.
Secure Enclave's main components are as follows:
- Secure Enclave Processor (SEP), which runs an Apple-modified version of the L4 microkernel and provides computing power exclusively to Secure Enclave.
- A memory protection engine.
- A True Random Number Generator (TRNG), which is used to generate random cryptographic keys.
- Dedicated Advanced Encryption Standard (AES) hardware engines, which communicate directly with the SEP through a secure channel and perform in-line encryption and decryption as files are written or read.
- A unique ID (UID), a cryptographic key that uniquely identifies the device. The UID is randomly generated and fused directly into Secure Enclave's hardware during device manufacturing, so it isn't visible outside the device.
- A dedicated, secure, nonvolatile storage system that can only be accessed by Secure Enclave. This is where data encryption keys are stored, ensuring that these are never exposed to iOS systems or applications.
The following diagram shows the different components of Secure Enclave:
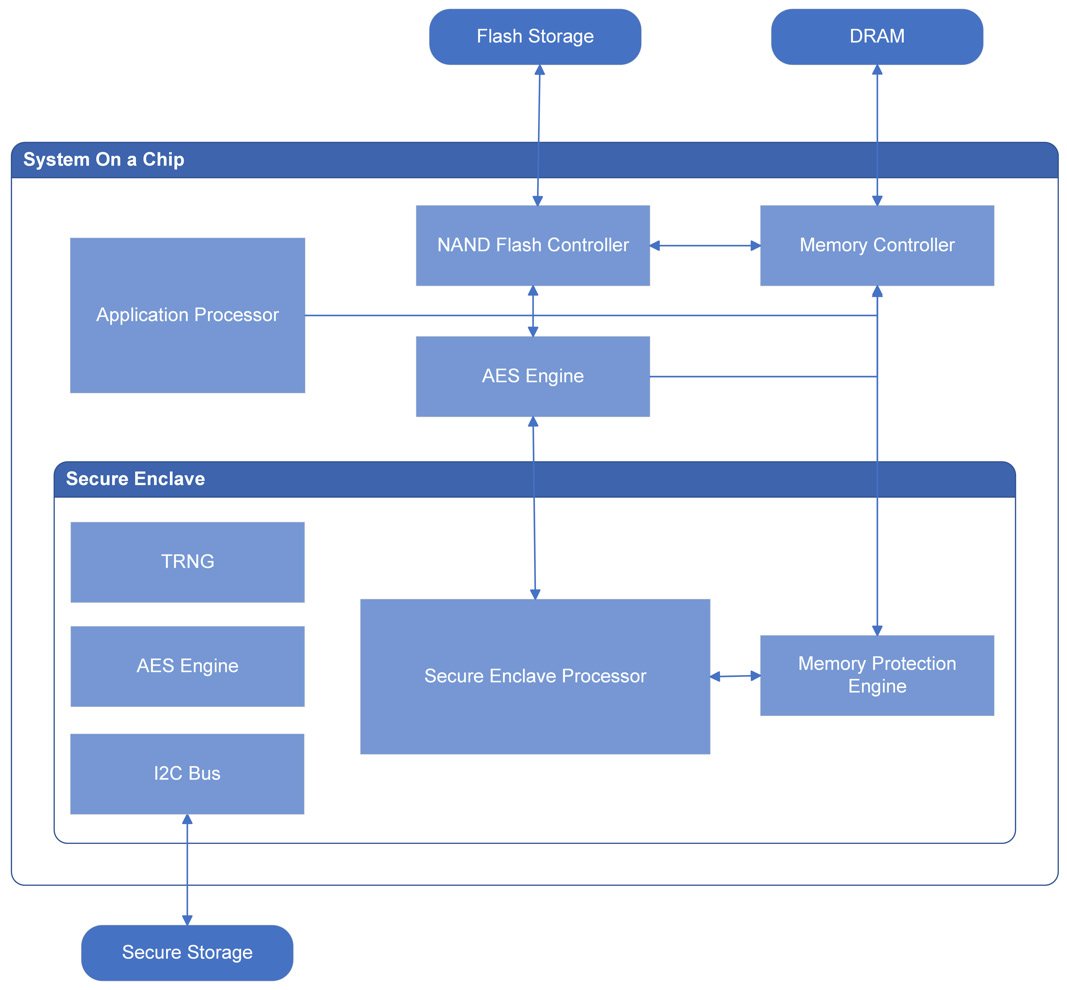
Figure 1.2 – Secure Enclave components
Secure Enclave is responsible for several different security-related operations, including generating and storing keys necessary for encrypting data on the device and evaluating biometric data from Touch ID and Face ID.
SEP uses the UID to generate cryptographic keys that are tied to the specific device. This adds another layer of security: if the device's SSD storage is physically moved to a different device, files can't be decrypted and thus will be inaccessible, since every device has a unique UID and the original UID is required to decrypt files.
iOS Data Protection keys
Data protection on iOS is implemented by generating and managing a hierarchy of cryptographic keys.
To make things easier, before we delve into the details, let's take a look at what keys are used during the encryption and decryption processes and what their purpose is:

Figure 1.3 – Cryptographic keys used for iOS data protection
- The device's UID is an AES 256-bit key that's fused directly into Secure Enclave during manufacturing. This key, together with the user's passcode, is used to unlock class keys.
- Class keys are generated when specific events occur on the device; for instance, when a device is unlocked, a complete protection class key is created. Shortly after the device locks, the decrypted class key is discarded. Class keys are used to wrap and unwrap file keys.
- File keys are 256-bit keys that are used to encrypt the content of each file; these keys are per-file keys and, as such, are randomly generated every time a new file is created on the user partition. File keys are encrypted using a class key and are then stored in the file's metadata. The metadata of all the files is encrypted with the filesystem key.
- The filesystem key is a random key that is generated when iOS is first installed or when the device is wiped. The filesystem key is stored on the device, and it's been designed to be quickly erased if the user requests it. Deleting the filesystem key makes all the files on the filesystem inaccessible.
iOS Data Protection classes
Let's take a closer look at the class keys.
Apple allows developers to specify security settings for each file by selecting a protection class that is assigned to a file when it is created. There are four different protection classes, depending on how the file is meant to be accessed:
- Complete Protection: Class keys for this protection are decrypted when a device is unlocked and are automatically evicted shortly after device lock, so a file associated with this protection class will only be accessible when the device is unlocked.
- Protection Unless Open: This protection class allows files to be created and encrypted when the device is locked, but only decrypted when the device is unlocked. This is used, for example, when an email attachment is downloading in the background.
- Protected Until First User Authentication: Class keys for this protection are decrypted when the device transitions from a before first unlock (BFU) state to an after first unlock (AFU) state and remain in memory, even if the device is locked.
- No Protection: The class keys for this protection class are always available in memory when the device is on.
Encrypting content while performing normal operations on a device can be challenging. Protection classes allow files to be encrypted safely, modulating the degree of protection based on how and when each file needs to be accessed.
For example, data that is useful to applications running in the background, such as messages or contacts, can be assigned to the Protected Until First User Authentication class; this allows data to be accessible to the device while keeping it encrypted.
iOS data encryption and decryption
When a file is written to the filesystem, the content of the file is encrypted with a per-file key, which is wrapped with a class key and stored in a file's metadata. The metadata is then encrypted using the filesystem key.
We've already seen how class keys are generated using a combination of the hardware's UID and the user's passcode while the filesystem key is generated upon iOS installation and stored on the device. Now, let's analyze the individual file encryption process step by step:
- Every time a file is created on the filesystem, Secure Enclave creates a 256-bit file key and passes this key to the hardware AES engine.
- The AES engine encrypts file content while it is written to flash memory using the provided file key.
- The file key is then wrapped with one of the four class keys, depending on the assigned protection class, and is stored in the file's metadata.
- Metadata for all the files is encrypted with the filesystem key.
All key handling happens in Secure Enclave, thus never exposing the operations to the system and its applications.
The decryption process works the other way round:
- When a file is opened, its metadata is decrypted using the filesystem key, revealing the wrapped file key and the assigned protection class.
- The file key is unwrapped using the class key and is then passed to the AES engine.
- The hardware AES engine decrypts file content while it reads the file from memory, using the provided file key.
Tip
Key wrapping is the process of encrypting one key using another key to securely store or transmit it.
Although the data protection architecture may seem complex, it provides both flexibility and good performance.
By now, you should have a basic understanding of where iOS stores application data, how data is structured, and how iOS leverages authentication and data protection to guarantee a high level of security on all devices.
In the next section, we will learn about the guidelines for a forensically sound examination process.
























































