We will define three broad areas in which all of the technology pieces required for enabling the IoT can be classified. The first one is edge-related technologies, which enable all of the activities that can be performed close to the source of the data. This includes sensors and sensor hubs that interface with the actual machines and devices. These perform data acquisition, basic data filtering, and data transfer to the cloud or gateway. Data from the sensor hubs flows to controllers or mobile devices that are used for storage and perform advanced data cleaning and filtering. The analytics on the edge happen on the gateways where data aggregation and analytics take place. Edge applications can also be deployed on the gateways, which can perform the real-time analytics to be done close to the source the of data. Apart from these, there are management applications that are required to manage devices and edge analytics applications. A platform to support the runtime environment for these also needs to be provided on this layer. Now, let's check the following diagram:
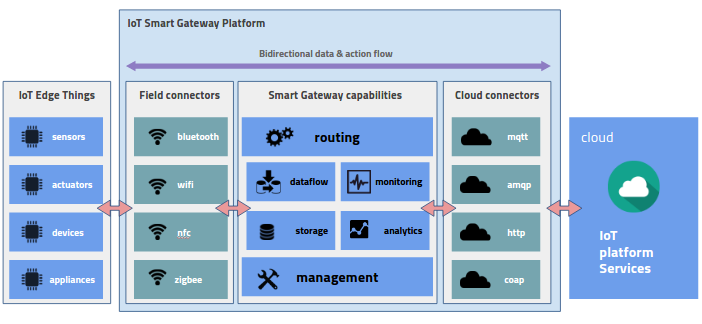
A key component of the IoT architecture is the gateway, which acts as the interface or proxy between the edge devices and the cloud/enterprise data center (see smart gateway in the preceding diagram). Apart from handling the connectivity between the edge and the cloud, the gateway acts as the interpreter/translator between field and cloud protocols. These gateways are increasingly becoming smart as they are embedded with logic to direct traffic based on rules, such as should data be transmitted as is or does it need to be aggregated or filtered prior to being transmitted? The following table describes the commonly used protocols on the edge layer:
|
Field Protocol
|
Specifications
|
Standards
|
Key Features
|
Typical Use Case
|
|
Bluetooth Low Energy
(BLE)
|
ISM band from 2.4 to 2.485 GHz (short wave lengths)
|
Bluetooth SIG standards
|
Low energy, small distances (couple of meters)
|
Inter-device communications on the edge
|
|
Zigbee
|
2.4 GHz
|
IEEE 802.15.4 protocol
|
Distances of up to 100 m in a given area
|
Applications that require relatively infrequent data exchanges at low data-rates over a restricted area
|
|
Wi-Fi
|
2.4 GHz UHF and 5 GHz SHF ISM radio bands
|
IEEE 802.11
|
Range can be up to several square kilometers using multiple access points
|
Leveraged by developers for their applications
|
|
Near Field Communication
(NFC)
|
Radio frequency ISM band of 13.56 MHz
|
RFID standards ISO/IEC 14443 and FeliCa
|
For distances that are less than 4 cm
|
Extends the capability of contactless card technology
|
Common protocols utilized at the edge
Similarly, we have prepared a table for the common cloud protocols that are used as part of the IoT stack, which is presented as follows:
|
Cloud Protocol
|
Specifications
|
Standards
|
Key Features
|
Typical Use Case
|
|
Message Queue Telemetry Transport
(MQTT)
|
Protocols availability depends on context
|
ISO/IEC PRF 20922
|
Publish/Subscribe architecture with broker for pub/sub
|
Connections with remote locations where a small code footprint is required or the network bandwidth is limited
|
|
Advanced Message Queuing Protocol
(AMQP)
|
AMQP 1.0 a binary application layer protocol to support messaging and communication patterns
|
SO/IEC 19464
|
Pub/sub with broker with broker being either exchange or queue type
|
Mostly used for financial industry applications
|
|
Constrained Application Protocol
(CoAP)
|
Built on UDP and easy translation to HTTP and multicast
|
RFC 7252/7228
|
Functionalities specific for IoT and M2M applications
|
Intended for use in resource-constrained internet devices, such as wireless sensor network (https://en.wikipedia.org/wiki/Wireless_sensor_network) nodes
|
|
HTTP
|
HTTP/1.1 HTTP/2.0 application protocol
|
RFC 2616
|
Utilizes TCP but can be modified to use UDP
|
Standard request response for WWW
|
Common cloud protocols
The second important piece is the Connectivity layer, which connects all edge-related technologies to each other and further to the cloud. Often times, the IoT device network is geographically dispersed and edges require multiple carrier relationships for secure Quality of Service (QoS) enabled networks. This requires policy driven connectivity, security, and QoS for the edge components and additionally policy authoring, management, and deployment on the cloud. Mobile sites require selection of networks based on cost, availability, and bandwidth in a dynamically changing environment.
In order to achieve this, we need a connectivity layer that is aware of IIOT applications and data semantics; a layer that is a Software Defined Network (SDN) and based on Machine to Machine (M2M) and Machine to Client (M2C) communications. Variable network characteristics of M2M and M2C require adaptable traffic shaping based on the nature of applications. Carrier-agnostic, QoS-enabled secure tunnels for M2M and M2C connectivity are required.
The third type of technologies is the cloud analytics platform capabilities that will process and analyze the data coming from the edge devices. The analytical platform provides capabilities to ingest, store, search, analyze, and finally visualize or consume data. The different types of technologies that enable each of these capabilities are required as part of this analytics stack. The requirements for each part of the stack are varied as well. For example, different types of ingestion capabilities, such as real-time ingestion, batch ingestion, and change data capture ingestion are required to be part of the complete stack. Similarly, the storage requirements for different types of data are different. For example, time series data requires NoSQL databases and image data requires Blob storage. A partial list of these capabilities is shown in the Common protocols utilized at the edge table, which gives an idea of the variety of technologies that are required to complete the stack.
 United States
United States
 United Kingdom
United Kingdom
 India
India
 Germany
Germany
 France
France
 Canada
Canada
 Russia
Russia
 Spain
Spain
 Brazil
Brazil
 Australia
Australia
 Argentina
Argentina
 Austria
Austria
 Belgium
Belgium
 Bulgaria
Bulgaria
 Chile
Chile
 Colombia
Colombia
 Cyprus
Cyprus
 Czechia
Czechia
 Denmark
Denmark
 Ecuador
Ecuador
 Egypt
Egypt
 Estonia
Estonia
 Finland
Finland
 Greece
Greece
 Hungary
Hungary
 Indonesia
Indonesia
 Ireland
Ireland
 Italy
Italy
 Japan
Japan
 Latvia
Latvia
 Lithuania
Lithuania
 Luxembourg
Luxembourg
 Malaysia
Malaysia
 Malta
Malta
 Mexico
Mexico
 Netherlands
Netherlands
 New Zealand
New Zealand
 Norway
Norway
 Philippines
Philippines
 Poland
Poland
 Portugal
Portugal
 Romania
Romania
 Singapore
Singapore
 Slovakia
Slovakia
 Slovenia
Slovenia
 South Africa
South Africa
 South Korea
South Korea
 Sweden
Sweden
 Switzerland
Switzerland
 Taiwan
Taiwan
 Thailand
Thailand
 Turkey
Turkey
 Ukraine
Ukraine







