Configuring Entra ID MDM/MAM scopes
The last thing we must do before we move on to Intune is allow our users to enroll devices into Mobile Device Management (MDM) and, if required, Mobile Application Management (MAM).
MDM is for enrolling your corporate-owned devices into Intune, while MAM is for your bring-your-own devices (BYODs). MAM uses Windows Information Protection (WIP), which is only supported on Android and iOS, but we can block personal Windows devices within Intune so that we can still set this to everyone and let Intune handle the rest.
How to do it…
Follow these steps to configure your Entra ID MDM and MAM scopes:
- Within Microsoft Entra ID, expand Settings and click on Mobility.
- Within the Mobility portal, click Microsoft Intune:
Figure 1.12 – The Mobility (MDM and MAM) screen
- For this environment, set them both to All. Note you can restrict by groups – for example, only allowing users with an Intune license based on a dynamic group, or block users from enrolling completely. Leave the default URLs as is and then click Save.
With that, we have configured our Microsoft Entra environment for device enrollment.
Automating it
This is a tricky one to automate. Not only does it use the IAM API that we used for ESR, but the MDM application ID is also tenant-specific.
Let us build a PowerShell script to automate these settings:
- First, in your browser window, look in the address bar and grab the ID:
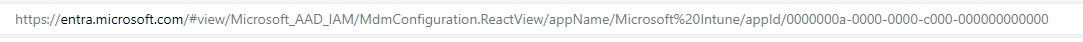
Figure 1.13 – Address bar object ID
- Set the necessary variables, including this ID. A setting of
2means enabled for all, while0means disabled:$MDMstatus = 2 $MAMstatus = 2 $policyid = "Policy ID grabbed from browser"
- Populate the JSON. As with the Entra ID device settings, we are manipulating the default values so that we can retrieve the current JSON with a
GETrequest. In this case, we are only changing two settings; everything else remains the same:$json = @" { "appCategory": "Mdm", "appData": { "complianceUrl": "https://portal.manage.microsoft.com/?portalAction=Compliance", "enrollmentUrl": "https://enrollment.manage.microsoft.com/enrollmentserver/discovery.svc", "mamComplianceUrl": "", "mamEnrollmentUrl": "https://wip.mam.manage.microsoft.com/Enroll", "mamTermsOfUseUrl": "", "termsOfUseUrl": "https://portal.manage.microsoft.com/TermsofUse.aspx" }, "appDisplayName": "Microsoft Intune", "appId": "0000000a-0000-0000-c000-000000000000", "isOnPrem": false, "logoUrl": null, "mamAppliesTo": $MAMstatus, "mamAppliesToGroups": [], "mdmAppliesTo": $MDMstatus, "mdmAppliesToGroups": [], "objectId": "$policyid", "originalAppData": { "complianceUrl": "https://portal.manage.microsoft.com/?portalAction=Compliance", "enrollmentUrl": "https://enrollment.manage.microsoft.com/enrollmentserver/discovery.svc", "mamComplianceUrl": "", "mamEnrollmentUrl": "https://wip.mam.manage.microsoft.com/Enroll", "mamTermsOfUseUrl": "", "termsOfUseUrl": "https://portal.manage.microsoft.com/TermsofUse.aspx" } } "@ - Set the URL:
$url = "https://main.iam.ad.ext.azure.com/api/MdmApplications /$policyid?mdmAppliesToChanged=true&mamAppliesToChanged=true"
- Authenticate against the IAM API:
##Create Access Token $clientid = "1950a258-227b-4e31-a9cf-717495945fc2" $response = Invoke-RestMethod -Method POST -UseBasicParsing -Uri "https://login.microsoftonline.com/$tenantId/oauth2/devicecode" -ContentType "application/x-www-form-urlencoded" -Body "resource=https%3A%2F%2Fmain.iam.ad.ext.azure.com&client_id=$clientId" Write-Output $response.message $waited = 0 while($true){ try{ $authResponse = Invoke-RestMethod -uri "https://login.microsoftonline.com/$tenantId/oauth2/token" -ContentType "application/x-www-form-urlencoded" -Method POST -Body "grant_type=device_code&resource=https%3A%2F%2Fmain.iam.ad.ext.azure.com&code=$($response.device_code)&client_id=$clientId" -ErrorAction Stop $refreshToken = $authResponse.refresh_token break }catch{ if($waited -gt 300){ Write-Verbose "No valid login detected within 5 minutes" Throw } #try again Start-Sleep -s 5 $waited += 5 } } $response = (Invoke-RestMethod "https://login.windows.net/$tenantId/oauth2/token" -Method POST -Body "resource=74658136-14ec-4630-ad9b-26e160ff0fc6&grant_type=refresh_token&refresh_token=$refreshToken&client_id=$clientId&scope=openid" -ErrorAction Stop) $resourceToken = $response.access_token - Create the headers:
$Headers = @{ "Authorization" = "Bearer " + $resourceToken "Content-type" = "application/json" "X-Requested-With" = "XMLHttpRequest" "x-ms-client-request-id" = [guid]::NewGuid() "x-ms-correlation-id" = [guid]::NewGuid() } - Configure the policy:
Invoke-RestMethod -Uri $url -Headers $Headers -Method PUT -Body $json -ErrorAction Stop
We now have a script to amend the MDM and MAM enrollment scopes.
































































