Implementing Azure AD tenant Identity and Access Management
Account compromise is one of the biggest threat vectors to protect against, and those with privileged access roles will be the focus of attacks. There are often too many users assigned privileged accounts, with more access than is required for a user to carry out their role. There is often insufficient RBAC in place, and the principle of least privilege should be adopted for these privileged administrator roles.
While we need to limit the number of user accounts that have the Global Administrator role, there should also not be a single point of compromise for the Global Administrator role. Having more than one account with the Global Administrator role is important. It is crucial to have an emergency account in case of a breach or conditional access lockout of a Global Administrator role assigned. Global Administrator role accounts can use a buddy system to monitor each other’s accounts for signs of a breach.
This recipe will teach you to ensure you only have the users assigned with the least privileges required for their role and ensure you have a minimum of two accounts assigned the Global Administrator role.
We will take you through the steps to implement these tasks.
Getting ready
This recipe requires the following:
- A device with a browser, such as Edge or Chrome, to access the Azure portal: https://portal.azure.com
- You should sign in with an account that has the Global Administrator role
How to do it…
This recipe consists of the following tasks:
- Implementing least privileged administrative roles
- Designating more than one Global Administrator
Task – implementing least privileged administrative roles
Perform the following steps:
- From the Azure portal, go to Azure Active Directory | Roles and administrators.
- From the All roles section, select the Global administrator role:
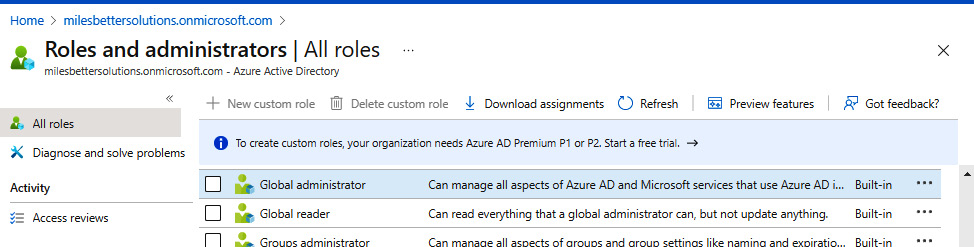
Figure 1.8 – Azure AD Roles and Administrators screen
- From the Assignments section, identify only the accounts required to have the Global Administrators role; ensure you have at least two or no more than five accounts with the Global Administrator role.
Select a user for users who no longer require the Global Administrator role and then click Remove assignments from the top toolbar:
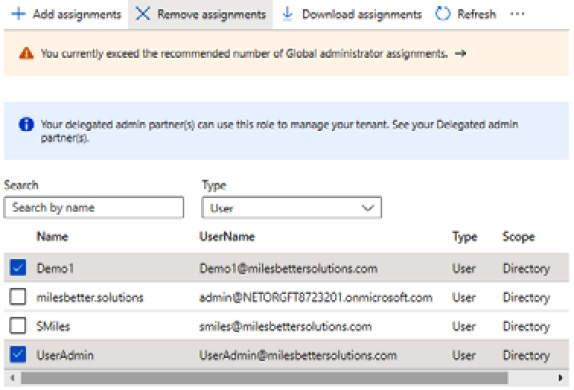
Figure 1.9 – The Remove assignments screen
- From Azure Active Directory | Roles and administrators | All roles | Global administrator, we can now see that the user has been removed from the Global Administrator role:
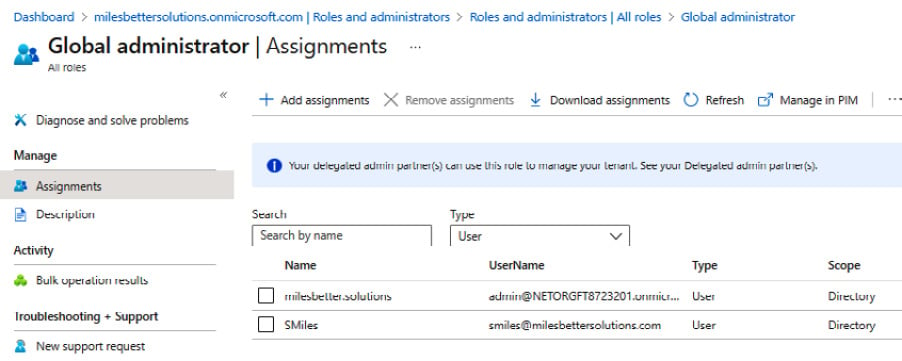
Figure 1.10 – Global Administrator Assignments screen
- To reassign least privileged admin users to roles required to complete their tasks, navigate to Azure Active Directory | Users. Select and click the users to assign roles.
- From the User blade for the user selected to assign a directory role, go to Assigned roles from the Manage section and click Add assignments:
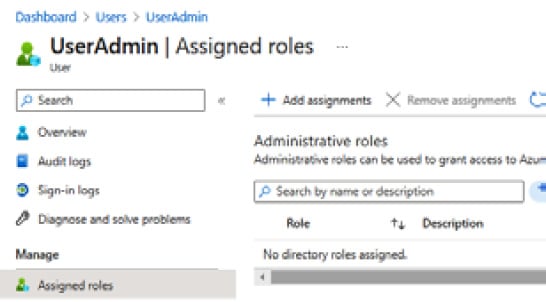
Figure 1.11 – The Assigned roles screen
- From the Directory roles pop-up screen, locate the directory role you wish to assign from the list of all available roles; select the directory role to assign and click Add:
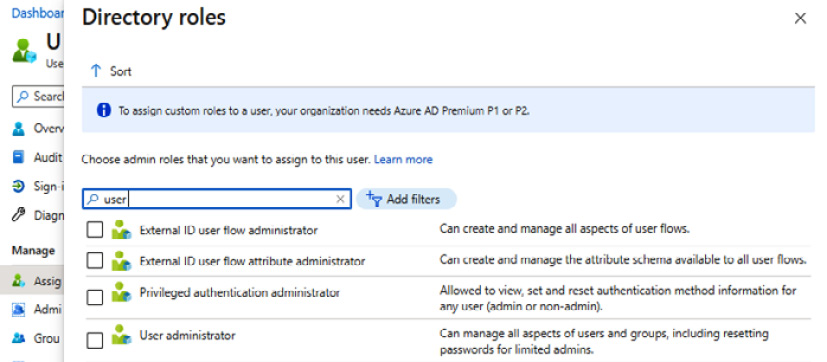
Figure 1.12 – The Directory roles assignment screen
- Your user will now have the required least privileged admin role assigned and no longer have the highly privileged Global Administrator role:
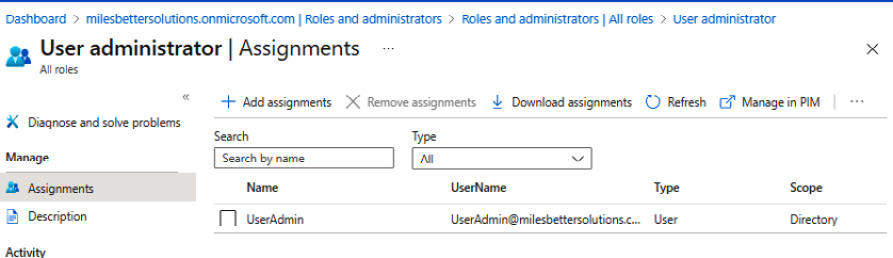
Figure 1.13 – User administrator | Assignments
With that, you have learned how to use least privileged roles. In the next task, we will designate more than one Global Administrator for the tenancy.
Task – designating more than one Global Administrator
Perform the following steps:
- From the Azure portal, go to Azure Active Directory | Roles and administrators | All roles | Global Administrator.
- From the Assignments blade, click Add assignments and locate the user(s) to add to the Global Administrators role:
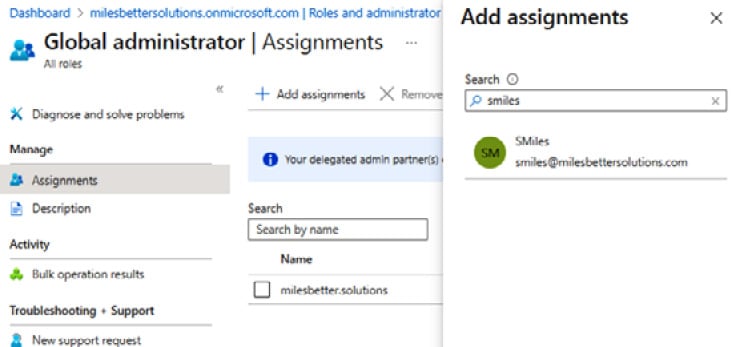
Figure 1.14 – Global administrator – the Add assignments screen
- Select the user, and then click Add:
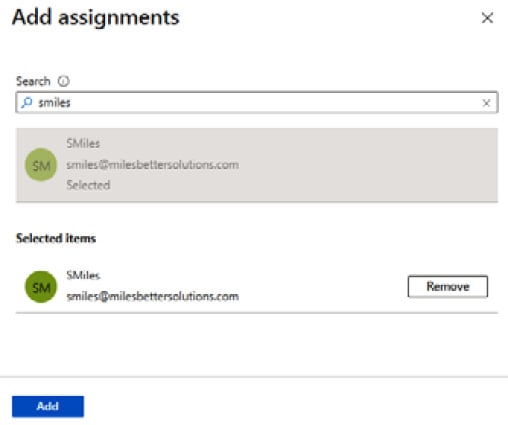
Figure 1.15 – Global administrator – The Add assignments screen
- You will now see that the user(s) have been assigned the Global Administrator role:
Figure 1.16 – Global administrator | Assignments
With that, you have created more than one Global Administrator role. This concludes the hands-on tasks for this recipe.
How it works…
In this recipe, we looked at limiting the number of users with the Global Administrator role and ensuring you only had the users assigned with the least required privileges for their role. In our example, we removed the Global Administrator role from a user and reassigned them to the User Administrator role, which was the least privileges required for their tasks.
We then ensured you had a minimum of two accounts assigned the Global Administrator role by adding a user to this role. The Microsoft recommendation is for a minimum of two users and no more than five for this role.
There’s more…
Azure AD user accounts with the highest privileged role of Global Administrator will be the primary goal for compromise by bad actors. This is because this role has access to every administrative setting in your environment’s Azure AD tenancy at the read and modify permission level.
Microsoft recommends that you assign user accounts with less privileged roles. This limits the user’s scope of permissions through RBAC to only be able to do what a user needs to do for their job function.
The following are some of the many roles that can be considered to reduce the use of the Global Administrator role but still have enough access for a user to be able to perform their duties:
- Application Administrator
- Authentication Administrator
- Azure DevOps Administrator
- Azure Information Protection Administrator
- Billing Administrator
- Compliance Administrator
- Conditional Access Administrator
- Directory Readers
- Exchange Administrator
- SharePoint Administrator
- Privileged Role Administrator
- Security Administrator
- User Administrator
Should you require further information on least privileged roles, you can refer to the following Microsoft Learn articles:
- Assigning Azure roles using the Azure portal: https://learn.microsoft.com/en-us/azure/role-based-access-control/role-assignments-portal
- Azure AD built-in roles: https://learn.microsoft.com/en-us/azure/active-directory/roles/permissions-reference
- What are the default user permissions in Azure Active Directory?: https://learn.microsoft.com/en-us/azure/active-directory/fundamentals/users-default-permissions
- Least privileged roles by task in Azure Active Directory: https://learn.microsoft.com/en-us/azure/active-directory/roles/delegate-by-task
See also
Should you require further information, you can refer to the following Microsoft Learn articles:
- Best practices for Azure AD roles: https://learn.microsoft.com/en-gb/azure/active-directory/roles/best-practices
- Restrict member users’ default permissions: https://learn.microsoft.com/en-gb/azure/active-directory/fundamentals/users-default-permissions#restrict-member-users-default-permissions
- Azure Active Directory fundamentals documentation: https://learn.microsoft.com/en-us/azure/active-directory/fundamentals

























































