Securing cloud-based workloads with Microsoft Entra’s identity-based access control
When transitioning workloads to the cloud, companies must consider the security implications of moving their resources. They need to define authorized users, restrict access to data, and ensure that employees and vendors only perform authorized operations. To centrally control access to cloud-based workloads, companies must establish a definitive identity for each user used for every service. This identity-based access control ensures that users have the necessary permissions to perform their jobs while restricting unauthorized access to resources.
Microsoft Entra comprises a set of multiple components, including the following:
- Azure AD
- Microsoft Entra Permissions Management
- Microsoft Entra Verified ID
- Microsoft Entra workload identities
- Microsoft Entra Identity Governance
- Microsoft Entra admin center
Let’s look at them in detail.
Azure AD
To simplify the process of securing cloud-based resources, Azure AD, a cloud-based IAM service that is part of Microsoft Entra, offers features such as SSO and MFA, which helps protect both users and data. By learning the basics of creating, configuring, and managing users and groups of users, organizations can effectively control access to their cloud-based resources. Additionally, by managing licenses through Azure AD, organizations can ensure that their employees and vendors have access to the necessary tools to perform their jobs while maintaining a secure environment.
Azure AD provides three ways to define users, which are helpful for different scenarios. The first way is cloud identities, which only exist in Azure AD. These can include administrator accounts and users managed directly in Azure AD. Cloud identities are deleted when removed from the primary directory, making them an excellent option for managing temporary access to Azure resources. The following figure represents the cloud identity.
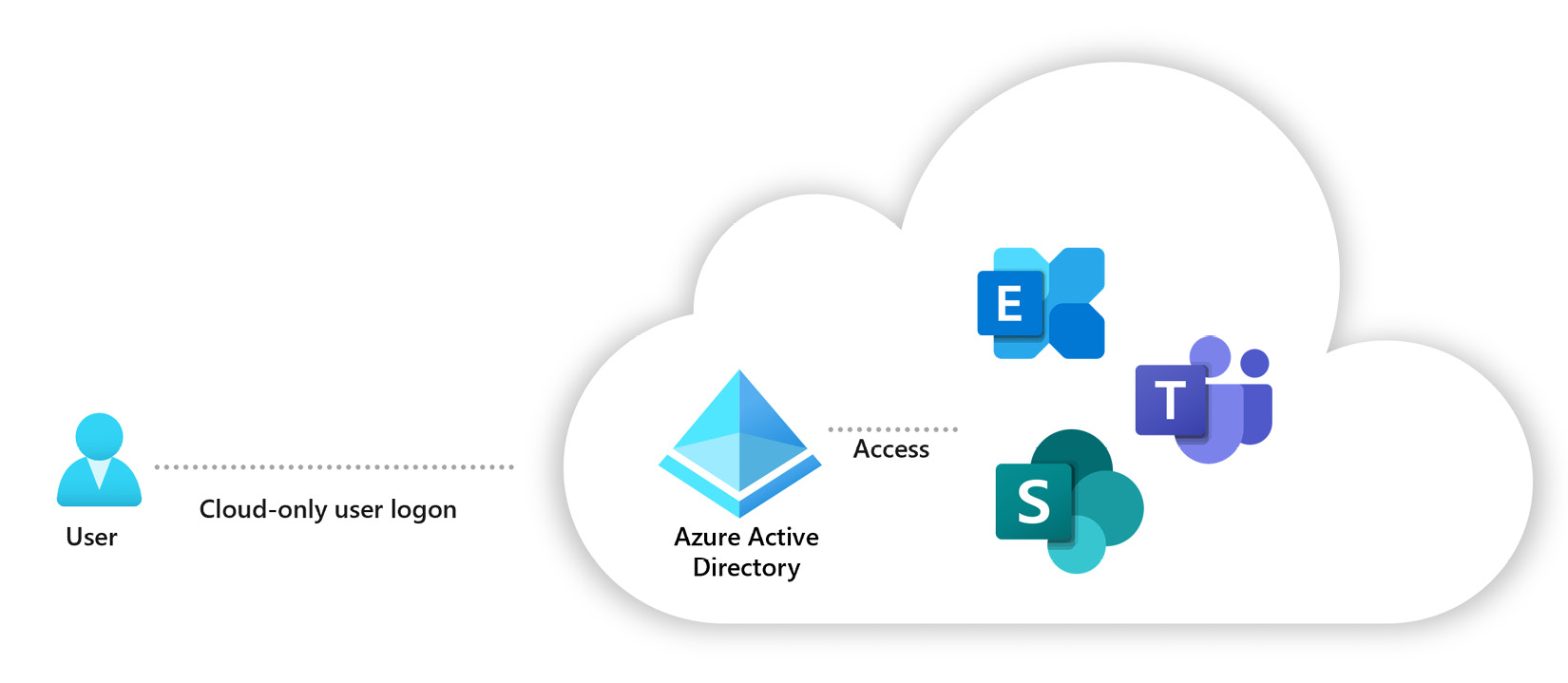
Figure 1.3 – Cloud identity
The second way is directory-synchronized identities, which exist in an on-premises AD. These users are brought into Azure through a synchronization activity with Azure AD Connect, making them useful for organizations with existing on-premises infrastructure.
You can leverage directory synchronization with Pass-through Authentication (PTA) or SSO with AD FS.
Finally, there are guest users that might exist outside of Azure or can be on a different Azure AD tenant. These can be accounts from other cloud providers or Microsoft accounts, such as an Xbox Live account. Guest users are invited to access Azure resources. They can be removed once their access is no longer necessary, making them an excellent option for external vendors or contractors who require temporary access.
Managing permissions is a critical aspect of Zero Trust security and is increasingly challenging for organizations adopting a multi-cloud strategy. With the proliferation of cloud services and identities, high-risk cloud permissions are exploding, creating a larger attack surface for organizations. IT security teams are pressured to ensure access to their expanding cloud estate is secure and compliant. However, the inconsistency of cloud providers’ native access management models makes it even more complex for security and identity teams to manage permissions and enforce least privilege access policies across their entire environment.
Microsoft Entra Permissions Management
Organizations need a cloud infrastructure entitlement management (CIEM) solution such as Microsoft Entra Permissions Management to enable comprehensive visibility into permissions assigned to all identities across multi-cloud infrastructures such as Microsoft Azure, AWS, and Google Cloud Platform (GCP). Microsoft Entra Permissions Management can detect and right-size unused and excessive permissions while continuously monitoring permissions to maintain a least privilege access policy. By implementing a CIEM solution such as Permissions Management, organizations can improve their cloud security posture and better manage access to their cloud-based resources.
Microsoft Entra Verified ID
The digital identity we use today is controlled by other parties, leading to potential privacy concerns. Users give apps and devices access to their data, making it challenging to track who has access to which information. Securely exchanging data with consumers and partners is difficult in the enterprise world. A standards-based decentralized identity system can improve user and organizational control over data, resulting in increased trust and security for apps, devices, and service providers.
Decentralized identifiers (DIDs) are a key component of verifiable credentials (VCs) in Azure AD. DIDs are unique identifiers created in a decentralized system and are not controlled by a central authority. DIDs can be used to represent individuals, organizations, devices, and other entities in a secure and privacy-preserving way. They can also be used to prove ownership of digital assets, such as domain names or social media handles.
Azure AD supports using DIDs and VCs to enable secure and trusted digital identities. This allows organizations to reduce the reliance on traditional usernames and passwords and instead use more secure and privacy-preserving methods for identity verification. The article also highlights the benefits of using DIDs and VCs, including increased security, privacy, and interoperability. It provides resources for developers and organizations to use DIDs and VCs in Azure AD.
Microsoft Entra workload identities
In the world of cloud computing, a workload identity is essential for authenticating and accessing other resources and services securely and efficiently. Workload identities can take different forms, such as a user account that an application uses to access a database or a service role attached to an instance with limited access to a specific resource. Regardless of its form, a workload identity ensures that the software entity can securely access the resources it needs while also helping to prevent unauthorized access and data breaches.
In Azure AD, a workload identity is a way for a software program, such as an application or service, to identify and authenticate itself when accessing other services and resources. There are three types of workload identities in Azure AD: applications, which are like templates that define how a program can access resources; service principals, which are like local copies of applications that are specific to a particular tenant; and managed identities, which are a special type of service principal that don’t require a developer to manage passwords or credentials.
Here are a few examples of how you can leverage workload identities:
- You can use a managed identity to access resources protected by Azure AD without the need to manage credentials or keys to authenticate your identity
- You can use workload identity federation to access Azure AD-protected resources without needing to manage secrets or credentials for workloads running in supported scenarios such as GitHub Actions, Kubernetes, or compute platforms outside Azure
- You can use access reviews for service principals to review and audit the access of service principals and applications assigned to privileged directory roles in Azure AD
- You can leverage Conditional Access policies for workload identities to control access to resources based on certain conditions or policies and use continuous access evaluation to monitor and evaluate access to resources in real time
- You can use Identity Protection to detect and respond to identity-related risks and threats for your workload identities and apply security policies to protect your identities from cyberattacks
As organizations embrace digital transformation, the need for the secure and efficient management of access to resources becomes increasingly important. Microsoft Entra Identity Governance is a tool designed to address this need, enabling companies to balance productivity and security by ensuring the right people have access to the right resources. Identity Governance uses a foundation of identity life cycle management to keep track of who has access to what resources and ensure that access is updated as needed.
Microsoft Entra Identity Governance
Microsoft Entra Identity Governance is a tool that helps organizations balance the need to keep their data secure and ensure employees can get their work done efficiently. It helps by ensuring the right people have access to the right things, and the company can keep an eye on who is accessing what. This helps reduce the risk of someone getting access to something they shouldn’t have and helps the company ensure employees can still do their jobs.
Identity Governance helps organizations to manage access to their resources in a way that balances productivity and security. It is designed to answer questions such as “Who should have access to which resources?” and “How can we ensure that access is appropriate and secure?” To do this, Identity Governance relies on a foundation of identity life cycle management, which involves keeping track of who has access to what resources and making sure that access is updated as needed. This process helps organizations ensure that their resources are protected while enabling their employees to get the access they need to do their jobs.
Sometimes, organizations need to work with people outside of their own company. Azure AD B2B collaboration is a feature that allows companies to safely share their apps and services with other people, such as guests and partners from different organizations. This way, organizations can maintain control over their own data while still allowing others to use their resources. Microsoft Entra entitlement management will enable organizations to decide which users from other organizations can request access and become guests in their directory. It will also remove these guests when they no longer need access.
Microsoft Entra admin center
Microsoft launched the Entra admin center for its Microsoft 365 and Azure AD customers. And you can log in to the portal using your Microsoft 365 account. The Entra admin center provides customers with better security, governance, and compliance features for their organization.
The portal is accessible through the following URL: https://entra.microsoft.com.
As you can see, Microsoft Entra helps organizations to make sure the right people have access to the right things. It does this by verifying who someone is and allowing them to access the apps and resources needed to do their job. Microsoft Entra works across different environments, such as cloud and on-premises systems. It also makes it easier for people to access what they need by using smart tools to make quick decisions about who should have access to what.