Setting your PowerShell Execution Policy
As you've hopefully already seen, Windows PowerShell can be an extremely powerful tool for server management. Windows and PowerShell are fully intertwined, and PowerShell can be useful for so many tasks on your servers. However, the ability to run PowerShell scripts is disabled by default on many machines. The first stumbling block that many new PowerShell administrators bump into is the execution policy. It's quite simple: in order to allow PowerShell scripts to run on your server, the execution policy must be adjusted to allow that to happen. Let's introduce our first task in PowerShell by using some commands in this recipe that will set this policy for us.
This is also a good introduction to the idea of the verb-noun syntax that PowerShell utilizes. For example, we are going to make use of cmdlets called Get-ExecutionPolicy and Set-ExecutionPolicy. The Get and Set verbs are very common across all facets of cmdlets available in PowerShell. Wrap your mind around this verb-noun syntax and you will be well on your way to figuring out PowerShell on your machines.
Getting ready
We will be working within a PowerShell prompt on our Windows Server 2019 server.
How to do it…
Follow these steps to set the PowerShell execution policy:
- Right-click on the PowerShell icon and choose Run as administrator:

Figure 1.29 – Running PowerShell as administrator
- Type
Get-ExecutionPolicyand press Enter in order to see the current settings for the PowerShell execution policy:
Figure 1.30 – Running Get-ExecutionPolicy
- You can see that the current execution policy is set to RemoteSigned. Here is a short description of the different options for the policy:
Remote Signed: This is the default setting in Server 2019 and allows PowerShell scripts that are locally created to run. If you try running remote scripts (for example, downloaded from the internet), they must be signed by a trusted publisher in order to execute successfully.
All Signed: With this setting, all scripts will only be allowed to run if they are signed by a trusted publisher.
Restricted: With this setting, PowerShell is locked down so that scripts will not run.
Unrestricted: This setting will allow PowerShell to run scripts with or without signing.
- For the purposes of our recipe and to make sure the scripts will run for us as we progress through these recipes, let's set our execution policy to unrestricted. Go ahead and use this command:
Set-ExecutionPolicy Unrestricted
The following is the output:
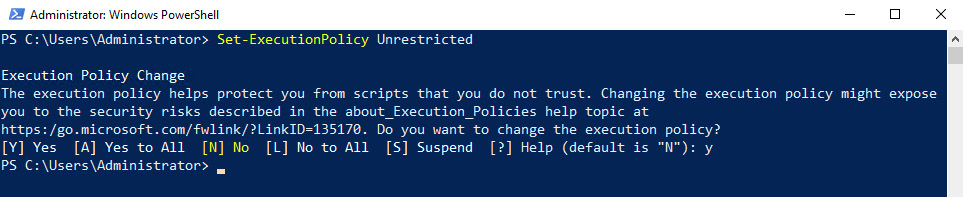
Figure 1.31 – Output of Set-ExecutionPolicy
How it works…
The PowerShell execution policy is a simple setting and easy to change, but can make a world of difference when it comes to running your first scripts. If configured to be more restrictive than you intend, you will have trouble getting your scripts to run and you may think that you have mistyped something, when in fact the issue is only the policy. On the other hand, in an effort to make your servers as secure as possible, on machines where you don't need to execute PowerShell scripts, it makes sense to restrict this access. You may also want to read some additional information on the signing of scripts to see whether creating and executing signed scripts would make more sense in your own environment. There are some in-built server functions that rely on a certain level of security with your execution policy. Setting your policy to unrestricted on all your servers could result in some functions not working properly, and you may have to increase that level of security back to remote signed.


























































