Becoming a successful hacker
In order to become a successful penetration tester, you will need a specific skill set. The first thing you will need is a strong desire to learn new technologies. The world of computing is changing at a very rapid pace and every few years, old tools and technologies are replaced. You can't use one successful exploit and expect it to be useful 10 years down the line. This book will focus mostly on developing your own tools. You won't be able to hack NASA with the tools developed in this book and that is not the idea of this book. This book is meant to serve as a starting point for you. The knowledge of the techniques and tools described in this book will help you to get started and then the sky is the limit.
The first thing you need in order to become successful in this field is knowledge of computer systems and computer networks. You won't be able to get very far without them. This book assumes that you have familiarity with computer networks and so on. When necessary, new terms will be explained. This book also assumes that you have a fundamental knowledge of the Python programming language. We will use Python 3 in this book.
Knowledge of these two components should be enough to follow this book. The world of penetration testing is quite huge and to be a hacker that stands out among the crowd, you will need to master a lot of technologies. This includes Linux, databases, hardware and memory access, reverse engineering, cryptography, networking, and analytical skills. You should be proactive and be able to think quickly on your feet if you want to be successful.
Most of the systems present today are online and web-based hacking is one of the most prevalent forms of penetration testing. This means that knowledge of how the web works is essential in order to become a penetration tester. Fundamental knowledge of web-based technologies such as HTML, JavaScript, PHP, and SQL is essential. These topics will not be covered in this book as they do not fit into the scope of the book; however, in practical life, knowledge of these tools is quite useful for penetration testing.
One of the critical skills needed for a successful ethical hacker is to think like a hacker. So, what does it means to think like a hacker? The goal of hackers is to break into a system. A computer system is designed in an intuitive way so most people will be able to interact with it using minimal effort. All the security aspects of a system are designed with this methodology in mind. To be able to break into a system, your thinking process should be somewhat counter-intuitive or rather creative. You need to be able to identify weak points to be attacked that could help you to compromise the system.
Creating a tool that could help you to attack some system is one side of the hacking process while being able to successfully deploy your malware onto the target system without being detected is the other half of the equation. This is almost as important as the hacking tool itself. Once you identify a target, your goal will be to think of a methodology by which you can deploy it to the system. There are many methods of deploying your code depending on what kind of access you can get to the system. These methods, such as phishing and Trojan horses, will be discussed later. Don't worry if these terms sound unfamiliar to you. Once you have gone through this book, you will be familiar with most of these terms.
Hacking requires you to be constantly up to date with the new technologies. The landscape in cybersecurity changes very abruptly and you need to be well versed in these changes. A good idea is to follow forums and websites dedicated to these matters. Hundreds of exploits are discovered and patched every day; you need to be at the right place at the right time to take advantage of them. The window of opportunity is often very small. A term commonly used in the cybersecurity space is zero-day exploit. Zero-day exploit refers to a vulnerability that has not been patched yet. Often, a very limited number of people are aware of these and they tend to not disclose them so they can take maximum advantage of them. Once an exploit is out in the public, chances are that it will be patched very quickly, in some instances even in a couple of days:
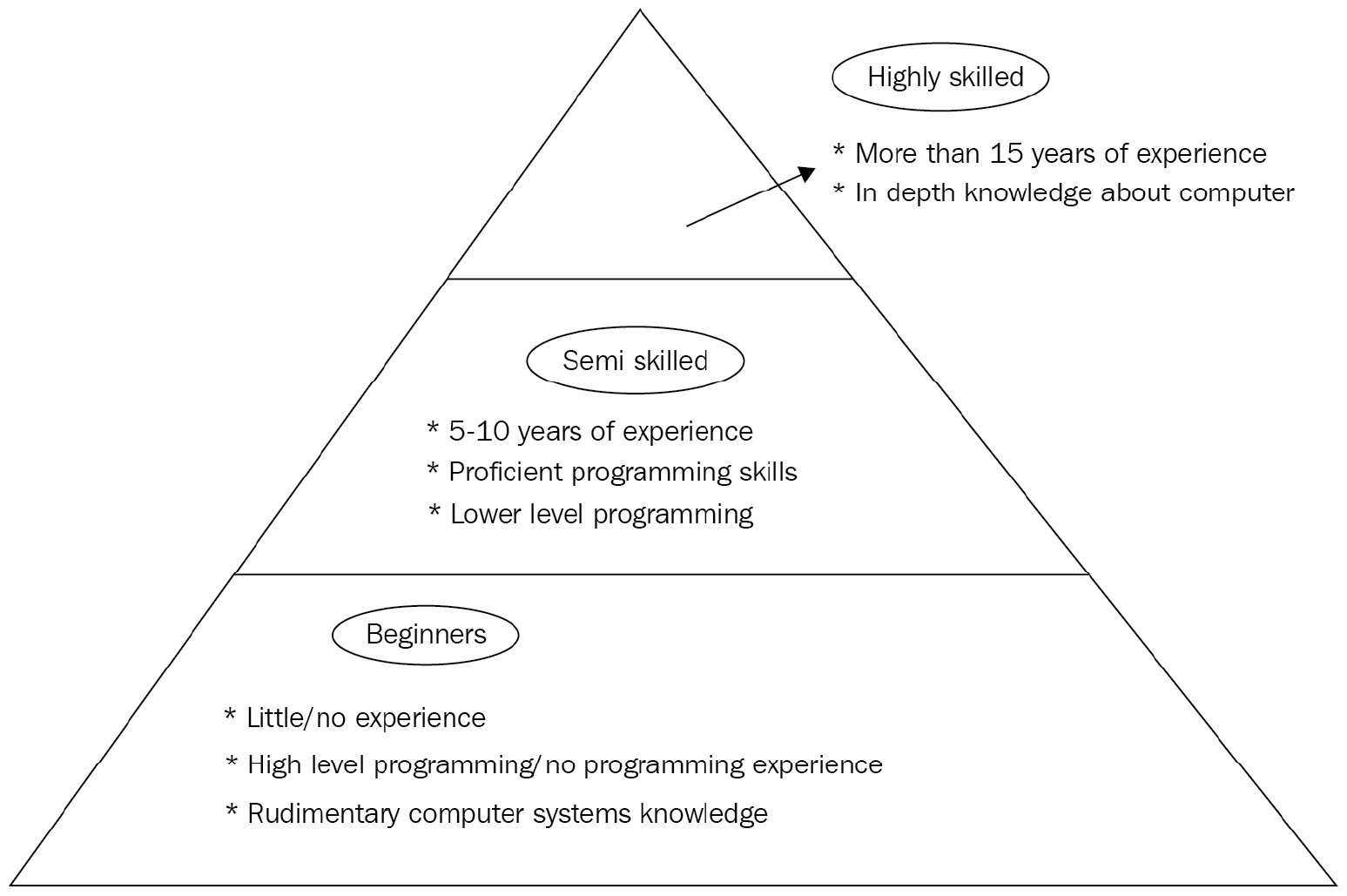
Figure 1.5 – Hacking skills pyramid
The preceding diagram shows the skills pyramid according to the expertise of an ethical hacker. Reaching the top requires a combination of experience, analytical skills, and, most importantly, in-depth knowledge of computer systems.
Legality
The rule of thumb in penetration testing is that you should not be attacking a system you are not supposed to. Even if you work in a cybersecurity firm as a penetration tester, you must get written permission in order to test out the security of the system. Without written consent, you can get into a lot of legal trouble. Penetration testing often involves attacking the system with different attack vectors, which could often result in breaking the system. If you do not have prior permission, you will be liable for damages caused to their infrastructure.
Pen-testing encompasses a wide variety of tests. In practical cases, the written contract of consent for testing must explicitly define the scope of the test. It should mention what type of tests will be performed and what systems/assets will be targeted in the test. The testing should strictly remain confined to these predefined objectives. For example, testing for software code should not include testing the network security unless explicitly mentioned.
Pen-testing could be done on production or live systems. If the asset under test is a live system, the user must be properly notified regarding the test and the potential damages associated with the test. Pen-testing is performed in different environments. Sometimes the users in the organization are aware of the pen-testing going on, and in other cases, only the top management knows about it so that they can test which individuals are a potential threat to the organization. If the users in the organization are already aware that a pen-test will be performed, it is a good idea to notify them in advance of the time of the test so that it doesn't interfere with the day-to-day activities of the organization. Next, let's learn about the types of hackers.


























































