Focusing on zero trust
Within only a couple of years since the first edition of the book was released, zero trust has gained tremendous momentum and has become a buzz and marketing term for most security vendors. As a reminder, the zero-trust architecture model was created by John Kindervag while he was at Forrester Research Inc. back in 2009. If you are not clear on what exactly zero trust is, essentially, it is a model where we trust no one until we can validate who they are, who they are meant to be, and whether they are authorized to have access to the system or information. In simple terms, zero trust is well known for the concept of never trust, always verify.
There are a lot of zero trust references from many vendors, and depending on which vendor you work with, there will be slight differences in their approach to zero trust. No matter which vendor you work with or which approach you take, the core of a zero-trust model will always fall back on the principle of never trust, always verify. Effectively implementing a zero-trust model requires a multilayered approach with your security strategy, along with the use of the most current and modern technology available. The method of allowing a user to access the environment with only a username and password is outdated and insecure.
Since we are focusing our security on Microsoft products, we will review zero trust as Microsoft has approached it. With Microsoft’s approach to zero trust, they have created their strategy for customers around six different pillars, as follows:
- Identities are the new perimeter of zero trust. An identity is something (typically a user) that needs to access an app, data, or some other form of resource. It is critical that identities have multiple layers of protection to prevent unauthorized access.
- Device and endpoint protection is an essential component of zero trust. Whether a mobile device, laptop, server, IoT, and so on, we need to ensure recommended baselines are deployed and that devices stay compliant and are constantly being scanned for vulnerabilities.
- Data is at the core of the zero-trust model. It is ultimately data that the intruders are looking to exfiltrate from your environment. This is the true asset that needs to be protected. Because of this, it is critical that you know where all your data lives, who has access to it; whether it’s classified correctly and encrypted, and that you have the correct controls to prevent it from being removed from your environment.
- Applications and application programming interfaces (APIs) are gateways to your data. They need to be governed and deployed with best practices to prevent unauthorized access to data, whether intentionally or unintentionally. Ensuring the business is following enterprise standards is critical for preventing shadow IT.
- Infrastructure pertains to everything within your environment that provides the means to store your data and/or run applications such as servers, VMs, appliances, Infrastructure as a Service (IaaS), Platform as a Service (PaaS), and Software as a Service (SaaS). Preventing unwanted access to your infrastructure is crucial by ensuring you have best practices and baselines in place, along with effective monitoring.
- A network is a medium where your data travels. Once considered the perimeter for defense, this pillar still holds a critical role as part of zero trust to ensure all data is encrypted during transport, next-generation protection is deployed, micro-segmentation is in place, and ongoing monitoring is taking place to detect unauthorized access to your data in transit.
Information
You can read more about the zero-trust Microsoft model here: https://www.microsoft.com/en-us/security/business/zero-trust.
The following screenshot represents the six pillars, with some examples of the technologies and solutions that should be implemented to support your broader zero-trust strategy:
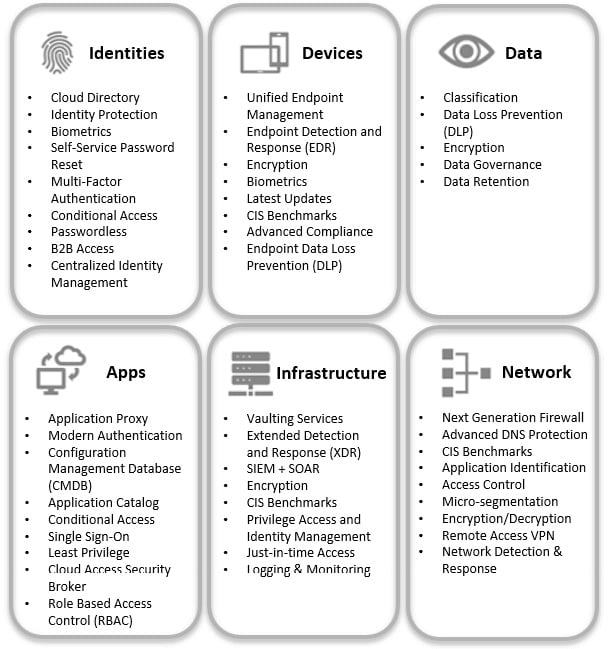
Figure 1.10 – Microsoft’s six pillars of zero trust
Now that you have an idea of what zero trust is and the technologies involved, you will need to have a plan in place to ensure success. Zero trust is not going to happen overnight or within a few weeks. Zero trust is a strategy and a foundation that needs to be planned over months or even years, depending on your organization’s maturity. With this, you will need to be able to measure your success, along with your current maturity. Microsoft has a very high-level and simplified maturity model that can help you better understand your current state and what will be needed to obtain zero trust. The following screenshot provides an example of how the Microsoft maturity model is presented:

Figure 1.11 – An example based on Microsoft’s zero-trust maturity model
For more details on the maturity model example, browse to https://download.microsoft.com/download/f/9/2/f92129bc-0d6e-4b8e-a47b-288432bae68e/Zero_Trust_Vision_Paper_Final%2010.28.pdf to view Microsoft’s maturity model with more details across all six pillars.
Once you have a good understanding of the technologies involved in zero trust and how the maturity model works, the next step is to build your strategy around accomplishing this transition. Remember—this transformation isn’t going to happen overnight, so you’ll need to build a roadmap based on where you are today with the technologies you have in place versus where you would like to be. Accomplishing this journey is not going to be easy, but the better you document your strategy and vision, the easier your journey will become. Here is a high-level idea of how you could build out your roadmap:
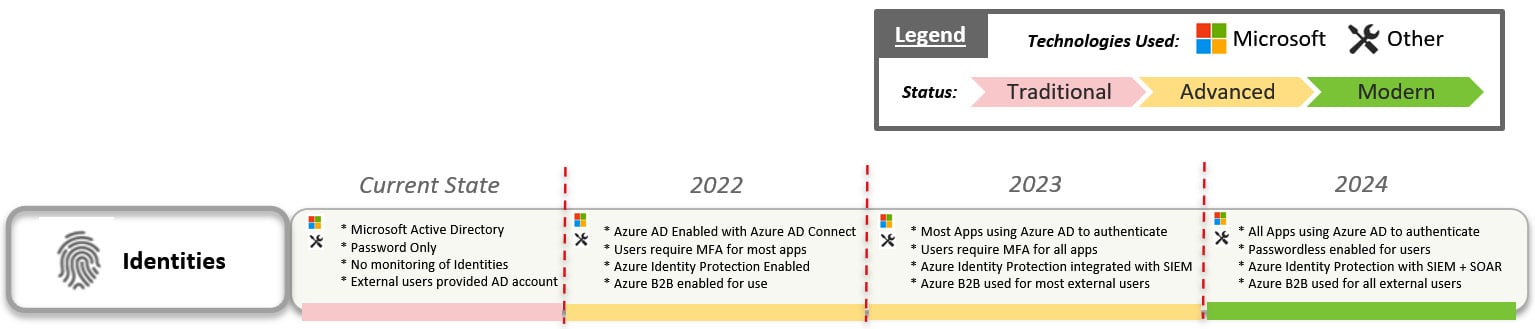
Figure 1.12 – Example of a zero-trust roadmap
There are many variations and vendors providing guidance on how to adopt a zero-trust approach. A couple of additional notable models to review as part of your planning include the NIST zero-trust architecture and the CISA zero-trust maturity model, as listed here:
- NIST zero trust: https://www.nist.gov/publications/zero-trust-architecture
- CISA zero trust: https://www.cisa.gov/publication/zero-trust-maturity-model
As you read through this book, you will find that the guidance and instructions provided will ultimately lead to a zero-trust model.
Tip
Microsoft also provides deployment guides to each of its pillars. The following link provides specific guidance to securing endpoints with zero trust. The same Uniform Resource Locator (URL) also has links to the other deployment guidelines for each of the pillars: https://docs.microsoft.com/en-us/security/zero-trust/deploy/endpoints.

























































