Chapter 4. Working with Mail Servers
In this chapter, we will cover the following recipes:
- Sending e-mails with Postfix
- Enabling IMAP and POP3 with Dovecot
- Adding e-mail accounts
- Mail filtering with spam-assassin
- Troubleshooting the mail server
- Installing the Zimbra mail server
Introduction
In this chapter, we will learn how to set up an e-mail server. We will be using Postfix MTA to send e-mails and Dovecot to enable receiving e-mails. We will also install the Zimbra e-mail server, which is all-in-one one package to set up sending and receiving e-mails and web access. By the end of this chapter, you will be able to send e-mails with your own e-mail server.
Sending e-mails with Postfix
In this recipe, we will set up Postfix Mail Transfer Agent (MTA). This will be a very basic setup which will enable us to send and receive e-mails from our server. Postfix is an open source MTA which routes e-mails to their destination. It is a default MTA for Ubuntu and is available in Ubuntu's main package repository.
Getting ready
You will need access to a root account or an account with sudo privileges.
A domain name (FQDN) is required while configuring Postfix. You can configure your local server for testing, but make sure that you set the proper host entries and hostname.
How to do it…
Follow these steps to send e-mails with Postfix:
- Install Postfix and
mailutilswith the following commands:$ sudo apt-get update $ sudo apt-get install postfix mailutils -y
- The installation process will prompt you to enter some basic configuration details. When asked for General type of mail configuration:, select Internet Site and then click on <Ok>:

- On the next screen, enter your domain name, for example,
mail.example.com, and answer the other questions. You can leave them with default values:
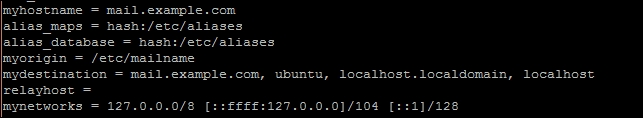
- After installation completes, we need to modify the Postfix configuration under
/etc/postfix/main.cf:$ sudo nano /etc/postfix/main.cf - Set
myhostnameto point to your domain name:myhostname = mail.example.com - Ensure
mynetworksis set to the local network. This will secure your server from spammers:mynetworks = 127.0.0.0/8 [::ffff:127.0.0.0]/104 [::1]/128
- Also check
mydestination. It should contain your domain name:mydestination = example.com, ubuntu, localhost.localdoma in, localhost
- Change the mail storage format to
Maildirfrom the defaultmbox. Search and uncomment the following line:home_mailbox = Maildir/ - Optionally, you can change the TLS keys used by Postfix. Find the
TLS parameterssection and point the variables to your key path:
- Save the configuration file and exit.
- Now, reload Postfix for the changes to take effect:
$ sudo service postfix reloadTest if everything is working as expected. Open a telnet connection to the mail server:
$ telnet localhost 25You should see an output similar to the following screenshot:

- Now, send your first e-mail from this server. Type
sendmail user@domainand press Enter. Then, type your message, and when done with that press Ctrl + D to send an e-mail. - To read your e-mails, log in with the user you send e-mails to. Start the mail program with the command
mail. This should show you a list of e-mails received by this user account. The output should look similar to following screenshot:
- To read any e-mail, type in the mail number and press Enter. Type
qfollowed by Enter to quit the mail reader.
How it works…
Postfix installation is quite a simple task; you need to be sure that you have configured the proper settings and then you are up and running in minutes. The Postfix installation process itself prompts for basic settings.
Tip
If you miss providing configuration during installation, you can always recall the same dialogue box with the reconfigure command as follows:
$ sudo dpkg-reconfigure postfix
Other parameters include mynetworks and mydestination. With mynetwork, we have restricted the uses of the mail server to the local network. Only users on the local network can use this server to send and receive e-mails. The parameter mydestination specifies the domain names that Postfix is going to serve. For all other domains that are not listed under mydestination, Postfix will simply act as a forwarder.
We have configured Postfix to use the Maildir format for storing e-mails. This is a new storage format and provides various improvements over the default format, mbox. Also, Maildir is used by various IMAP and POP servers. With Maildir, each new message is stored in a separate file. This avoids file locking when working with messages and provides protection against mailbox corruption.
Now if you send an e-mail to a local domain, it will be delivered to the inbox of the respective user, which can be read with mail command. If you send e-mails to an external mail server, such as Gmail, chances are your mail gets delivered to spam. You need to include a number of different parameters in your e-mail headers and then make sure that your server IP is not blacklisted. It would be a good idea to use an external mail server such as Mail Chimp or Gmail for sending e-mails.
See also
- An article by Jeff Atwood on sending e-mails through code. This may help you get your e-mails out of spam: http://blog.codinghorror.com/so-youd-like-to-send-some-email-through-code/
- Mailbox formats: http://wiki.dovecot.org/MailboxFormat
- The difference between port 465 and 587: http://stackoverflow.com/questions/15796530/what-is-the-difference-between-ports-465-and-587
Getting ready
You will need access to a root account or an account with sudo privileges.
A domain name (FQDN) is required while configuring Postfix. You can configure your local server for testing, but make sure that you set the proper host entries and hostname.
How to do it…
Follow these steps to send e-mails with Postfix:
- Install Postfix and
mailutilswith the following commands:$ sudo apt-get update $ sudo apt-get install postfix mailutils -y
- The installation process will prompt you to enter some basic configuration details. When asked for General type of mail configuration:, select Internet Site and then click on <Ok>:

- On the next screen, enter your domain name, for example,
mail.example.com, and answer the other questions. You can leave them with default values:
- After installation completes, we need to modify the Postfix configuration under
/etc/postfix/main.cf:$ sudo nano /etc/postfix/main.cf - Set
myhostnameto point to your domain name:myhostname = mail.example.com - Ensure
mynetworksis set to the local network. This will secure your server from spammers:mynetworks = 127.0.0.0/8 [::ffff:127.0.0.0]/104 [::1]/128
- Also check
mydestination. It should contain your domain name:mydestination = example.com, ubuntu, localhost.localdoma in, localhost

- Change the mail storage format to
Maildirfrom the defaultmbox. Search and uncomment the following line:home_mailbox = Maildir/ - Optionally, you can change the TLS keys used by Postfix. Find the
TLS parameterssection and point the variables to your key path:
- Save the configuration file and exit.
- Now, reload Postfix for the changes to take effect:
$ sudo service postfix reloadTest if everything is working as expected. Open a telnet connection to the mail server:
$ telnet localhost 25You should see an output similar to the following screenshot:

- Now, send your first e-mail from this server. Type
sendmail user@domainand press Enter. Then, type your message, and when done with that press Ctrl + D to send an e-mail. - To read your e-mails, log in with the user you send e-mails to. Start the mail program with the command
mail. This should show you a list of e-mails received by this user account. The output should look similar to following screenshot:
- To read any e-mail, type in the mail number and press Enter. Type
qfollowed by Enter to quit the mail reader.
How it works…
Postfix installation is quite a simple task; you need to be sure that you have configured the proper settings and then you are up and running in minutes. The Postfix installation process itself prompts for basic settings.
Tip
If you miss providing configuration during installation, you can always recall the same dialogue box with the reconfigure command as follows:
$ sudo dpkg-reconfigure postfix
Other parameters include mynetworks and mydestination. With mynetwork, we have restricted the uses of the mail server to the local network. Only users on the local network can use this server to send and receive e-mails. The parameter mydestination specifies the domain names that Postfix is going to serve. For all other domains that are not listed under mydestination, Postfix will simply act as a forwarder.
We have configured Postfix to use the Maildir format for storing e-mails. This is a new storage format and provides various improvements over the default format, mbox. Also, Maildir is used by various IMAP and POP servers. With Maildir, each new message is stored in a separate file. This avoids file locking when working with messages and provides protection against mailbox corruption.
Now if you send an e-mail to a local domain, it will be delivered to the inbox of the respective user, which can be read with mail command. If you send e-mails to an external mail server, such as Gmail, chances are your mail gets delivered to spam. You need to include a number of different parameters in your e-mail headers and then make sure that your server IP is not blacklisted. It would be a good idea to use an external mail server such as Mail Chimp or Gmail for sending e-mails.
See also
- An article by Jeff Atwood on sending e-mails through code. This may help you get your e-mails out of spam: http://blog.codinghorror.com/so-youd-like-to-send-some-email-through-code/
- Mailbox formats: http://wiki.dovecot.org/MailboxFormat
- The difference between port 465 and 587: http://stackoverflow.com/questions/15796530/what-is-the-difference-between-ports-465-and-587
How to do it…
Follow these steps to send e-mails with Postfix:
- Install Postfix and
mailutilswith the following commands:$ sudo apt-get update $ sudo apt-get install postfix mailutils -y
- The installation process will prompt you to enter some basic configuration details. When asked for General type of mail configuration:, select Internet Site and then click on <Ok>:

- On the next screen, enter your domain name, for example,
mail.example.com, and answer the other questions. You can leave them with default values:
- After installation completes, we need to modify the Postfix configuration under
/etc/postfix/main.cf:$ sudo nano /etc/postfix/main.cf - Set
myhostnameto point to your domain name:myhostname = mail.example.com - Ensure
mynetworksis set to the local network. This will secure your server from spammers:mynetworks = 127.0.0.0/8 [::ffff:127.0.0.0]/104 [::1]/128
- Also check
mydestination. It should contain your domain name:mydestination = example.com, ubuntu, localhost.localdoma in, localhost

- Change the mail storage format to
Maildirfrom the defaultmbox. Search and uncomment the following line:home_mailbox = Maildir/ - Optionally, you can change the TLS keys used by Postfix. Find the
TLS parameterssection and point the variables to your key path:
- Save the configuration file and exit.
- Now, reload Postfix for the changes to take effect:
$ sudo service postfix reloadTest if everything is working as expected. Open a telnet connection to the mail server:
$ telnet localhost 25You should see an output similar to the following screenshot:

- Now, send your first e-mail from this server. Type
sendmail user@domainand press Enter. Then, type your message, and when done with that press Ctrl + D to send an e-mail. - To read your e-mails, log in with the user you send e-mails to. Start the mail program with the command
mail. This should show you a list of e-mails received by this user account. The output should look similar to following screenshot:
- To read any e-mail, type in the mail number and press Enter. Type
qfollowed by Enter to quit the mail reader.
How it works…
Postfix installation is quite a simple task; you need to be sure that you have configured the proper settings and then you are up and running in minutes. The Postfix installation process itself prompts for basic settings.
Tip
If you miss providing configuration during installation, you can always recall the same dialogue box with the reconfigure command as follows:
$ sudo dpkg-reconfigure postfix
Other parameters include mynetworks and mydestination. With mynetwork, we have restricted the uses of the mail server to the local network. Only users on the local network can use this server to send and receive e-mails. The parameter mydestination specifies the domain names that Postfix is going to serve. For all other domains that are not listed under mydestination, Postfix will simply act as a forwarder.
We have configured Postfix to use the Maildir format for storing e-mails. This is a new storage format and provides various improvements over the default format, mbox. Also, Maildir is used by various IMAP and POP servers. With Maildir, each new message is stored in a separate file. This avoids file locking when working with messages and provides protection against mailbox corruption.
Now if you send an e-mail to a local domain, it will be delivered to the inbox of the respective user, which can be read with mail command. If you send e-mails to an external mail server, such as Gmail, chances are your mail gets delivered to spam. You need to include a number of different parameters in your e-mail headers and then make sure that your server IP is not blacklisted. It would be a good idea to use an external mail server such as Mail Chimp or Gmail for sending e-mails.
See also
- An article by Jeff Atwood on sending e-mails through code. This may help you get your e-mails out of spam: http://blog.codinghorror.com/so-youd-like-to-send-some-email-through-code/
- Mailbox formats: http://wiki.dovecot.org/MailboxFormat
- The difference between port 465 and 587: http://stackoverflow.com/questions/15796530/what-is-the-difference-between-ports-465-and-587
How it works…
Postfix installation is quite a simple task; you need to be sure that you have configured the proper settings and then you are up and running in minutes. The Postfix installation process itself prompts for basic settings.
Tip
If you miss providing configuration during installation, you can always recall the same dialogue box with the reconfigure command as follows:
$ sudo dpkg-reconfigure postfix
Other parameters include mynetworks and mydestination. With mynetwork, we have restricted the uses of the mail server to the local network. Only users on the local network can use this server to send and receive e-mails. The parameter mydestination specifies the domain names that Postfix is going to serve. For all other domains that are not listed under mydestination, Postfix will simply act as a forwarder.
We have configured Postfix to use the Maildir format for storing e-mails. This is a new storage format and provides various improvements over the default format, mbox. Also, Maildir is used by various IMAP and POP servers. With Maildir, each new message is stored in a separate file. This avoids file locking when working with messages and provides protection against mailbox corruption.
Now if you send an e-mail to a local domain, it will be delivered to the inbox of the respective user, which can be read with mail command. If you send e-mails to an external mail server, such as Gmail, chances are your mail gets delivered to spam. You need to include a number of different parameters in your e-mail headers and then make sure that your server IP is not blacklisted. It would be a good idea to use an external mail server such as Mail Chimp or Gmail for sending e-mails.
See also
- An article by Jeff Atwood on sending e-mails through code. This may help you get your e-mails out of spam: http://blog.codinghorror.com/so-youd-like-to-send-some-email-through-code/
- Mailbox formats: http://wiki.dovecot.org/MailboxFormat
- The difference between port 465 and 587: http://stackoverflow.com/questions/15796530/what-is-the-difference-between-ports-465-and-587
See also
- An article by Jeff Atwood on sending e-mails through code. This may help you get your e-mails out of spam: http://blog.codinghorror.com/so-youd-like-to-send-some-email-through-code/
- Mailbox formats: http://wiki.dovecot.org/MailboxFormat
- The difference between port 465 and 587: http://stackoverflow.com/questions/15796530/what-is-the-difference-between-ports-465-and-587
Enabling IMAP and POP3 with Dovecot
In this recipe, we will learn how to install and set up Dovecot to enable accessing e-mails over IMAP and POP3 protocols. This will enable mail clients such as thunderbird to download e-mails on a user's local system.
Getting ready
You will need access to a root account or an account with sudo privileges
Make sure that you have set up Postfix and are able to send and receive e-mails on your server.
You may need an e-mail client to connect to and test the Dovecot setup.
How to do it…
Follow these steps to enable IMAP and POP3 with Dovecot:
- First, install the Dovecot binaries from the Ubuntu main repository:
$ sudo apt-get update $ sudo apt-get install dovecot-imapd dovecot-pop3d
- You will be prompted for a hostname to be used for certificate generation. Type in a full hostname, for example
mail.example.com. You can skip this step if you already have certificates. - Next, proceed with configuring Dovecot. Open the file
/etc/dovecot/dovecot.conf:$ sudo nano /etc/dovecot/dovecot.conf - Find the
Enable installed protocolssection and add a new line to set the protocols that you want Dovecot to support:protocols = pop3 pop3s imap imaps
- Open
/etc/dovecot/conf.d/10-mail.confand set the mailbox to be used. Dovecot supportsmboxas well asMaildir. Make sure you set the correct path of yourmaildirectory:mail_location = mbox:~/mail:INBOX=/var/spool/mail/%u
- Open
/etc/dovecot/conf.d/10-ssl.confand uncomment or change the following lines to enable SSL authentication. Here, I have used certificates created by Postfix. You can use your own certificates or use the one generated by Dovecot:ssl = yes ssl_cert = < /etc/ssl/certs/ssl-cert-snakeoil.pem ssl_key =</etc/ssl/private/ssl-cert-snakeoil.key
- Restart the Dovecot daemon:
$ sudo service dovecot restart - Test Dovecot by creating a telnet connection. You should see an output similar to the following:
$ telnet localhost pop3
How it works…
Dovecot is one of the most popular Mail Delivery Agents (MDA) with support for IMAP and POP3 protocols. It works with both major mailbox formats, namely mbox and Maildir. The installation process is simple, and a minimal configuration can get you started with your own IMAP or POP3 service.
Dovecot developers have tried to simplify the configuration by separating it across various small files for each section. All these configuration files are located under /etc/dovecot/conf.d. If you prefer to use a single configuration file, you can replace the default file with the entire working configuration. To get all enabled configurations, use the doveconf -n command:
# mv /etc/dovecot/dovecot.conf /etc/dovecot/dovecot.conf.old # doveconf -n > /etc/dovecot/dovecot.conf
In this recipe, we have configured Dovecot to support POP3, POP3 secure, IMAP, and IMAP secure. You can choose a single protocol or any combination of them. After setting protocol support, we have set the mailbox type to mbox. If you are using Maildir as your mailbox format, instead replace the mailbox setting with following line:
mail_location = maildir:~/Maildir
Now, when a user wants to check his e-mails, they need to authenticate with the Dovecot server. At this stage, only users with a user account on the server will be able to access their e-mails with Dovecot. To support users without creating a user account, we will need to set up Virtual Users, which is covered in the next recipes.
If you plan to skip SSL setup, you may need to enable plain text authentication under the configuration file, /etc/dovecot/conf.d/10-auth.conf. Find and uncomment the following line and set it to no:
disable_plaintext_auth = yes
The default setting is to allow plain text authentication over SSL connections only. That means the clients that do not support SSL will not be allowed to log in.
See also
- Dovecot wiki Quick-configuration at http://wiki2.dovecot.org/QuickConfiguration
Getting ready
You will need access to a root account or an account with sudo privileges
Make sure that you have set up Postfix and are able to send and receive e-mails on your server.
You may need an e-mail client to connect to and test the Dovecot setup.
How to do it…
Follow these steps to enable IMAP and POP3 with Dovecot:
- First, install the Dovecot binaries from the Ubuntu main repository:
$ sudo apt-get update $ sudo apt-get install dovecot-imapd dovecot-pop3d
- You will be prompted for a hostname to be used for certificate generation. Type in a full hostname, for example
mail.example.com. You can skip this step if you already have certificates. - Next, proceed with configuring Dovecot. Open the file
/etc/dovecot/dovecot.conf:$ sudo nano /etc/dovecot/dovecot.conf - Find the
Enable installed protocolssection and add a new line to set the protocols that you want Dovecot to support:protocols = pop3 pop3s imap imaps
- Open
/etc/dovecot/conf.d/10-mail.confand set the mailbox to be used. Dovecot supportsmboxas well asMaildir. Make sure you set the correct path of yourmaildirectory:mail_location = mbox:~/mail:INBOX=/var/spool/mail/%u
- Open
/etc/dovecot/conf.d/10-ssl.confand uncomment or change the following lines to enable SSL authentication. Here, I have used certificates created by Postfix. You can use your own certificates or use the one generated by Dovecot:ssl = yes ssl_cert = < /etc/ssl/certs/ssl-cert-snakeoil.pem ssl_key =</etc/ssl/private/ssl-cert-snakeoil.key
- Restart the Dovecot daemon:
$ sudo service dovecot restart - Test Dovecot by creating a telnet connection. You should see an output similar to the following:
$ telnet localhost pop3
How it works…
Dovecot is one of the most popular Mail Delivery Agents (MDA) with support for IMAP and POP3 protocols. It works with both major mailbox formats, namely mbox and Maildir. The installation process is simple, and a minimal configuration can get you started with your own IMAP or POP3 service.
Dovecot developers have tried to simplify the configuration by separating it across various small files for each section. All these configuration files are located under /etc/dovecot/conf.d. If you prefer to use a single configuration file, you can replace the default file with the entire working configuration. To get all enabled configurations, use the doveconf -n command:
# mv /etc/dovecot/dovecot.conf /etc/dovecot/dovecot.conf.old # doveconf -n > /etc/dovecot/dovecot.conf
In this recipe, we have configured Dovecot to support POP3, POP3 secure, IMAP, and IMAP secure. You can choose a single protocol or any combination of them. After setting protocol support, we have set the mailbox type to mbox. If you are using Maildir as your mailbox format, instead replace the mailbox setting with following line:
mail_location = maildir:~/Maildir
Now, when a user wants to check his e-mails, they need to authenticate with the Dovecot server. At this stage, only users with a user account on the server will be able to access their e-mails with Dovecot. To support users without creating a user account, we will need to set up Virtual Users, which is covered in the next recipes.
If you plan to skip SSL setup, you may need to enable plain text authentication under the configuration file, /etc/dovecot/conf.d/10-auth.conf. Find and uncomment the following line and set it to no:
disable_plaintext_auth = yes
The default setting is to allow plain text authentication over SSL connections only. That means the clients that do not support SSL will not be allowed to log in.
See also
- Dovecot wiki Quick-configuration at http://wiki2.dovecot.org/QuickConfiguration
How to do it…
Follow these steps to enable IMAP and POP3 with Dovecot:
- First, install the Dovecot binaries from the Ubuntu main repository:
$ sudo apt-get update $ sudo apt-get install dovecot-imapd dovecot-pop3d
- You will be prompted for a hostname to be used for certificate generation. Type in a full hostname, for example
mail.example.com. You can skip this step if you already have certificates. - Next, proceed with configuring Dovecot. Open the file
/etc/dovecot/dovecot.conf:$ sudo nano /etc/dovecot/dovecot.conf - Find the
Enable installed protocolssection and add a new line to set the protocols that you want Dovecot to support:protocols = pop3 pop3s imap imaps
- Open
/etc/dovecot/conf.d/10-mail.confand set the mailbox to be used. Dovecot supportsmboxas well asMaildir. Make sure you set the correct path of yourmaildirectory:mail_location = mbox:~/mail:INBOX=/var/spool/mail/%u
- Open
/etc/dovecot/conf.d/10-ssl.confand uncomment or change the following lines to enable SSL authentication. Here, I have used certificates created by Postfix. You can use your own certificates or use the one generated by Dovecot:ssl = yes ssl_cert = < /etc/ssl/certs/ssl-cert-snakeoil.pem ssl_key =</etc/ssl/private/ssl-cert-snakeoil.key
- Restart the Dovecot daemon:
$ sudo service dovecot restart - Test Dovecot by creating a telnet connection. You should see an output similar to the following:
$ telnet localhost pop3
How it works…
Dovecot is one of the most popular Mail Delivery Agents (MDA) with support for IMAP and POP3 protocols. It works with both major mailbox formats, namely mbox and Maildir. The installation process is simple, and a minimal configuration can get you started with your own IMAP or POP3 service.
Dovecot developers have tried to simplify the configuration by separating it across various small files for each section. All these configuration files are located under /etc/dovecot/conf.d. If you prefer to use a single configuration file, you can replace the default file with the entire working configuration. To get all enabled configurations, use the doveconf -n command:
# mv /etc/dovecot/dovecot.conf /etc/dovecot/dovecot.conf.old # doveconf -n > /etc/dovecot/dovecot.conf
In this recipe, we have configured Dovecot to support POP3, POP3 secure, IMAP, and IMAP secure. You can choose a single protocol or any combination of them. After setting protocol support, we have set the mailbox type to mbox. If you are using Maildir as your mailbox format, instead replace the mailbox setting with following line:
mail_location = maildir:~/Maildir
Now, when a user wants to check his e-mails, they need to authenticate with the Dovecot server. At this stage, only users with a user account on the server will be able to access their e-mails with Dovecot. To support users without creating a user account, we will need to set up Virtual Users, which is covered in the next recipes.
If you plan to skip SSL setup, you may need to enable plain text authentication under the configuration file, /etc/dovecot/conf.d/10-auth.conf. Find and uncomment the following line and set it to no:
disable_plaintext_auth = yes
The default setting is to allow plain text authentication over SSL connections only. That means the clients that do not support SSL will not be allowed to log in.
See also
- Dovecot wiki Quick-configuration at http://wiki2.dovecot.org/QuickConfiguration
How it works…
Dovecot is one of the most popular Mail Delivery Agents (MDA) with support for IMAP and POP3 protocols. It works with both major mailbox formats, namely mbox and Maildir. The installation process is simple, and a minimal configuration can get you started with your own IMAP or POP3 service.
Dovecot developers have tried to simplify the configuration by separating it across various small files for each section. All these configuration files are located under /etc/dovecot/conf.d. If you prefer to use a single configuration file, you can replace the default file with the entire working configuration. To get all enabled configurations, use the doveconf -n command:
# mv /etc/dovecot/dovecot.conf /etc/dovecot/dovecot.conf.old # doveconf -n > /etc/dovecot/dovecot.conf
In this recipe, we have configured Dovecot to support POP3, POP3 secure, IMAP, and IMAP secure. You can choose a single protocol or any combination of them. After setting protocol support, we have set the mailbox type to mbox. If you are using Maildir as your mailbox format, instead replace the mailbox setting with following line:
mail_location = maildir:~/Maildir
Now, when a user wants to check his e-mails, they need to authenticate with the Dovecot server. At this stage, only users with a user account on the server will be able to access their e-mails with Dovecot. To support users without creating a user account, we will need to set up Virtual Users, which is covered in the next recipes.
If you plan to skip SSL setup, you may need to enable plain text authentication under the configuration file, /etc/dovecot/conf.d/10-auth.conf. Find and uncomment the following line and set it to no:
disable_plaintext_auth = yes
The default setting is to allow plain text authentication over SSL connections only. That means the clients that do not support SSL will not be allowed to log in.
See also
- Dovecot wiki Quick-configuration at http://wiki2.dovecot.org/QuickConfiguration
See also
- Dovecot wiki Quick-configuration at http://wiki2.dovecot.org/QuickConfiguration
Adding e-mail accounts
In this recipe, we will learn how to add e-mail accounts to Postfix. The easiest way to add a new e-mail account to Postfix is to add a new user account on your server. Postfix will check for user accounts and deliver e-mails to respective users. We will create a virtual user setup so that we do not need to create user accounts for each e-mail user.
Getting ready
You will need access to a root account or an account with sudo privileges.
I assume that you have completed your basic Postfix setup and that it is working properly.
How to do it…
Follow these steps to add e-mail account:
- Create a new user account:
$ useradd -s /usr/bin/nologin -m vmail - Get the UID and GID for this account:
$ grep vmail /etc/passwd vmail:x:1001:1001::/home/vmail:/usr/bin/nologin

- Create a base directory layout for domains and users:
$ sudo mkdir -p /home/vmail/example.org/bob $ sudo mkdir -p /home/vmail/example.net/alice
- Allow only the user vmail to access these files:
$ sudo chown -R vmail:vmail /home/vmail $ chmod -R 700 /home/vmail
- Next, configure Postfix. Edit
/etc/postfix/main.cfand add the following lines:virtual_mailbox_base = /home/vmail virtual_mailbox_domains = /etc/postfix/virtual_domains virtual_mailbox_maps = hash:/etc/postfix/virtual_maps virtual_alias_maps = hash:/etc/postfix/virtual_alias virtual_uid_maps = static:1001 # user ID for user vmail virtual_gid_maps = static:1001 # group ID for user vmail
- Create the file
virtual_domainsunder/etc/postfix:$ sudo nano /etc/postfix/virtual_domainsexample.org example.net
- Create the
virtual_mapsfile:$ sudo nano /etc/postfix/virtual_maps bob@example.org example.org/bob/ alice@example.org example.org/alice/ @example.org example.org/catchall/ # catch all address
- Create the
virtual_aliasfile and optionally set aredirect:$ sudo nano /etc/postfix/virtual_alias # redirect emails for tim to bob tim@example.org bob@example.org
- Now generate database of virtual maps and aliases by hashing respective files:
$ sudo postmap /etc/postfix/virtual_maps $ sudo postmap /etc/postfix/virtual_alias
- Reload Postfix and send an e-mail to the newly created address:
$ sudo postfix reload $ sendmail bob@example.org
How it works…
Here, we have created a virtual mailbox setup to enable our Postfix server to serve multiple domains as well as add e-mail users without creating user accounts on the server. All e-mails received by virtual users will be stored under the home directory of the vmail user (virtual_mailbox_base in Postfix configuration). When you need to add a new e-mail account, simply add the e-mail address with its respective domain to the virtual_maps file. In case you need to support a new domain, you can easily add it to the virtual_domains file.
The third file we used is virtual_alias. You can set e-mail forwarding in this file. It is handy when you need to create a new alias for an e-mail address or forward e-mails to one or multiple accounts. We have set a catchall entry in the virtual_alias file; this setting will redirect all e-mails received on nonexistent accounts to catchall@example.org, which can be checked by the domain administrator.
There's more…
Using files for virtual users and domains is good for getting started with setup. But once you need to add more and more user accounts and domains it is a good idea to move the users and domains to a database server. This can be easily done by changing the lookup table type. Postfix supports a variety of lookup table types, which include LDAP, MySQL, PGSQL, memcache, SQLite, and many others.
To use MySQL as a backend database, complete the following steps:
- Create respective tables for
virtual_domain,virtual_maps, andvirtual_alias. - Change the Postfix configuration to use MySQL as a lookup table:
virtual_mailbox_domains = mysql:/etc/postfix/mysql-virtual-domains virtual_mailbox_maps = mysql:/etc/postfix/mysql-virtual-maps virtual_alias_maps = mysql:/etc/postfix/mysql-virtual-alias
- Add the respective details to each file using the following commands:
$ sudo nano /etc/postfix/mysql-virtual-domainsuser = mysql_user password = mysql_password hosts = 127.0.0.1 dbname = mysql_db_name query = SELECT 1 FROM virtual_domains WHERE name='%s' $ sudo nano /etc/postfix/mysql-virtual-maps... query = SELECT 1 FROM virtual_users WHERE email='%s' $ sudo nano /etc/postfix/mysql-virtual-alias... query = SELECT destination FROM virtual_aliases WHERE source='%s'
- You can test your mapping with the following command. This should output
1as a result:$ postmap -q bob@example.org mysql:/etc/postfix/mysql-virtual-maps - Finally, restart the Postfix daemon.
Web console for virtual mailbox administration
The Vimbadmin package provides a web console for virtual mailbox administration. It is a PHP-based open source package. You can get source code and installation instructions at https://github.com/opensolutions/ViMbAdmin.
See also
- Postfix guide at http://www.postfix.org/VIRTUAL_README.html
- Postfix lookup table types at http://www.postfix.org/DATABASE_README.html#types
Getting ready
You will need access to a root account or an account with sudo privileges.
I assume that you have completed your basic Postfix setup and that it is working properly.
How to do it…
Follow these steps to add e-mail account:
- Create a new user account:
$ useradd -s /usr/bin/nologin -m vmail - Get the UID and GID for this account:
$ grep vmail /etc/passwd vmail:x:1001:1001::/home/vmail:/usr/bin/nologin

- Create a base directory layout for domains and users:
$ sudo mkdir -p /home/vmail/example.org/bob $ sudo mkdir -p /home/vmail/example.net/alice
- Allow only the user vmail to access these files:
$ sudo chown -R vmail:vmail /home/vmail $ chmod -R 700 /home/vmail
- Next, configure Postfix. Edit
/etc/postfix/main.cfand add the following lines:virtual_mailbox_base = /home/vmail virtual_mailbox_domains = /etc/postfix/virtual_domains virtual_mailbox_maps = hash:/etc/postfix/virtual_maps virtual_alias_maps = hash:/etc/postfix/virtual_alias virtual_uid_maps = static:1001 # user ID for user vmail virtual_gid_maps = static:1001 # group ID for user vmail
- Create the file
virtual_domainsunder/etc/postfix:$ sudo nano /etc/postfix/virtual_domainsexample.org example.net
- Create the
virtual_mapsfile:$ sudo nano /etc/postfix/virtual_maps bob@example.org example.org/bob/ alice@example.org example.org/alice/ @example.org example.org/catchall/ # catch all address
- Create the
virtual_aliasfile and optionally set aredirect:$ sudo nano /etc/postfix/virtual_alias # redirect emails for tim to bob tim@example.org bob@example.org
- Now generate database of virtual maps and aliases by hashing respective files:
$ sudo postmap /etc/postfix/virtual_maps $ sudo postmap /etc/postfix/virtual_alias
- Reload Postfix and send an e-mail to the newly created address:
$ sudo postfix reload $ sendmail bob@example.org
How it works…
Here, we have created a virtual mailbox setup to enable our Postfix server to serve multiple domains as well as add e-mail users without creating user accounts on the server. All e-mails received by virtual users will be stored under the home directory of the vmail user (virtual_mailbox_base in Postfix configuration). When you need to add a new e-mail account, simply add the e-mail address with its respective domain to the virtual_maps file. In case you need to support a new domain, you can easily add it to the virtual_domains file.
The third file we used is virtual_alias. You can set e-mail forwarding in this file. It is handy when you need to create a new alias for an e-mail address or forward e-mails to one or multiple accounts. We have set a catchall entry in the virtual_alias file; this setting will redirect all e-mails received on nonexistent accounts to catchall@example.org, which can be checked by the domain administrator.
There's more…
Using files for virtual users and domains is good for getting started with setup. But once you need to add more and more user accounts and domains it is a good idea to move the users and domains to a database server. This can be easily done by changing the lookup table type. Postfix supports a variety of lookup table types, which include LDAP, MySQL, PGSQL, memcache, SQLite, and many others.
To use MySQL as a backend database, complete the following steps:
- Create respective tables for
virtual_domain,virtual_maps, andvirtual_alias. - Change the Postfix configuration to use MySQL as a lookup table:
virtual_mailbox_domains = mysql:/etc/postfix/mysql-virtual-domains virtual_mailbox_maps = mysql:/etc/postfix/mysql-virtual-maps virtual_alias_maps = mysql:/etc/postfix/mysql-virtual-alias
- Add the respective details to each file using the following commands:
$ sudo nano /etc/postfix/mysql-virtual-domainsuser = mysql_user password = mysql_password hosts = 127.0.0.1 dbname = mysql_db_name query = SELECT 1 FROM virtual_domains WHERE name='%s' $ sudo nano /etc/postfix/mysql-virtual-maps... query = SELECT 1 FROM virtual_users WHERE email='%s' $ sudo nano /etc/postfix/mysql-virtual-alias... query = SELECT destination FROM virtual_aliases WHERE source='%s'
- You can test your mapping with the following command. This should output
1as a result:$ postmap -q bob@example.org mysql:/etc/postfix/mysql-virtual-maps - Finally, restart the Postfix daemon.
Web console for virtual mailbox administration
The Vimbadmin package provides a web console for virtual mailbox administration. It is a PHP-based open source package. You can get source code and installation instructions at https://github.com/opensolutions/ViMbAdmin.
See also
- Postfix guide at http://www.postfix.org/VIRTUAL_README.html
- Postfix lookup table types at http://www.postfix.org/DATABASE_README.html#types
How to do it…
Follow these steps to add e-mail account:
- Create a new user account:
$ useradd -s /usr/bin/nologin -m vmail - Get the UID and GID for this account:
$ grep vmail /etc/passwd vmail:x:1001:1001::/home/vmail:/usr/bin/nologin

- Create a base directory layout for domains and users:
$ sudo mkdir -p /home/vmail/example.org/bob $ sudo mkdir -p /home/vmail/example.net/alice
- Allow only the user vmail to access these files:
$ sudo chown -R vmail:vmail /home/vmail $ chmod -R 700 /home/vmail
- Next, configure Postfix. Edit
/etc/postfix/main.cfand add the following lines:virtual_mailbox_base = /home/vmail virtual_mailbox_domains = /etc/postfix/virtual_domains virtual_mailbox_maps = hash:/etc/postfix/virtual_maps virtual_alias_maps = hash:/etc/postfix/virtual_alias virtual_uid_maps = static:1001 # user ID for user vmail virtual_gid_maps = static:1001 # group ID for user vmail
- Create the file
virtual_domainsunder/etc/postfix:$ sudo nano /etc/postfix/virtual_domainsexample.org example.net
- Create the
virtual_mapsfile:$ sudo nano /etc/postfix/virtual_maps bob@example.org example.org/bob/ alice@example.org example.org/alice/ @example.org example.org/catchall/ # catch all address
- Create the
virtual_aliasfile and optionally set aredirect:$ sudo nano /etc/postfix/virtual_alias # redirect emails for tim to bob tim@example.org bob@example.org
- Now generate database of virtual maps and aliases by hashing respective files:
$ sudo postmap /etc/postfix/virtual_maps $ sudo postmap /etc/postfix/virtual_alias
- Reload Postfix and send an e-mail to the newly created address:
$ sudo postfix reload $ sendmail bob@example.org
How it works…
Here, we have created a virtual mailbox setup to enable our Postfix server to serve multiple domains as well as add e-mail users without creating user accounts on the server. All e-mails received by virtual users will be stored under the home directory of the vmail user (virtual_mailbox_base in Postfix configuration). When you need to add a new e-mail account, simply add the e-mail address with its respective domain to the virtual_maps file. In case you need to support a new domain, you can easily add it to the virtual_domains file.
The third file we used is virtual_alias. You can set e-mail forwarding in this file. It is handy when you need to create a new alias for an e-mail address or forward e-mails to one or multiple accounts. We have set a catchall entry in the virtual_alias file; this setting will redirect all e-mails received on nonexistent accounts to catchall@example.org, which can be checked by the domain administrator.
There's more…
Using files for virtual users and domains is good for getting started with setup. But once you need to add more and more user accounts and domains it is a good idea to move the users and domains to a database server. This can be easily done by changing the lookup table type. Postfix supports a variety of lookup table types, which include LDAP, MySQL, PGSQL, memcache, SQLite, and many others.
To use MySQL as a backend database, complete the following steps:
- Create respective tables for
virtual_domain,virtual_maps, andvirtual_alias. - Change the Postfix configuration to use MySQL as a lookup table:
virtual_mailbox_domains = mysql:/etc/postfix/mysql-virtual-domains virtual_mailbox_maps = mysql:/etc/postfix/mysql-virtual-maps virtual_alias_maps = mysql:/etc/postfix/mysql-virtual-alias
- Add the respective details to each file using the following commands:
$ sudo nano /etc/postfix/mysql-virtual-domainsuser = mysql_user password = mysql_password hosts = 127.0.0.1 dbname = mysql_db_name query = SELECT 1 FROM virtual_domains WHERE name='%s' $ sudo nano /etc/postfix/mysql-virtual-maps... query = SELECT 1 FROM virtual_users WHERE email='%s' $ sudo nano /etc/postfix/mysql-virtual-alias... query = SELECT destination FROM virtual_aliases WHERE source='%s'
- You can test your mapping with the following command. This should output
1as a result:$ postmap -q bob@example.org mysql:/etc/postfix/mysql-virtual-maps - Finally, restart the Postfix daemon.
Web console for virtual mailbox administration
The Vimbadmin package provides a web console for virtual mailbox administration. It is a PHP-based open source package. You can get source code and installation instructions at https://github.com/opensolutions/ViMbAdmin.
See also
- Postfix guide at http://www.postfix.org/VIRTUAL_README.html
- Postfix lookup table types at http://www.postfix.org/DATABASE_README.html#types
How it works…
Here, we have created a virtual mailbox setup to enable our Postfix server to serve multiple domains as well as add e-mail users without creating user accounts on the server. All e-mails received by virtual users will be stored under the home directory of the vmail user (virtual_mailbox_base in Postfix configuration). When you need to add a new e-mail account, simply add the e-mail address with its respective domain to the virtual_maps file. In case you need to support a new domain, you can easily add it to the virtual_domains file.
The third file we used is virtual_alias. You can set e-mail forwarding in this file. It is handy when you need to create a new alias for an e-mail address or forward e-mails to one or multiple accounts. We have set a catchall entry in the virtual_alias file; this setting will redirect all e-mails received on nonexistent accounts to catchall@example.org, which can be checked by the domain administrator.
There's more…
Using files for virtual users and domains is good for getting started with setup. But once you need to add more and more user accounts and domains it is a good idea to move the users and domains to a database server. This can be easily done by changing the lookup table type. Postfix supports a variety of lookup table types, which include LDAP, MySQL, PGSQL, memcache, SQLite, and many others.
To use MySQL as a backend database, complete the following steps:
- Create respective tables for
virtual_domain,virtual_maps, andvirtual_alias. - Change the Postfix configuration to use MySQL as a lookup table:
virtual_mailbox_domains = mysql:/etc/postfix/mysql-virtual-domains virtual_mailbox_maps = mysql:/etc/postfix/mysql-virtual-maps virtual_alias_maps = mysql:/etc/postfix/mysql-virtual-alias
- Add the respective details to each file using the following commands:
$ sudo nano /etc/postfix/mysql-virtual-domainsuser = mysql_user password = mysql_password hosts = 127.0.0.1 dbname = mysql_db_name query = SELECT 1 FROM virtual_domains WHERE name='%s' $ sudo nano /etc/postfix/mysql-virtual-maps... query = SELECT 1 FROM virtual_users WHERE email='%s' $ sudo nano /etc/postfix/mysql-virtual-alias... query = SELECT destination FROM virtual_aliases WHERE source='%s'
- You can test your mapping with the following command. This should output
1as a result:$ postmap -q bob@example.org mysql:/etc/postfix/mysql-virtual-maps - Finally, restart the Postfix daemon.
Web console for virtual mailbox administration
The Vimbadmin package provides a web console for virtual mailbox administration. It is a PHP-based open source package. You can get source code and installation instructions at https://github.com/opensolutions/ViMbAdmin.
See also
- Postfix guide at http://www.postfix.org/VIRTUAL_README.html
- Postfix lookup table types at http://www.postfix.org/DATABASE_README.html#types
There's more…
Using files for virtual users and domains is good for getting started with setup. But once you need to add more and more user accounts and domains it is a good idea to move the users and domains to a database server. This can be easily done by changing the lookup table type. Postfix supports a variety of lookup table types, which include LDAP, MySQL, PGSQL, memcache, SQLite, and many others.
To use MySQL as a backend database, complete the following steps:
- Create respective tables for
virtual_domain,virtual_maps, andvirtual_alias. - Change the Postfix configuration to use MySQL as a lookup table:
virtual_mailbox_domains = mysql:/etc/postfix/mysql-virtual-domains virtual_mailbox_maps = mysql:/etc/postfix/mysql-virtual-maps virtual_alias_maps = mysql:/etc/postfix/mysql-virtual-alias
- Add the respective details to each file using the following commands:
$ sudo nano /etc/postfix/mysql-virtual-domainsuser = mysql_user password = mysql_password hosts = 127.0.0.1 dbname = mysql_db_name query = SELECT 1 FROM virtual_domains WHERE name='%s' $ sudo nano /etc/postfix/mysql-virtual-maps... query = SELECT 1 FROM virtual_users WHERE email='%s' $ sudo nano /etc/postfix/mysql-virtual-alias... query = SELECT destination FROM virtual_aliases WHERE source='%s'
- You can test your mapping with the following command. This should output
1as a result:$ postmap -q bob@example.org mysql:/etc/postfix/mysql-virtual-maps - Finally, restart the Postfix daemon.
Web console for virtual mailbox administration
The Vimbadmin package provides a web console for virtual mailbox administration. It is a PHP-based open source package. You can get source code and installation instructions at https://github.com/opensolutions/ViMbAdmin.
See also
- Postfix guide at http://www.postfix.org/VIRTUAL_README.html
- Postfix lookup table types at http://www.postfix.org/DATABASE_README.html#types
Web console for virtual mailbox administration
The Vimbadmin package provides a web console for virtual mailbox administration. It is a PHP-based open source package. You can get source code and installation instructions at https://github.com/opensolutions/ViMbAdmin.
- Postfix guide at http://www.postfix.org/VIRTUAL_README.html
- Postfix lookup table types at http://www.postfix.org/DATABASE_README.html#types
See also
- Postfix guide at http://www.postfix.org/VIRTUAL_README.html
- Postfix lookup table types at http://www.postfix.org/DATABASE_README.html#types
Mail filtering with spam-assassin
In this recipe, we will learn how to install and set up a well-known e-mail filtering program, spam-assassin.
Getting ready
You will need access to a root account or an account with sudo privileges.
You need to have Postfix installed and working.
How to do it…
Follow these steps to filter mail with spam-assassin:
- Install spam-assassin with the following command:
$ sudo apt-get update $ sudo apt-get install spamassassin spamc
- Create a user account and group for spam-assassin:
$ sudo groupadd spamd $ sudo useradd -g spamd -s /usr/bin/nologin \ -d /var/log/spamassassin -m spamd
- Change the default settings for the spam daemon. Open
/etc/default/spamassassinand update the following lines:ENABLED=1 SAHOME="/var/log/spamassassin/" OPTIONS="--create-prefs --max-children 5 --username spamd --helper-home-dir ${SAHOME} -s ${SAHOME}spamd.log" PIDFILE="${SAHOME}spamd.pid" CRON=1 - Optionally, configure spam rules by changing values in
/etc/spamassassin/local.cf:trusted_networks 10.0.2. # set your trusted network required_score 3.0 # 3 + will be marked as spam
- Next, we need to change the Postfix settings to pass e-mails through spam-assassin. Open
/etc/postfix/master.cfand find the following line:smtp inet n - - - - smtpd
- Add the content filtering option:
-o content_filter=spamassassin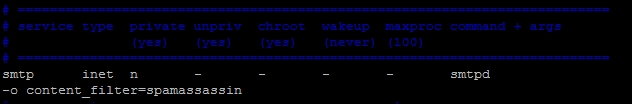
- Define the content filter block by adding the following lines to the end of the file:
spamassassin unix - n n - - pipe user=spamd argv=/usr/bin/spamc -f -e /usr/sbin/sendmail -oi -f ${sender} ${recipient}
- Finally, restart spam-assassin and Postfix:
$ sudo service spamassassin start $ sudo service postfix reload
- You can check spam-assassin and mail logs to verify that spam-assassin is working properly:
$ less /var/log/spamassassin/spamd.log $ less /var/log/mail.log
How it works…
Spam filtering works with the help of a piping mechanism provided by Postfix. We have created a new Unix pipe which will be used to filter e-mails. Postfix will pass all e-mails through this pipe, which will be then scanned through spam-assassin to determine the spam score. If given e-mail scores below the configured threshold, then it passes the filter without any modification; otherwise, spam-assassin adds a spam header to the e-mail.
Spam-assassin works with a Bayesian classifier to classify e-mails as spam or not spam. Basically, it checks the content of the e-mail and determines the score based on content.
There's more…
You can train spam-assassin's Bayesian classifier to get more accurate spam detections.
The following command will train spam-assassin with spam contents (--spam):
$ sudo sa-learn --spam -u spamd --dir ~/Maildir/.Junk/* -D
To train with non-spam content, use the following command (--ham):
$ sudo sa-learn --ham -u spamd --dir ~/Maildir/.INBOX/* -D
If you are using the mbox format, replace --dir ~/Maildir/.Junk/* with the option --mbox.
See also
- Sa-learn - train SpamAssassin's Bayesian classifier at https://spamassassin.apache.org/full/3.2.x/doc/sa-learn.html and https://wiki.apache.org/spamassassin/BayesInSpamAssassin
- Learn about Bayesian classification at https://en.wikipedia.org/wiki/Naive_Bayes_classifier
Getting ready
You will need access to a root account or an account with sudo privileges.
You need to have Postfix installed and working.
How to do it…
Follow these steps to filter mail with spam-assassin:
- Install spam-assassin with the following command:
$ sudo apt-get update $ sudo apt-get install spamassassin spamc
- Create a user account and group for spam-assassin:
$ sudo groupadd spamd $ sudo useradd -g spamd -s /usr/bin/nologin \ -d /var/log/spamassassin -m spamd
- Change the default settings for the spam daemon. Open
/etc/default/spamassassinand update the following lines:ENABLED=1 SAHOME="/var/log/spamassassin/" OPTIONS="--create-prefs --max-children 5 --username spamd --helper-home-dir ${SAHOME} -s ${SAHOME}spamd.log" PIDFILE="${SAHOME}spamd.pid" CRON=1 - Optionally, configure spam rules by changing values in
/etc/spamassassin/local.cf:trusted_networks 10.0.2. # set your trusted network required_score 3.0 # 3 + will be marked as spam
- Next, we need to change the Postfix settings to pass e-mails through spam-assassin. Open
/etc/postfix/master.cfand find the following line:smtp inet n - - - - smtpd
- Add the content filtering option:
-o content_filter=spamassassin
- Define the content filter block by adding the following lines to the end of the file:
spamassassin unix - n n - - pipe user=spamd argv=/usr/bin/spamc -f -e /usr/sbin/sendmail -oi -f ${sender} ${recipient}
- Finally, restart spam-assassin and Postfix:
$ sudo service spamassassin start $ sudo service postfix reload
- You can check spam-assassin and mail logs to verify that spam-assassin is working properly:
$ less /var/log/spamassassin/spamd.log $ less /var/log/mail.log
How it works…
Spam filtering works with the help of a piping mechanism provided by Postfix. We have created a new Unix pipe which will be used to filter e-mails. Postfix will pass all e-mails through this pipe, which will be then scanned through spam-assassin to determine the spam score. If given e-mail scores below the configured threshold, then it passes the filter without any modification; otherwise, spam-assassin adds a spam header to the e-mail.
Spam-assassin works with a Bayesian classifier to classify e-mails as spam or not spam. Basically, it checks the content of the e-mail and determines the score based on content.
There's more…
You can train spam-assassin's Bayesian classifier to get more accurate spam detections.
The following command will train spam-assassin with spam contents (--spam):
$ sudo sa-learn --spam -u spamd --dir ~/Maildir/.Junk/* -D
To train with non-spam content, use the following command (--ham):
$ sudo sa-learn --ham -u spamd --dir ~/Maildir/.INBOX/* -D
If you are using the mbox format, replace --dir ~/Maildir/.Junk/* with the option --mbox.
See also
- Sa-learn - train SpamAssassin's Bayesian classifier at https://spamassassin.apache.org/full/3.2.x/doc/sa-learn.html and https://wiki.apache.org/spamassassin/BayesInSpamAssassin
- Learn about Bayesian classification at https://en.wikipedia.org/wiki/Naive_Bayes_classifier
How to do it…
Follow these steps to filter mail with spam-assassin:
- Install spam-assassin with the following command:
$ sudo apt-get update $ sudo apt-get install spamassassin spamc
- Create a user account and group for spam-assassin:
$ sudo groupadd spamd $ sudo useradd -g spamd -s /usr/bin/nologin \ -d /var/log/spamassassin -m spamd
- Change the default settings for the spam daemon. Open
/etc/default/spamassassinand update the following lines:ENABLED=1 SAHOME="/var/log/spamassassin/" OPTIONS="--create-prefs --max-children 5 --username spamd --helper-home-dir ${SAHOME} -s ${SAHOME}spamd.log" PIDFILE="${SAHOME}spamd.pid" CRON=1 - Optionally, configure spam rules by changing values in
/etc/spamassassin/local.cf:trusted_networks 10.0.2. # set your trusted network required_score 3.0 # 3 + will be marked as spam
- Next, we need to change the Postfix settings to pass e-mails through spam-assassin. Open
/etc/postfix/master.cfand find the following line:smtp inet n - - - - smtpd
- Add the content filtering option:
-o content_filter=spamassassin
- Define the content filter block by adding the following lines to the end of the file:
spamassassin unix - n n - - pipe user=spamd argv=/usr/bin/spamc -f -e /usr/sbin/sendmail -oi -f ${sender} ${recipient}
- Finally, restart spam-assassin and Postfix:
$ sudo service spamassassin start $ sudo service postfix reload
- You can check spam-assassin and mail logs to verify that spam-assassin is working properly:
$ less /var/log/spamassassin/spamd.log $ less /var/log/mail.log
How it works…
Spam filtering works with the help of a piping mechanism provided by Postfix. We have created a new Unix pipe which will be used to filter e-mails. Postfix will pass all e-mails through this pipe, which will be then scanned through spam-assassin to determine the spam score. If given e-mail scores below the configured threshold, then it passes the filter without any modification; otherwise, spam-assassin adds a spam header to the e-mail.
Spam-assassin works with a Bayesian classifier to classify e-mails as spam or not spam. Basically, it checks the content of the e-mail and determines the score based on content.
There's more…
You can train spam-assassin's Bayesian classifier to get more accurate spam detections.
The following command will train spam-assassin with spam contents (--spam):
$ sudo sa-learn --spam -u spamd --dir ~/Maildir/.Junk/* -D
To train with non-spam content, use the following command (--ham):
$ sudo sa-learn --ham -u spamd --dir ~/Maildir/.INBOX/* -D
If you are using the mbox format, replace --dir ~/Maildir/.Junk/* with the option --mbox.
See also
- Sa-learn - train SpamAssassin's Bayesian classifier at https://spamassassin.apache.org/full/3.2.x/doc/sa-learn.html and https://wiki.apache.org/spamassassin/BayesInSpamAssassin
- Learn about Bayesian classification at https://en.wikipedia.org/wiki/Naive_Bayes_classifier
How it works…
Spam filtering works with the help of a piping mechanism provided by Postfix. We have created a new Unix pipe which will be used to filter e-mails. Postfix will pass all e-mails through this pipe, which will be then scanned through spam-assassin to determine the spam score. If given e-mail scores below the configured threshold, then it passes the filter without any modification; otherwise, spam-assassin adds a spam header to the e-mail.
Spam-assassin works with a Bayesian classifier to classify e-mails as spam or not spam. Basically, it checks the content of the e-mail and determines the score based on content.
There's more…
You can train spam-assassin's Bayesian classifier to get more accurate spam detections.
The following command will train spam-assassin with spam contents (--spam):
$ sudo sa-learn --spam -u spamd --dir ~/Maildir/.Junk/* -D
To train with non-spam content, use the following command (--ham):
$ sudo sa-learn --ham -u spamd --dir ~/Maildir/.INBOX/* -D
If you are using the mbox format, replace --dir ~/Maildir/.Junk/* with the option --mbox.
See also
- Sa-learn - train SpamAssassin's Bayesian classifier at https://spamassassin.apache.org/full/3.2.x/doc/sa-learn.html and https://wiki.apache.org/spamassassin/BayesInSpamAssassin
- Learn about Bayesian classification at https://en.wikipedia.org/wiki/Naive_Bayes_classifier
There's more…
You can train spam-assassin's Bayesian classifier to get more accurate spam detections.
The following command will train spam-assassin with spam contents (--spam):
$ sudo sa-learn --spam -u spamd --dir ~/Maildir/.Junk/* -D
To train with non-spam content, use the following command (--ham):
$ sudo sa-learn --ham -u spamd --dir ~/Maildir/.INBOX/* -D
If you are using the mbox format, replace --dir ~/Maildir/.Junk/* with the option --mbox.
See also
- Sa-learn - train SpamAssassin's Bayesian classifier at https://spamassassin.apache.org/full/3.2.x/doc/sa-learn.html and https://wiki.apache.org/spamassassin/BayesInSpamAssassin
- Learn about Bayesian classification at https://en.wikipedia.org/wiki/Naive_Bayes_classifier
See also
- Sa-learn - train SpamAssassin's Bayesian classifier at https://spamassassin.apache.org/full/3.2.x/doc/sa-learn.html and https://wiki.apache.org/spamassassin/BayesInSpamAssassin
- Learn about Bayesian classification at https://en.wikipedia.org/wiki/Naive_Bayes_classifier
Troubleshooting the mail server
Sometimes you may face problems such as e-mails not being sent, delayed delivery or mail bouncing, issues while fetching e-mails, and login failures. In this recipe, we will learn how to identify the exact problem behind these issues. We will learn how to use debugging tools and read the logs of Postfix and Dovecot.
Getting ready
You will need access to a root account or an account with sudo privileges.
It is assumed that you have already installed Postfix and Dovecot servers.
How to do it…
Follow these steps to troubleshoot the mail server:
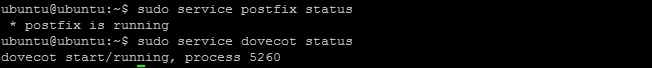
- Start with checking the status of Postfix and Dovecot. If you get output that says
stop/waitingornot runningthen the respective service is not running:$ sudo service postfix status $ sudo service dovecot status
- Try to restart the respective services. Restarting may give you error messages. Also check for startup logs under
/var/log/mail.log:$ sudo service postfix restart $ less /var/log/mail.log
- You can use a
tailcommand to monitor the stream of logs while the service is running. You can easily filter the output oftailby piping it to agrepcommand:$ tail -f /var/log/mail.logUse
grepto only view selected logs:$ tail -f /var/log/mail.log | grep "dovecot"
- Use
grep -vto filter/remove selected logs:$ tail -f /var/log/mail.log | grep -v "dovecot"
- You can check other log files such as
/var/log/mail.errand/var/log/upstart/dovecot.log.You may want to enable verbose logging to get detailed debugging information. To enable debug mode on Dovecot, edit
10-logging.confand enableauth_verboseandmail_debugvariables:$ sudo nano /etc/dovecot/conf.d/10-logging.confauth_verbose = yes mail_debug = yes
Restart Dovecot:
$ sudo service dovecot restart - To enable verbose logging on Postfix, edit
master.cffile and add the-vargument:$ sudo nano /etc/postfix/master.cf smtp inet n - - - - smtpd -v
Restart Postfix.
- Turn off chroot operations:
$ sudo nano /etc/postfix/master.cf smtp inet n - n - - smtpd
- Check user account with Dovecot:
$ doveadm username useremail@example.com - If you have set virtual users, check if they are working properly:
$ postmap -q bob@example.org mysql:/etc/postfix/mysql-virtual-maps - Check respective ports used by Postfix and Dovecot. Postfix uses ports
25,465,587and Dovecot uses port993and995:$ telnet localhost 993 - Check
netstatto make sure services are listening:$ sudo netstat -plutn
- Check for DNS resolution and MX records:
$ host -t mx example.com - Check if spam filters and antivirus scanners are working properly.
See also
- Postfix debugging - http://www.postfix.org/DEBUG_README.html
- Postfix book (troubleshooting) at http://www.postfix-book.com/debugging.html
- Dovecot troubleshooting at http://wiki2.dovecot.org/WhyDoesItNotWork
Getting ready
You will need access to a root account or an account with sudo privileges.
It is assumed that you have already installed Postfix and Dovecot servers.
How to do it…
Follow these steps to troubleshoot the mail server:
- Start with checking the status of Postfix and Dovecot. If you get output that says
stop/waitingornot runningthen the respective service is not running:$ sudo service postfix status $ sudo service dovecot status

- Try to restart the respective services. Restarting may give you error messages. Also check for startup logs under
/var/log/mail.log:$ sudo service postfix restart $ less /var/log/mail.log
- You can use a
tailcommand to monitor the stream of logs while the service is running. You can easily filter the output oftailby piping it to agrepcommand:$ tail -f /var/log/mail.logUse
grepto only view selected logs:$ tail -f /var/log/mail.log | grep "dovecot"
- Use
grep -vto filter/remove selected logs:$ tail -f /var/log/mail.log | grep -v "dovecot"
- You can check other log files such as
/var/log/mail.errand/var/log/upstart/dovecot.log.You may want to enable verbose logging to get detailed debugging information. To enable debug mode on Dovecot, edit
10-logging.confand enableauth_verboseandmail_debugvariables:$ sudo nano /etc/dovecot/conf.d/10-logging.confauth_verbose = yes mail_debug = yes
Restart Dovecot:
$ sudo service dovecot restart - To enable verbose logging on Postfix, edit
master.cffile and add the-vargument:$ sudo nano /etc/postfix/master.cf smtp inet n - - - - smtpd -v
Restart Postfix.
- Turn off chroot operations:
$ sudo nano /etc/postfix/master.cf smtp inet n - n - - smtpd
- Check user account with Dovecot:
$ doveadm username useremail@example.com - If you have set virtual users, check if they are working properly:
$ postmap -q bob@example.org mysql:/etc/postfix/mysql-virtual-maps - Check respective ports used by Postfix and Dovecot. Postfix uses ports
25,465,587and Dovecot uses port993and995:$ telnet localhost 993 - Check
netstatto make sure services are listening:$ sudo netstat -plutn
- Check for DNS resolution and MX records:
$ host -t mx example.com - Check if spam filters and antivirus scanners are working properly.
See also
- Postfix debugging - http://www.postfix.org/DEBUG_README.html
- Postfix book (troubleshooting) at http://www.postfix-book.com/debugging.html
- Dovecot troubleshooting at http://wiki2.dovecot.org/WhyDoesItNotWork
How to do it…
Follow these steps to troubleshoot the mail server:
- Start with checking the status of Postfix and Dovecot. If you get output that says
stop/waitingornot runningthen the respective service is not running:$ sudo service postfix status $ sudo service dovecot status

- Try to restart the respective services. Restarting may give you error messages. Also check for startup logs under
/var/log/mail.log:$ sudo service postfix restart $ less /var/log/mail.log
- You can use a
tailcommand to monitor the stream of logs while the service is running. You can easily filter the output oftailby piping it to agrepcommand:$ tail -f /var/log/mail.logUse
grepto only view selected logs:$ tail -f /var/log/mail.log | grep "dovecot"
- Use
grep -vto filter/remove selected logs:$ tail -f /var/log/mail.log | grep -v "dovecot"
- You can check other log files such as
/var/log/mail.errand/var/log/upstart/dovecot.log.You may want to enable verbose logging to get detailed debugging information. To enable debug mode on Dovecot, edit
10-logging.confand enableauth_verboseandmail_debugvariables:$ sudo nano /etc/dovecot/conf.d/10-logging.confauth_verbose = yes mail_debug = yes
Restart Dovecot:
$ sudo service dovecot restart - To enable verbose logging on Postfix, edit
master.cffile and add the-vargument:$ sudo nano /etc/postfix/master.cf smtp inet n - - - - smtpd -v
Restart Postfix.
- Turn off chroot operations:
$ sudo nano /etc/postfix/master.cf smtp inet n - n - - smtpd
- Check user account with Dovecot:
$ doveadm username useremail@example.com - If you have set virtual users, check if they are working properly:
$ postmap -q bob@example.org mysql:/etc/postfix/mysql-virtual-maps - Check respective ports used by Postfix and Dovecot. Postfix uses ports
25,465,587and Dovecot uses port993and995:$ telnet localhost 993 - Check
netstatto make sure services are listening:$ sudo netstat -plutn
- Check for DNS resolution and MX records:
$ host -t mx example.com - Check if spam filters and antivirus scanners are working properly.
See also
- Postfix debugging - http://www.postfix.org/DEBUG_README.html
- Postfix book (troubleshooting) at http://www.postfix-book.com/debugging.html
- Dovecot troubleshooting at http://wiki2.dovecot.org/WhyDoesItNotWork
See also
- Postfix debugging - http://www.postfix.org/DEBUG_README.html
- Postfix book (troubleshooting) at http://www.postfix-book.com/debugging.html
- Dovecot troubleshooting at http://wiki2.dovecot.org/WhyDoesItNotWork
Installing the Zimbra mail server
Until now, we have installed Postfix, Dovecot, spam-assassin, and other tools separately. In this recipe, we will learn how to install the Zimbra collaboration server, which covers all tools in a single package. The Zimbra server contains Postfix, MySQL, OpenLDAP, ClamAV, and Spam-Assassin, Calendar, and various other features. Zimbra provides a paid option as well as an open source version. We will be installing an open source version of the Zimbra server in single server mode.
Getting ready
As always, you will need access to a root account or an account with sudo privileges.
For Zimbra to work properly, you will need the following minimum configuration for your server:
- At least 1.5 GHz of CPU 2 GHz recommended
- Minimum 8 GB of memory
- Minimum 10 GB of storage 20 GB recommended
You will need to set proper DNS and MX records for your domain.
You will also need various ports, as follows:
- Postfix/LMTP 25, 7025
- HTTP 80, 443
- POP3 110, 995
- IMAP 143, 993
- LDAP 389
How to do it…
Follow these steps to install Zimbra collaboration server:
- Install the dependency packages before starting with the Zimbra installation:
$ sudo apt-get update $ sudo apt-get install libperl5.18 libaio1 unzip pax sysstat sqlite3 libgmp10
- Download and extract the Zimbra open source package using the following command:
$ wget https://files.zimbra.com/downloads/8.6.0_GA/zcs-8.6.0_GA_1153.UBUNTU14_64.20141215151116.tgz $ tar -zxvf zcs-8.6.0_GA_1153.UBUNTU14_64.20141215151116.tgz $ cd zcs-8.6.0_GA_1153.UBUNTU14_64.20141215151116
- Make sure you have set the proper hostname and hosts entries in respective files:
$ cat /etc/hosts 127.0.0.1 localhost 119.9.107.28 mail.server.local mail $ cat /etc/hostname mail.server.local
- Start the Zimbra installation by executing the installer:
$ sudo ./install.sh - The installation process will ask you to agree with License Agreement. Type
yand press Enter to continue:
- On acceptance of agreement, Zimbra will check for dependencies and then ask for the component selection. I have chosen to skip a few components. Type
ywhen asked for confirmation:
- Type
ywhen asked for package selection confirmation. - The installation process will take some time. As installation completes, the Zimbra configuration menu will be displayed. Here, you need to set an admin account password:

- On the main menu, select
6to choosezimbra-storeand then type4for the admin password. The new prompt will ask for the admin account password:
- Then, type
rto come back to the main menu and then typeato apply settings, and again press Enter to save settings:
- Finally, apply all configurations when asked. Zimbra will ask you to send installation notification to Zimbra. Choose
Yesby typingyto notify Zimbra:
- Now you can access your Zimbra server with the domain name of your server or IP address. Your browser may prompt for a non-trusted server certificate, as shown in the following screenshot:

- You can access the Inbox panel on port
7071,https://yourserver.tld:7071.
How it works…
Zimbra combines various commonly used packages in a single package and provides a web interface to work with them. It reduces the efforts required in installing and configuring all tools separately. For any additional features, you can always switch to the Zimbra collaboration server, Network Edition.
There's more…
If you are planning to use Zimbra on your local network, you will need a DNS server set up. Alternatively, you can use the tool dnsmasq. It is a small package that sets up a quick DNS environment on your local network.
See also
- Zimbra open source features at https://www.zimbra.com/open-source/features
Getting ready
As always, you will need access to a root account or an account with sudo privileges.
For Zimbra to work properly, you will need the following minimum configuration for your server:
- At least 1.5 GHz of CPU 2 GHz recommended
- Minimum 8 GB of memory
- Minimum 10 GB of storage 20 GB recommended
You will need to set proper DNS and MX records for your domain.
You will also need various ports, as follows:
- Postfix/LMTP 25, 7025
- HTTP 80, 443
- POP3 110, 995
- IMAP 143, 993
- LDAP 389
How to do it…
Follow these steps to install Zimbra collaboration server:
- Install the dependency packages before starting with the Zimbra installation:
$ sudo apt-get update $ sudo apt-get install libperl5.18 libaio1 unzip pax sysstat sqlite3 libgmp10
- Download and extract the Zimbra open source package using the following command:
$ wget https://files.zimbra.com/downloads/8.6.0_GA/zcs-8.6.0_GA_1153.UBUNTU14_64.20141215151116.tgz $ tar -zxvf zcs-8.6.0_GA_1153.UBUNTU14_64.20141215151116.tgz $ cd zcs-8.6.0_GA_1153.UBUNTU14_64.20141215151116
- Make sure you have set the proper hostname and hosts entries in respective files:
$ cat /etc/hosts 127.0.0.1 localhost 119.9.107.28 mail.server.local mail $ cat /etc/hostname mail.server.local
- Start the Zimbra installation by executing the installer:
$ sudo ./install.sh - The installation process will ask you to agree with License Agreement. Type
yand press Enter to continue:
- On acceptance of agreement, Zimbra will check for dependencies and then ask for the component selection. I have chosen to skip a few components. Type
ywhen asked for confirmation:
- Type
ywhen asked for package selection confirmation. - The installation process will take some time. As installation completes, the Zimbra configuration menu will be displayed. Here, you need to set an admin account password:

- On the main menu, select
6to choosezimbra-storeand then type4for the admin password. The new prompt will ask for the admin account password:
- Then, type
rto come back to the main menu and then typeato apply settings, and again press Enter to save settings:
- Finally, apply all configurations when asked. Zimbra will ask you to send installation notification to Zimbra. Choose
Yesby typingyto notify Zimbra:
- Now you can access your Zimbra server with the domain name of your server or IP address. Your browser may prompt for a non-trusted server certificate, as shown in the following screenshot:

- You can access the Inbox panel on port
7071,https://yourserver.tld:7071.
How it works…
Zimbra combines various commonly used packages in a single package and provides a web interface to work with them. It reduces the efforts required in installing and configuring all tools separately. For any additional features, you can always switch to the Zimbra collaboration server, Network Edition.
There's more…
If you are planning to use Zimbra on your local network, you will need a DNS server set up. Alternatively, you can use the tool dnsmasq. It is a small package that sets up a quick DNS environment on your local network.
See also
- Zimbra open source features at https://www.zimbra.com/open-source/features
How to do it…
Follow these steps to install Zimbra collaboration server:
- Install the dependency packages before starting with the Zimbra installation:
$ sudo apt-get update $ sudo apt-get install libperl5.18 libaio1 unzip pax sysstat sqlite3 libgmp10
- Download and extract the Zimbra open source package using the following command:
$ wget https://files.zimbra.com/downloads/8.6.0_GA/zcs-8.6.0_GA_1153.UBUNTU14_64.20141215151116.tgz $ tar -zxvf zcs-8.6.0_GA_1153.UBUNTU14_64.20141215151116.tgz $ cd zcs-8.6.0_GA_1153.UBUNTU14_64.20141215151116
- Make sure you have set the proper hostname and hosts entries in respective files:
$ cat /etc/hosts 127.0.0.1 localhost 119.9.107.28 mail.server.local mail $ cat /etc/hostname mail.server.local
- Start the Zimbra installation by executing the installer:
$ sudo ./install.sh - The installation process will ask you to agree with License Agreement. Type
yand press Enter to continue:
- On acceptance of agreement, Zimbra will check for dependencies and then ask for the component selection. I have chosen to skip a few components. Type
ywhen asked for confirmation:
- Type
ywhen asked for package selection confirmation. - The installation process will take some time. As installation completes, the Zimbra configuration menu will be displayed. Here, you need to set an admin account password:

- On the main menu, select
6to choosezimbra-storeand then type4for the admin password. The new prompt will ask for the admin account password:
- Then, type
rto come back to the main menu and then typeato apply settings, and again press Enter to save settings:
- Finally, apply all configurations when asked. Zimbra will ask you to send installation notification to Zimbra. Choose
Yesby typingyto notify Zimbra:
- Now you can access your Zimbra server with the domain name of your server or IP address. Your browser may prompt for a non-trusted server certificate, as shown in the following screenshot:

- You can access the Inbox panel on port
7071,https://yourserver.tld:7071.
How it works…
Zimbra combines various commonly used packages in a single package and provides a web interface to work with them. It reduces the efforts required in installing and configuring all tools separately. For any additional features, you can always switch to the Zimbra collaboration server, Network Edition.
There's more…
If you are planning to use Zimbra on your local network, you will need a DNS server set up. Alternatively, you can use the tool dnsmasq. It is a small package that sets up a quick DNS environment on your local network.
See also
- Zimbra open source features at https://www.zimbra.com/open-source/features
How it works…
Zimbra combines various commonly used packages in a single package and provides a web interface to work with them. It reduces the efforts required in installing and configuring all tools separately. For any additional features, you can always switch to the Zimbra collaboration server, Network Edition.
There's more…
If you are planning to use Zimbra on your local network, you will need a DNS server set up. Alternatively, you can use the tool dnsmasq. It is a small package that sets up a quick DNS environment on your local network.
See also
- Zimbra open source features at https://www.zimbra.com/open-source/features
There's more…
If you are planning to use Zimbra on your local network, you will need a DNS server set up. Alternatively, you can use the tool dnsmasq. It is a small package that sets up a quick DNS environment on your local network.
See also
- Zimbra open source features at https://www.zimbra.com/open-source/features
See also
- Zimbra open source features at https://www.zimbra.com/open-source/features
























































