Kali Linux is known as one of the best hacking distributions, providing an entire arsenal of penetration testing tools. The developers recently released Kali Linux 2016.2, which solidified their efforts in making it a rolling distribution. Different desktop environments have been released alongside GNOME in this release, such as e17, LXDE, Xfce, MATE, and KDE. Kali Linux will be kept updated with the latest improvements and tools by weekly updated ISOs. For the purposes of this book, we will be using Kali Linux 2016.2 with GNOME as our development environment for many of the scanning scripts that will be discussed throughout this book.
Installing Kali Linux
Getting ready
Prior to installing Kali Linux in your virtual security testing lab, you will need to acquire
the ISO file (image file) from a trusted source. The Kali Linux ISO can be downloaded at http://www.kali.org/downloads/.
How to do it...
These steps will guide you to install Kali Linux on the VM:
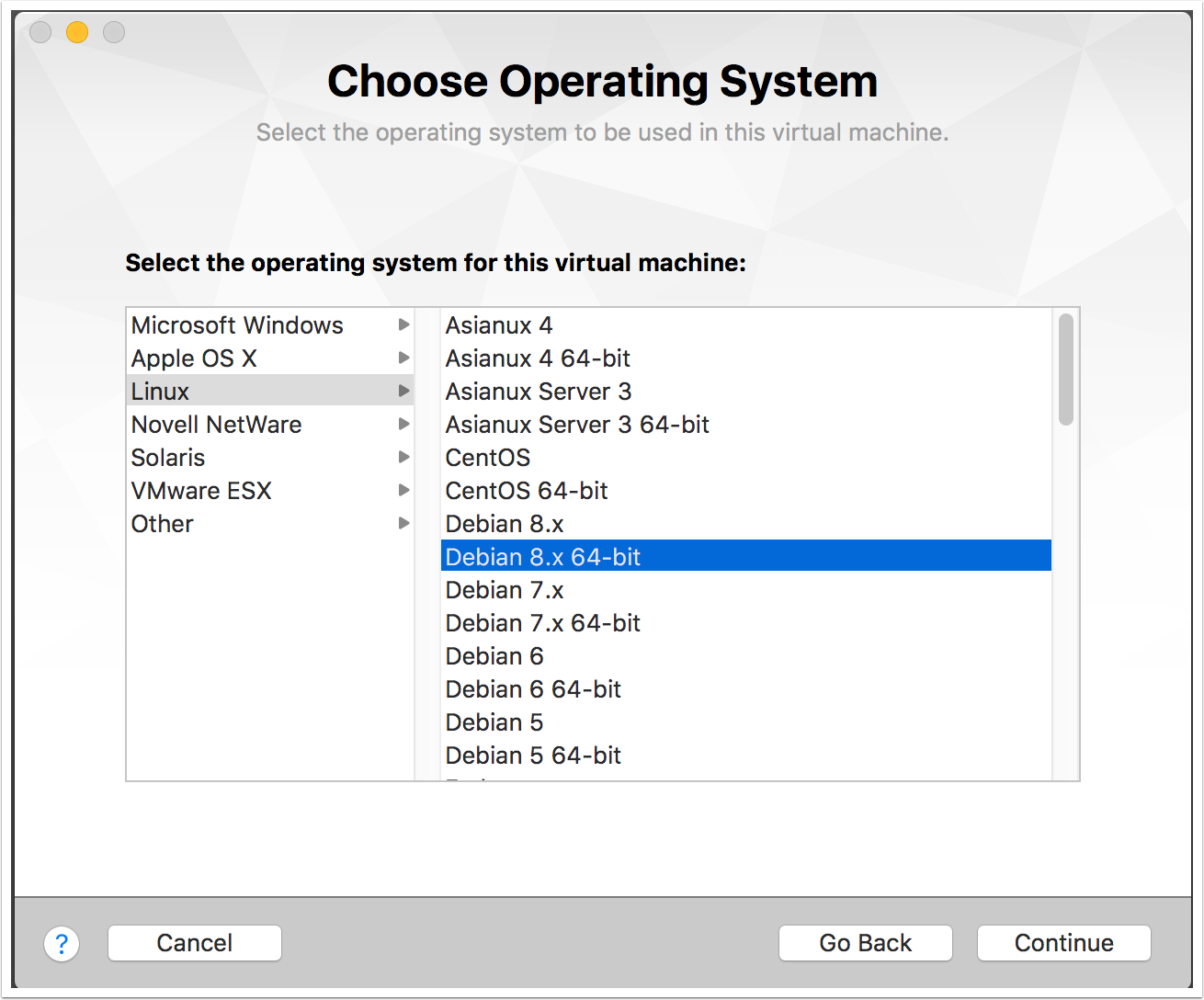
- After selecting the Kali Linux ISO file, you will be asked what operating system you are installing. Currently Kali Linux is built on Debian 8.x. Choose this and click on Continue:
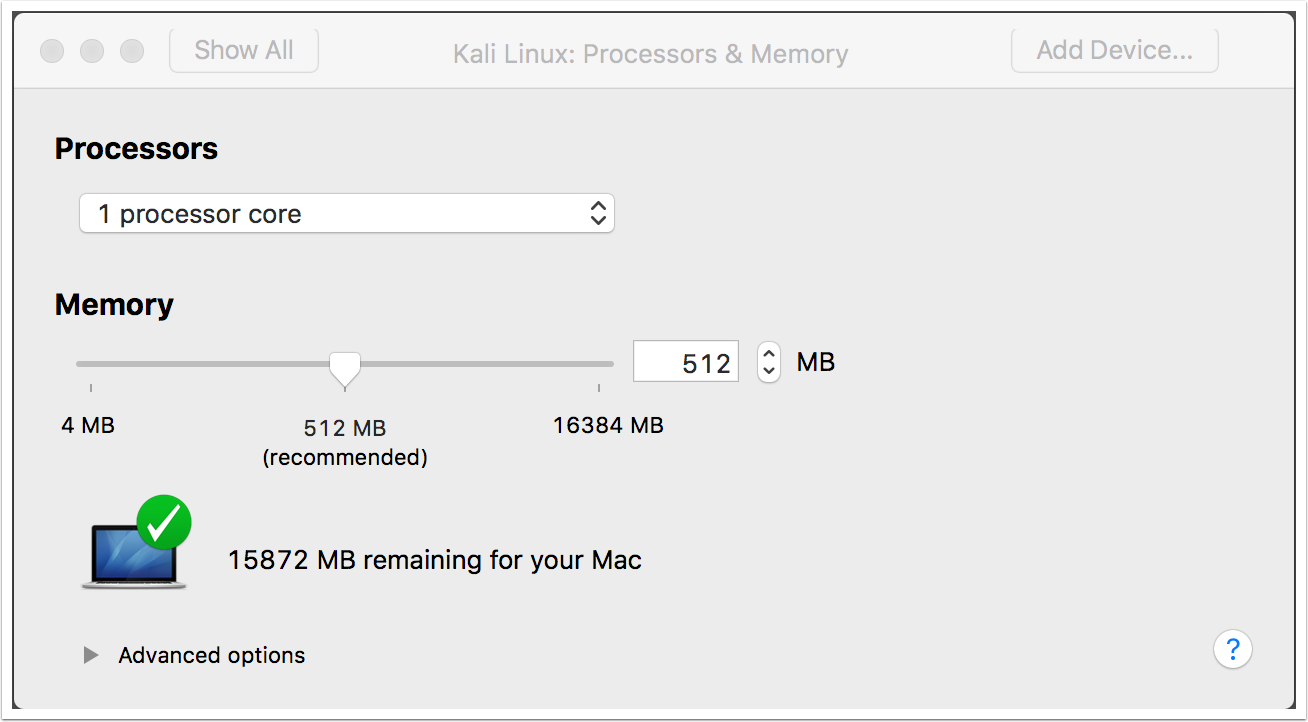
- You will see a finish screen, but let's customize the settings first. Kali Linux requires at least 15 GB of hard disk space and a minimum of 512 MB RAM:
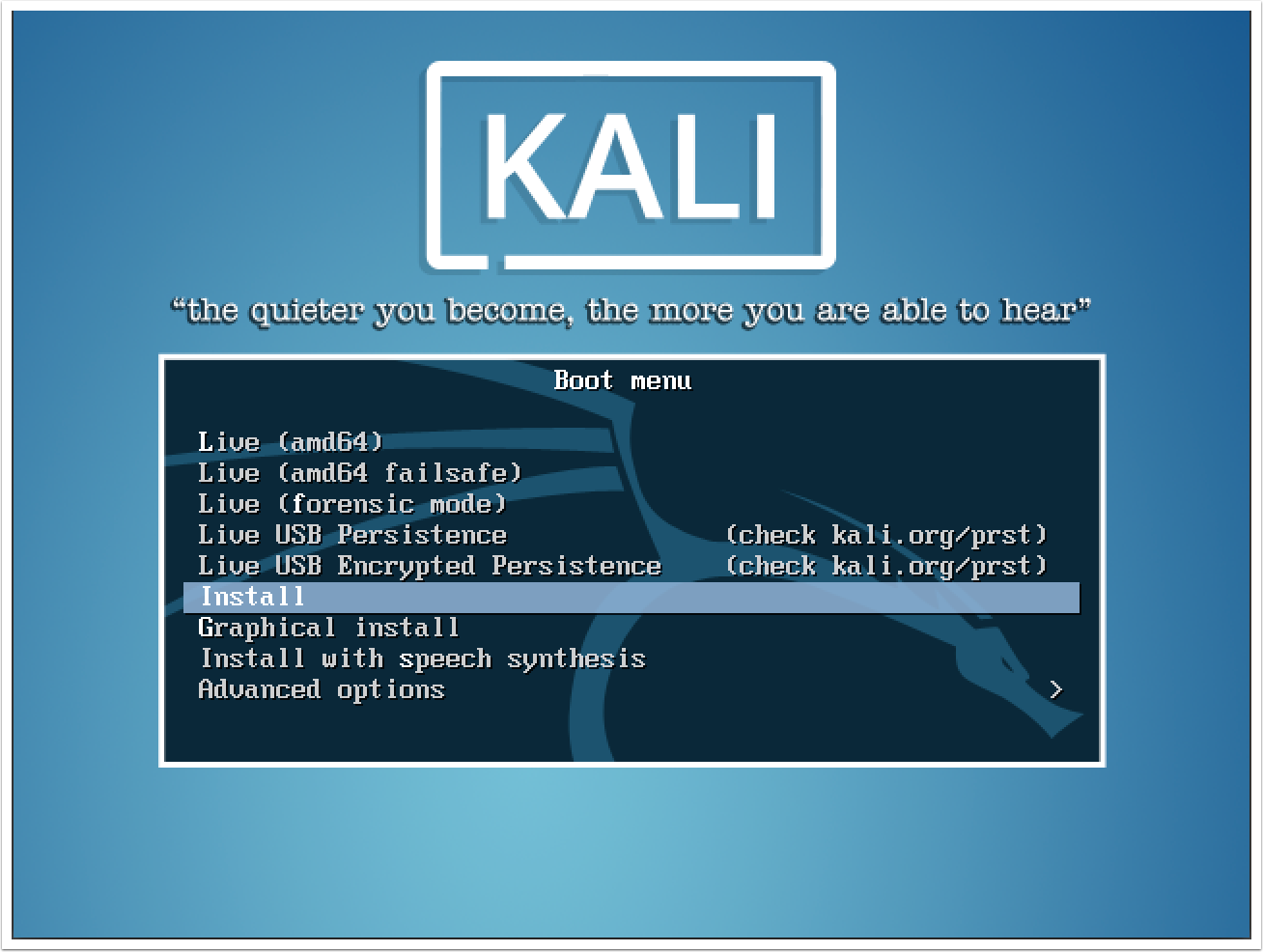
- After booting from the Kali Linux image file, you will be presented with the initial boot menu. Here, scroll down to the sixth option, Install, and press the Enter key to start the installation process:
- Once it has started, you will be guided through a series of questions to complete the installation process. Initially, you will be asked to provide your location (country) and language. You will then be provided with an option to manually select your keyboard configuration or use a guided detection process.
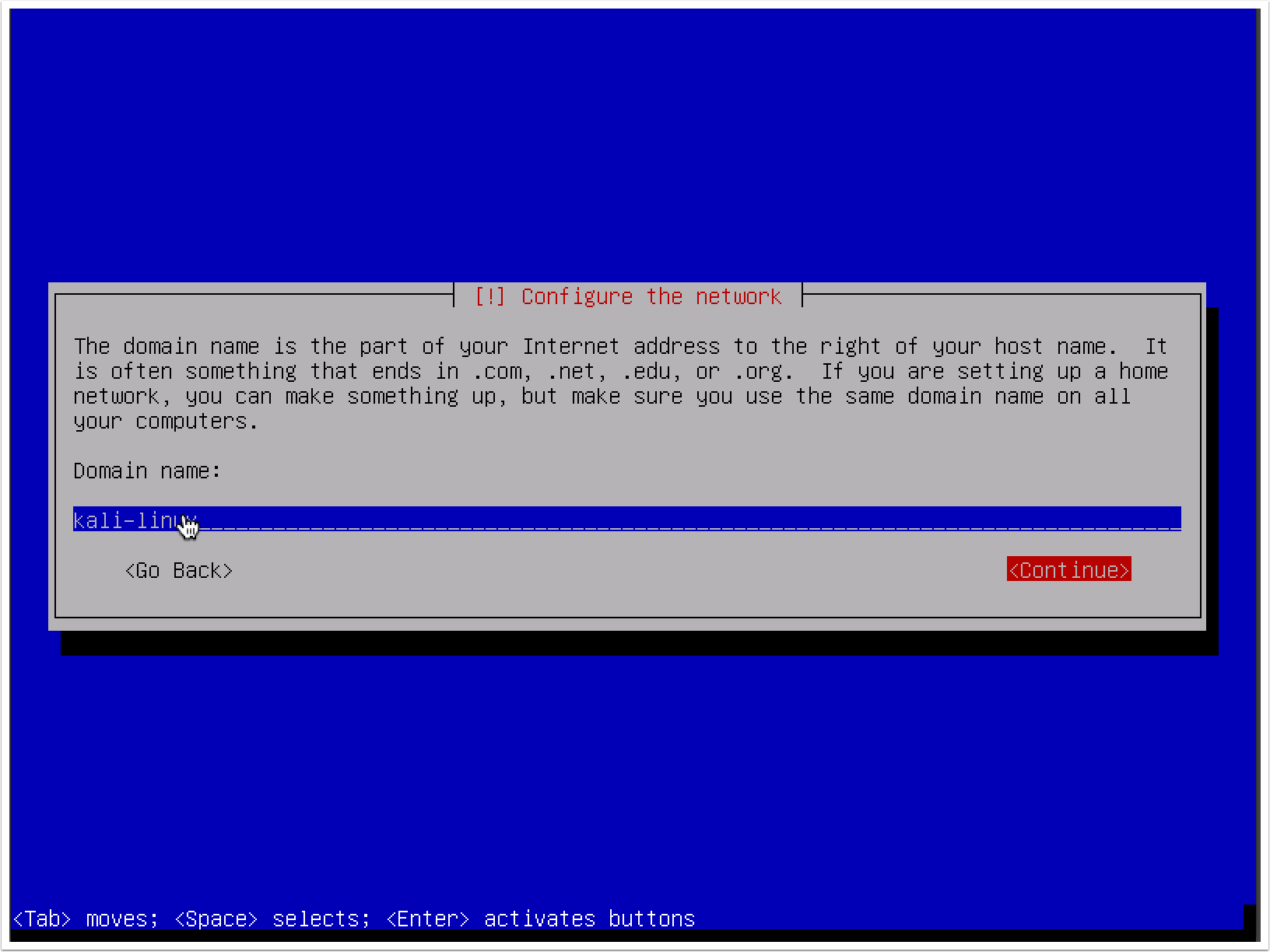
- The next step will request that you provide a hostname for the system. If the system will be joined to a domain, ensure that the hostname is unique, as shown in the following screenshot:
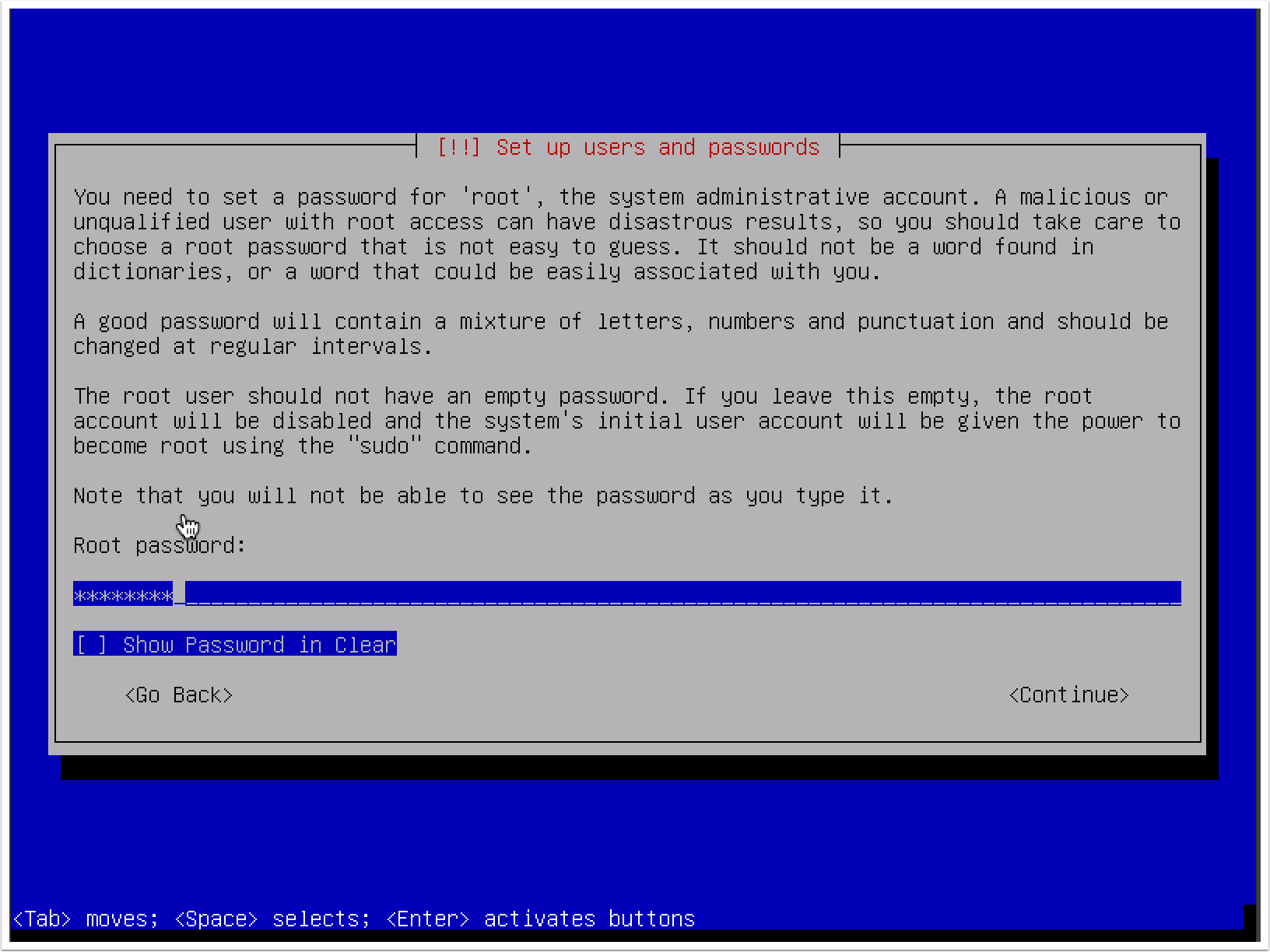
- Next, you will need to set the password for the root account. It is recommended that this be a fairly complex password that will not be easily compromised. Have a look at the following screenshot:
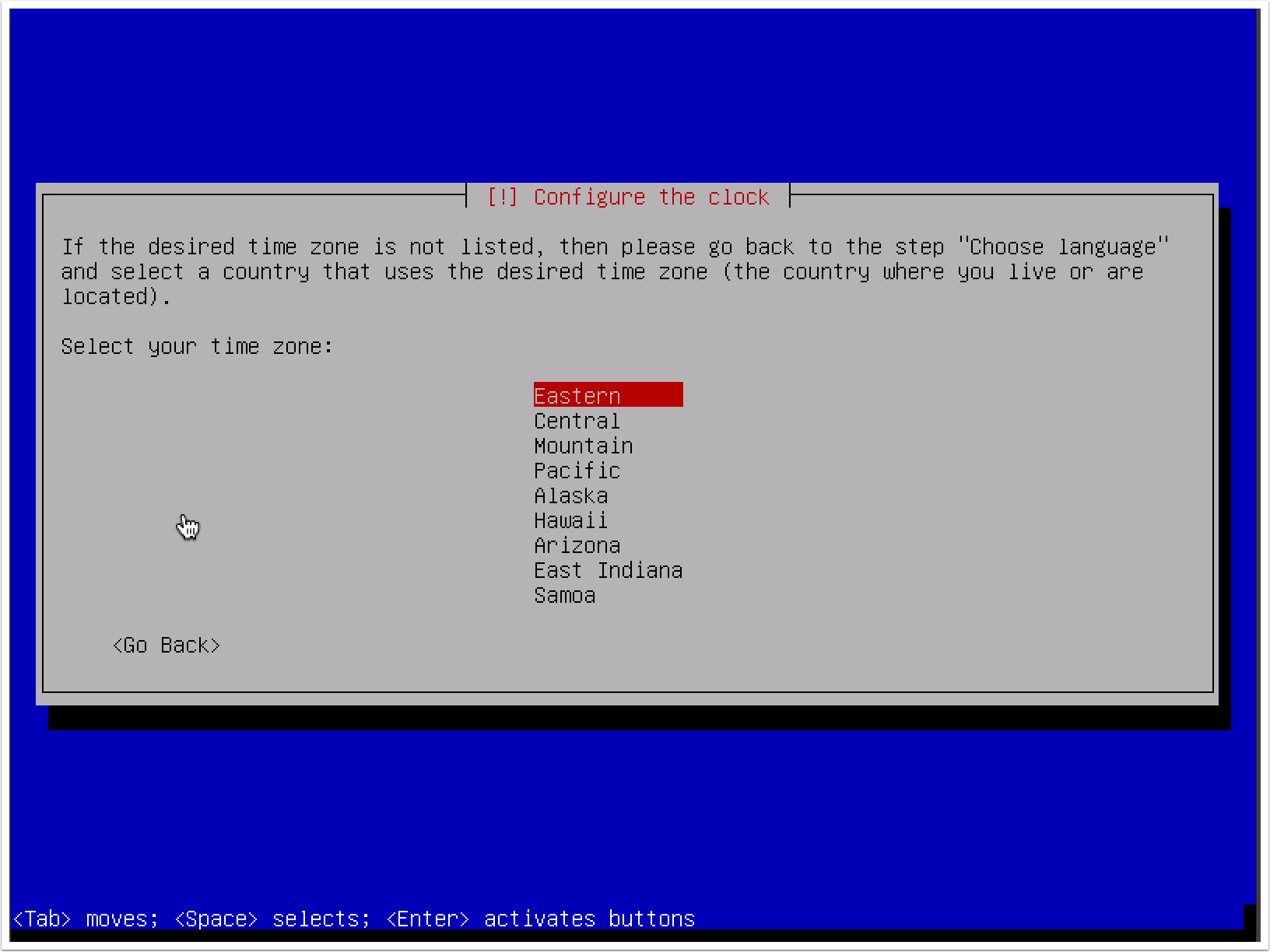
- Next, you will be asked to provide the time zone you are located in. The system will use IP geolocation to provide its best guess of your location. If this is not correct, manually select the correct time zone:
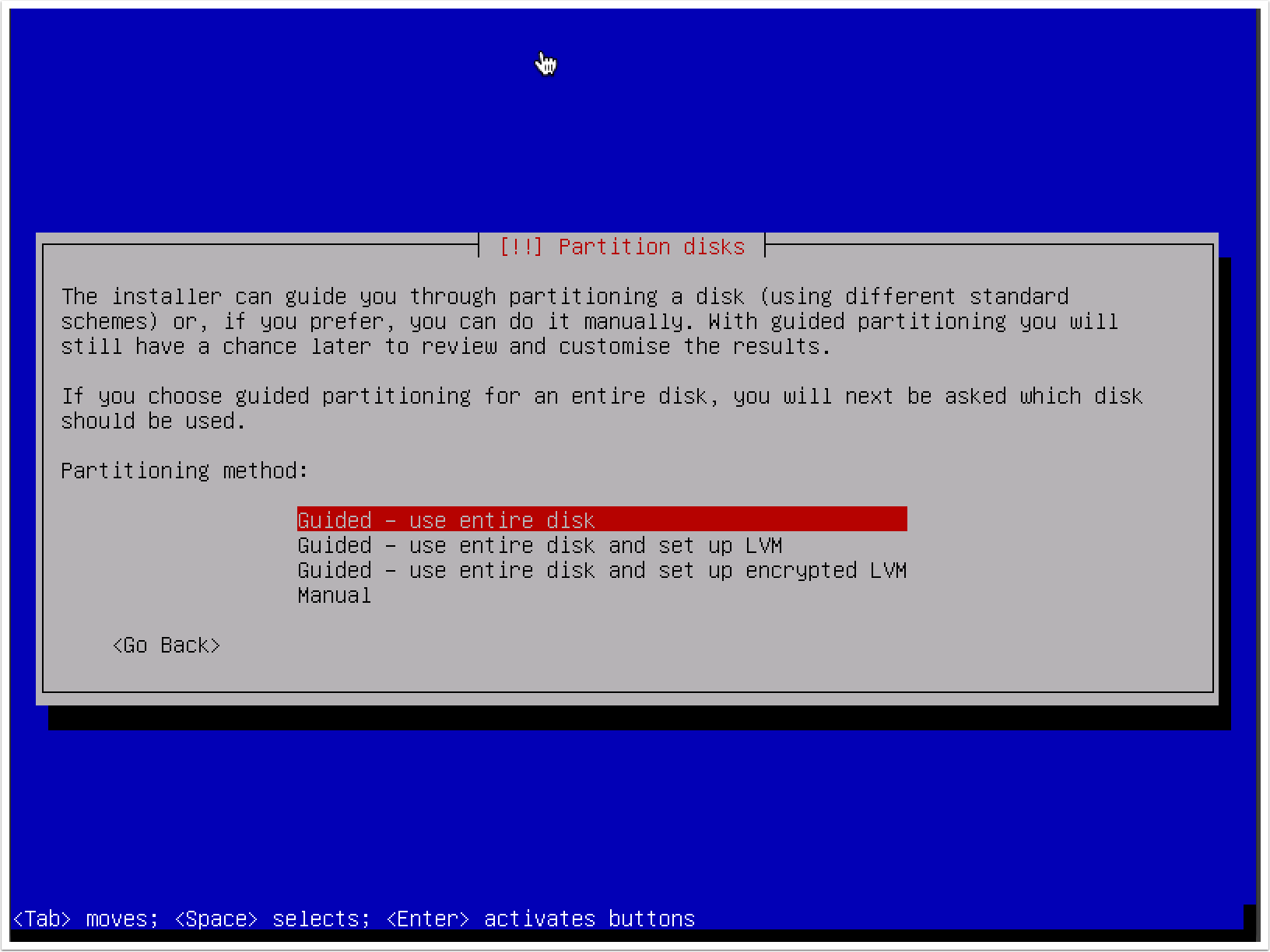
- For setting up your disk partition, using the default method and partitioning scheme should be sufficient for lab purposes:
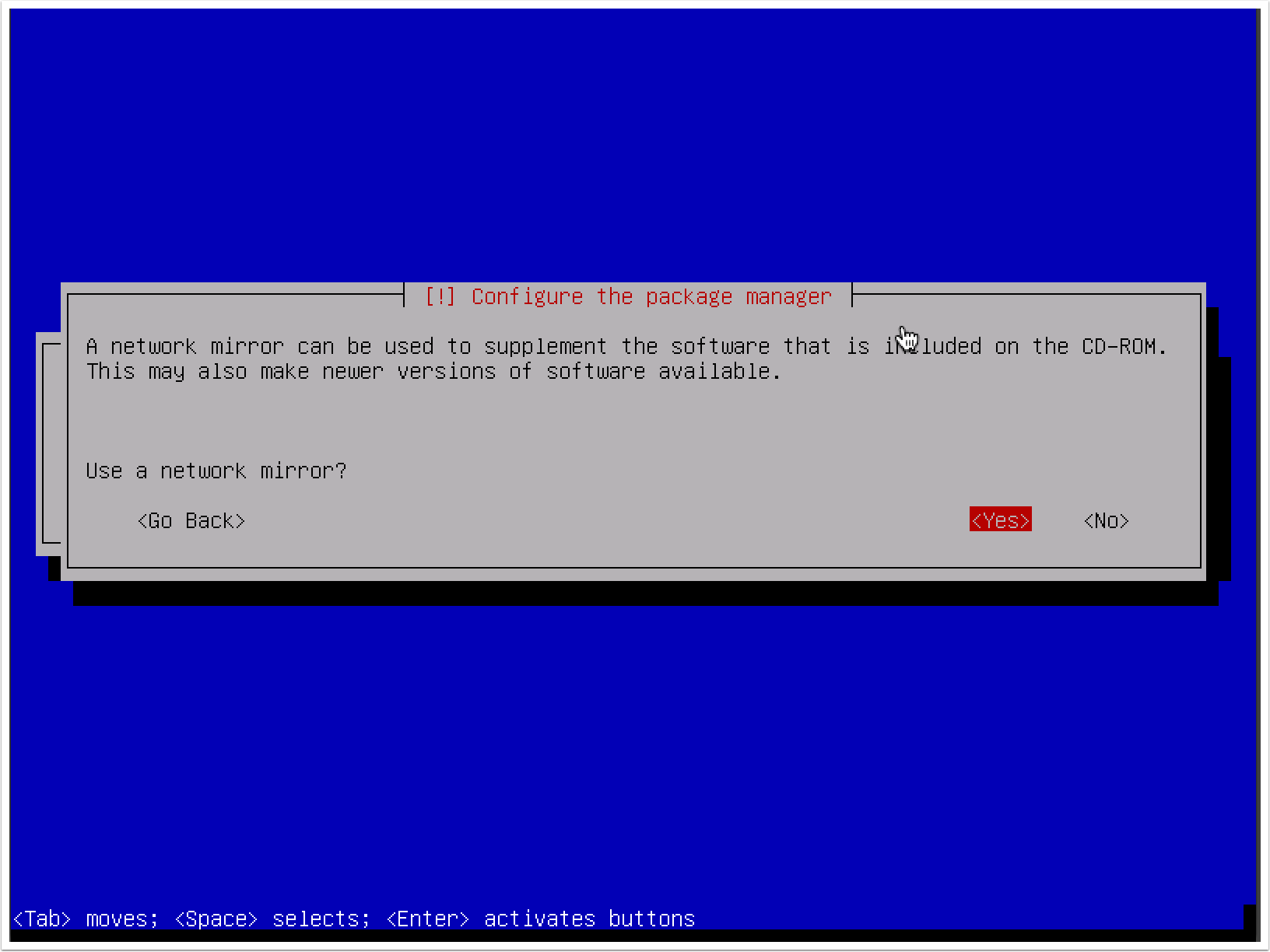
- It is recommended that you use a mirror to ensure that your software in Kali Linux is kept up to date:
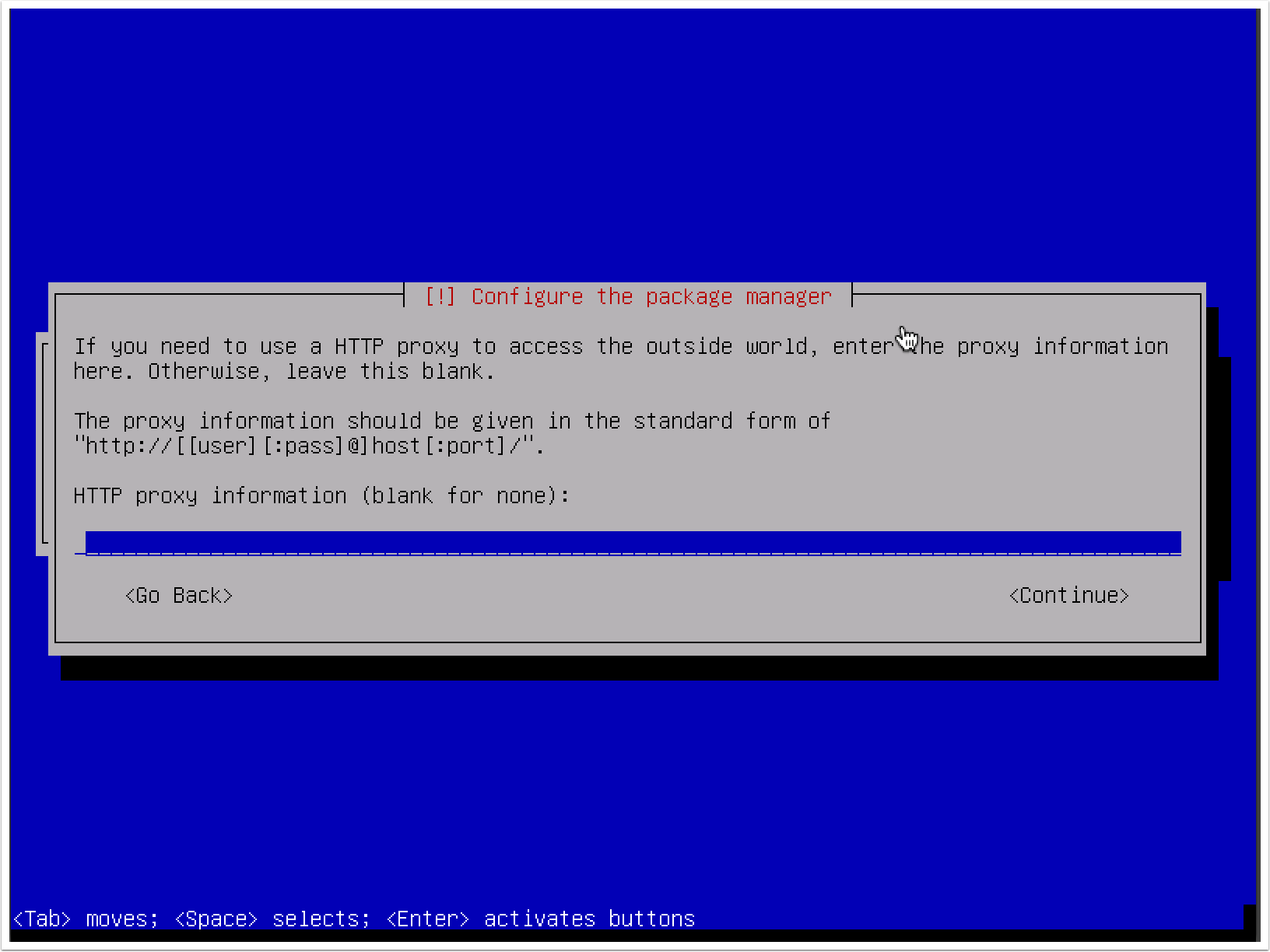
- Next, you will be asked to provide an HTTP proxy address. An external HTTP proxy is not required for any of the exercises addressed in this book, so this can be left blank:
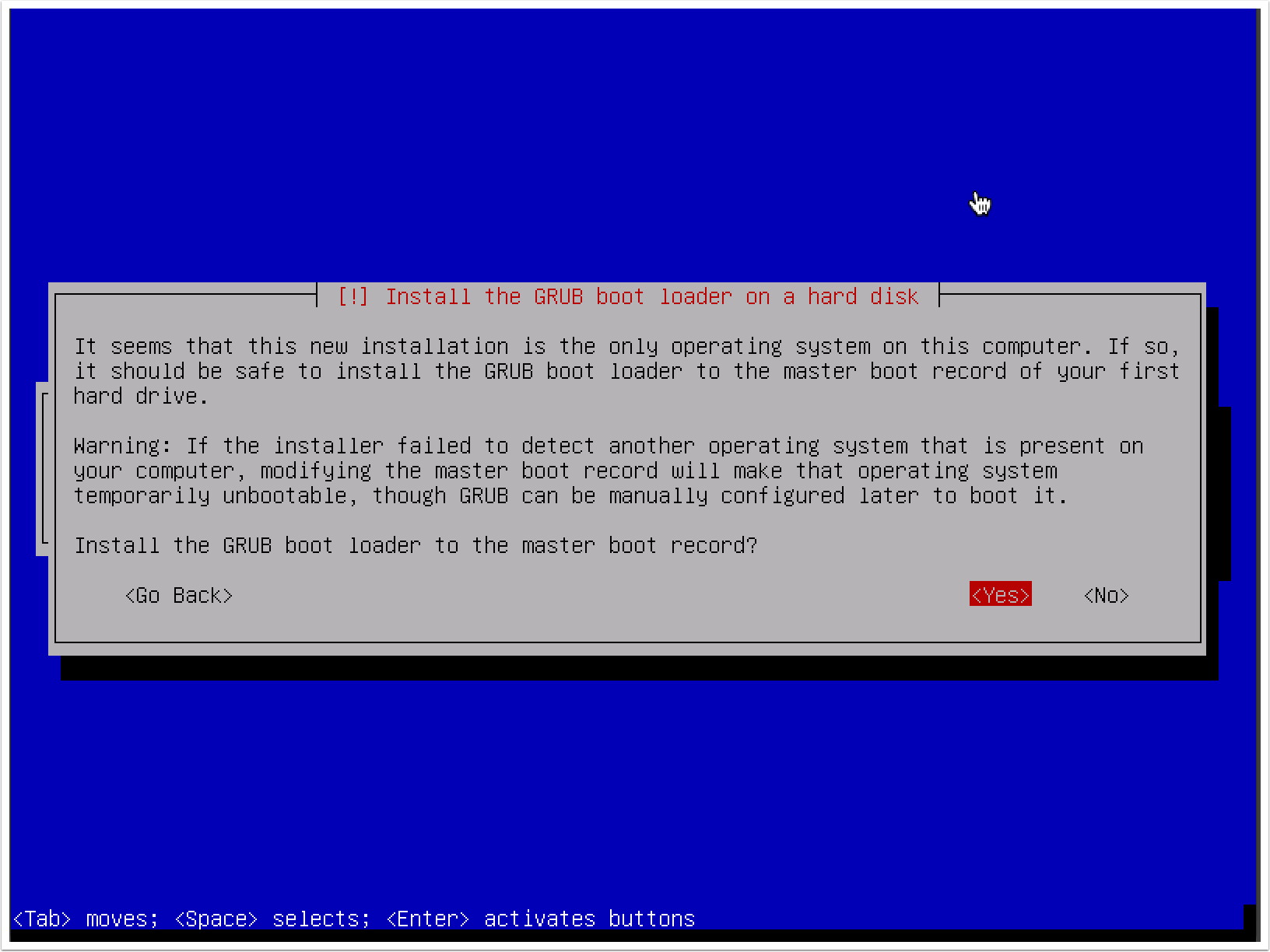
- Finally, choose Yes to install the GRUB boot loader and then press the Enter key to complete the installation process. When the system loads, you can log in with the root account and the password provided during the installation:
How it works...
Kali Linux is a Debian Linux distribution that has a large number of preinstalled, third-party penetration tools. While all of these tools could be acquired and installed independently, the organization and implementation that Kali Linux provides makes it a useful tool for any serious penetration tester.



























































